‘UNC4536’ Cybercriminals Spread Malware via Fake Download Sites for Popular Business Software
- An active malvertising campaign targets users who seek popular business software via trojanized installers.
- Cybercriminals attach a malicious PowerShell script to the legitimate software that victims download from fake websites.
- The UNC4536 threat actor is part of a Malware-as-a-Service operation that distributes several malware strains.
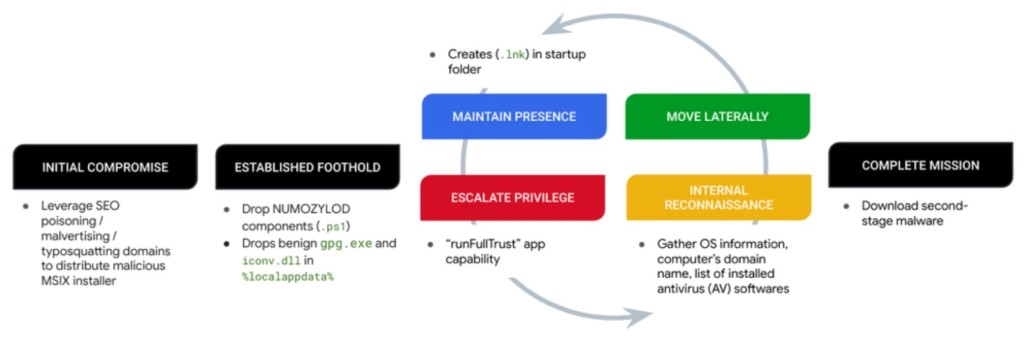
Malvertising campaigns targeting users who search for popular business software, such as Trello, Brave, KeePass, Notion, Steam, and Zoom, deploy a trojanized MSIX installer, covertly bundled and distributed alongside legitimate software, as per a new report from the Mandiant Managed Defense team.
The installer executes a PowerShell script tracked as NUMOZYLOD by Mandiant, which downloads a secondary payload. It is also known as FakeBat, EugenLoader, and PaykLoader, and its distribution is attributed to the UNC4536 threat actor.
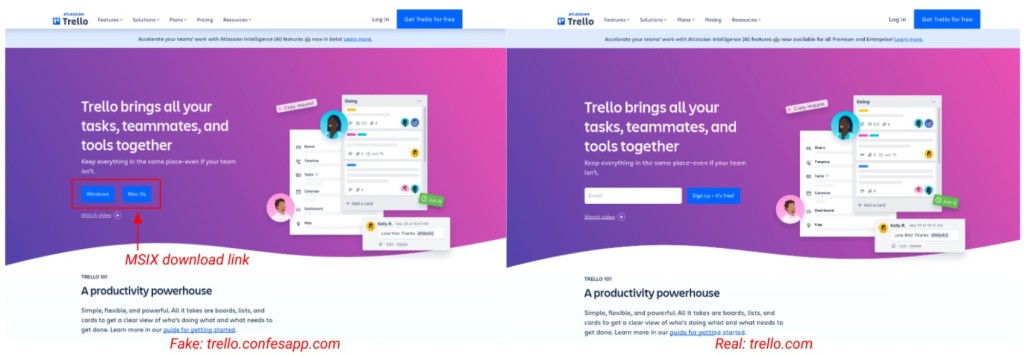
UNC4536 hosts these trojanized MSIX installers on fake websites designed to mimic the legitimate hosting sites of the software they pretend to be.
In the analyzed case, Trello users are targeted by malvertising attacks that redirect them to a fake website.
Once the victim starts installing the seemingly legitimate software, a secondary payload and additional packages hidden within the MSIX installer are downloaded, with the NUMOZYLOD PowerShell payload executed discreetly in the background.
The attackers abuse MSIX features to gain initial access and evade detection since it can execute scripts via the Package Support Framework (PSF), which installers can instruct to run a script before the main application starts and when it finishes by adding configuration items.
The cybercriminals operate under the moniker "eugenfest" and are part of a Malware-as-a-Service (MaaS) operation, distributing malware such as IcedID, RedLine Stealer, Carbanak, Lumma Stealer, or Arechclient2.
In 2023, a NUMOZYLOD downloader was observed to be configured to retrieve the CARBANAK backdoor in trojanized installers hosted on fake download sites for the KeePass open-source password manager as part of a campaign that exploited SEO poisoning tactics.
In another campaign, a heavily obfuscated NUMOZYLOD sample delivered the Lumma Stealer payload.
Recently, a widespread data-stealing campaign lured victims via fake download sites looking like Roblox FPS Unlocker, YouTube, VLC, or KeePass to distribute Trojans that install malicious Web browser extensions.