Seemingly Legitimate Ad for Google Authenticator Distributes Info-Stealing Malware
- A fake ad for the popular Google Authenticator service impersonating Google passed the company’s checks.
- The premise of these attacks relies on social engineering, as the advertisement led to a decoy website with a different URL.
- Unsuspecting victims inadvertently downloaded info-stealing malware instead of the official Authenticator app.
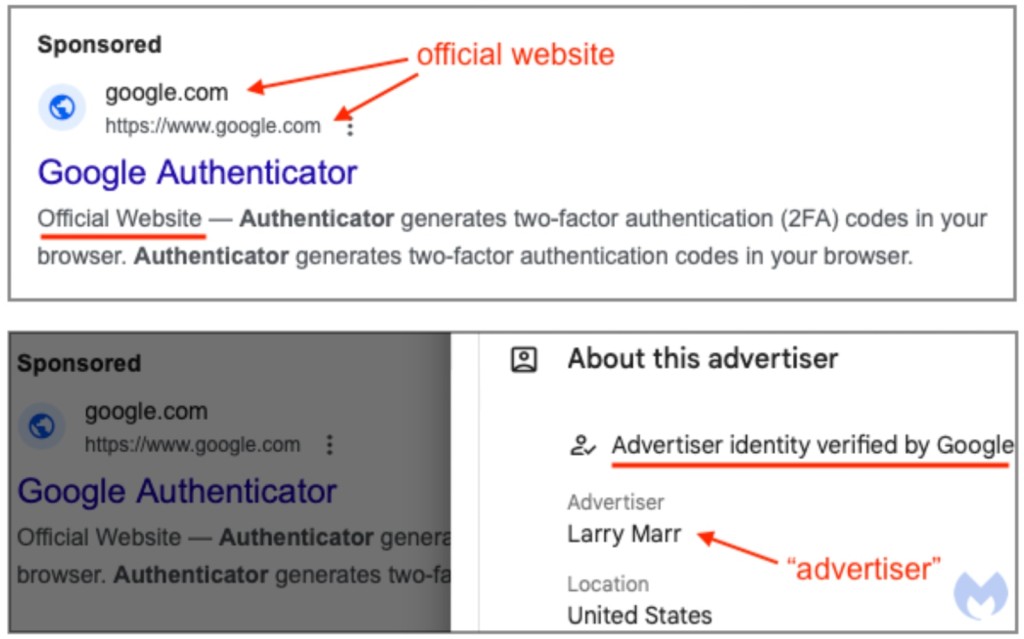
A fake ad for the trusted multi-factor authentication (MFA) app Google Authenticator appearing among Google search results looked as if it was from official sources, and the advertiser’s identity was even verified by Google, a new report from security experts Malwarebytes says.
The advertisement led to a decoy website where people actually downloaded malware.
People who were looking to download the popular MFA service through a Google search in the past few days could see a malicious ad that masterfully impersonated the Aphabet Inc.-owned app. The downloaded executable actually contained an infostealer.
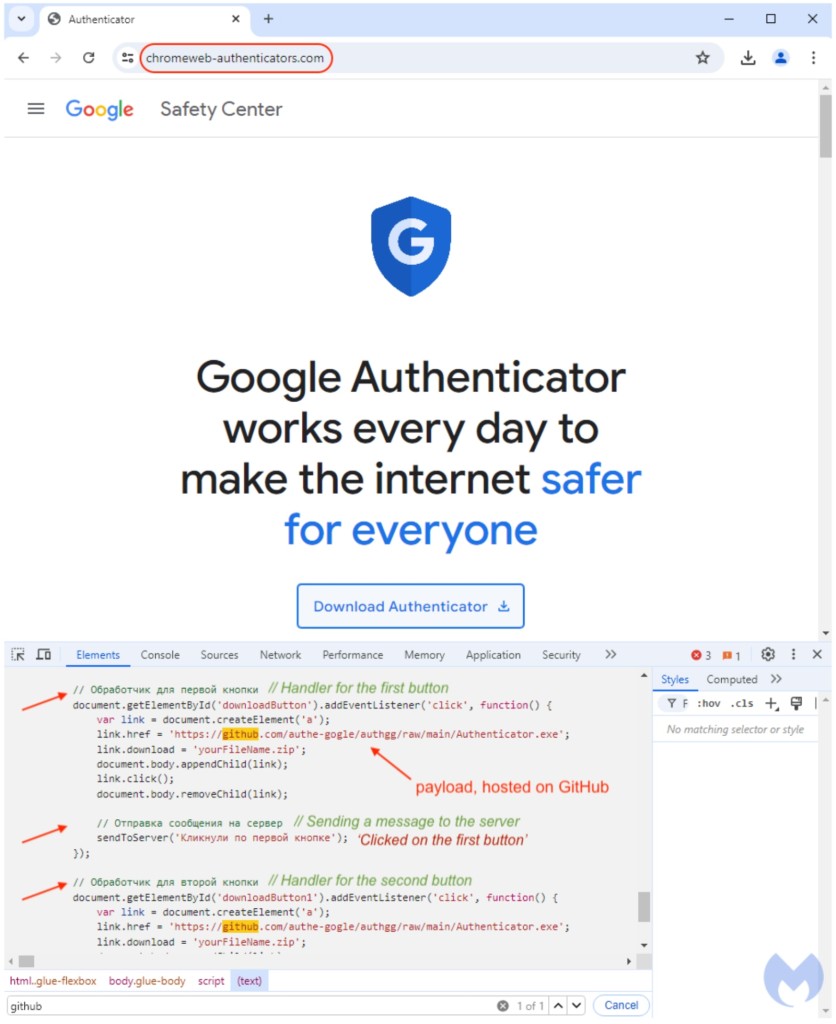
Upon clicking, the user experiences several redirects via intermediary domains controlled by the attacker before landing on a fake site for Authenticator, which leads to a signed payload hosted on GitHub.
Using a trusted cloud resource makes it unlikely to be blocked via conventional means. The threat actor leveraged the fact that anyone can make an account and upload files on GitHub and created the ‘authgg’ repository with the username ‘authe-gogle,’ which contains the malicious Authenticator.exe.
The code that downloads Authenticator.exe from GitHub contains comments from the author in Russian. The file itself has been digitally signed by “Songyuan Meiying Electronic Products Co., Ltd.”
Sandbox maker AnyRun previously reported a similar distribution site and the same payload. Malwarebytes blocked access to the fake Authenticator website and detected the payload as Spyware.DeerStealer.
In the analyzed campaign, the DeerStealer malware could exfiltrate user personal data via an attacker-controlled website hosted at vaniloin[.]fun.
During the past year, various info-stealer malware campaigns that infected victims’ devices got access to their stolen credentials, which were then exfiltrated for financial gains.