SystemBC Malware Distributed in New Data Theft Campaign Using Fake IT Calls and AnyDesk
- Cybercriminals were seen deploying a social engineering campaign to distribute data-stealing malware.
- The campaign debuted via email and continued with calls from scammers.
- Their aim was to make the victim install a remote access app in order to compromise their devices.
Threat actors focusing on stealing credentials and other data ultimately deploy SystemBC malware after a carefully crafted social engineering campaign, per a new security report from Rapid7. This campaign is believed to be linked to the Black Basta ransomware group.
The initial lure was an email followed by an attempt to call impacted users, typically via Microsoft Teams, and offer a fake solution that relied on the user downloading and installing the popular remote access tool AnyDesk.
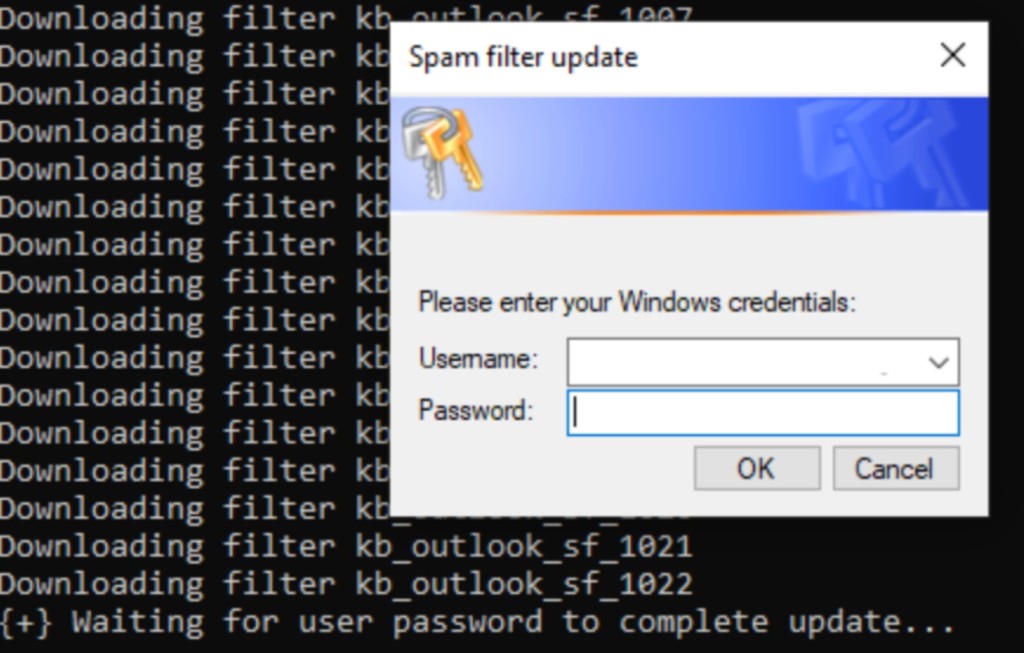
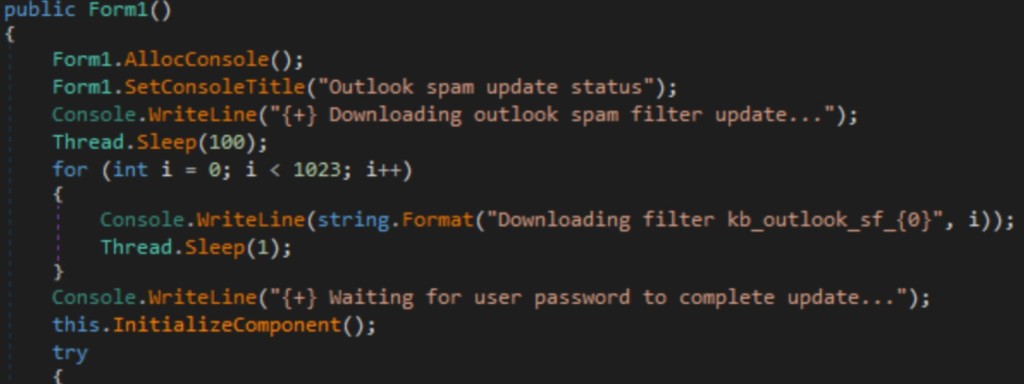
Once the threat actor gained control of the user’s device, they uploaded and executed payloads and exfiltrated stolen data during the initial stages of the attack. In the studied sample, the hackers employed the 32-bit .NET executable “AntiSpam.exe” as a credential harvester.
It required the victim’s Windows credentials under the false pretense of downloading email spam filters. After validation, the entered credentials and system enumeration information were saved to disk.
Several binaries and PowerShell scripts were then executed to attempt connecting to the command and control (C2) servers, including Golang HTTP and Socks beacons and the SystemBC dropper and socks proxy.
Among them was also a Beacon Object File (BOF) converted from a Cobalt Strike module to a standalone executable, and one of the follow-on payloads attempted to exploit the CVE-2022-26923 active directory domain services elevation of privilege flaw to add a machine account for Kerberoasting.
The threat actor also used reverse SSH tunnels and the Level Remote Monitoring and Management (RMM) tool for lateral movement and persistence.
Recently, 12 cybercriminals arrested in Moldova used deepfake ads on Facebook featuring politicians and popular personalities. They promoted fake investments in legitimate companies to lure victims into installing AnyDesk and then accessing their banking accounts remotely to drain users’ accounts.