Proofpoint Email Protections Exploited for Spoofing Prominent Brands in Massive Phishing Campaign
- Threat actors managed to send millions of emails appearing to come from legitimate brands and companies.
- The large-scale phishing campaign bypassed major security protections using spoofed email addresses.
- Proofpoint’s email protection service was exploited as part of the cybercriminal operation.
A critical in-the-wild exploit of Proofpoint’s email protection service was observed by Guardio Labs, which allowed threat actors to steal funds and credit card details via millions of perfectly spoofed phishing emails impersonating Proofpoint customers. These phishing emails bypassed major security protections using authenticated SPF and DKIM signatures.
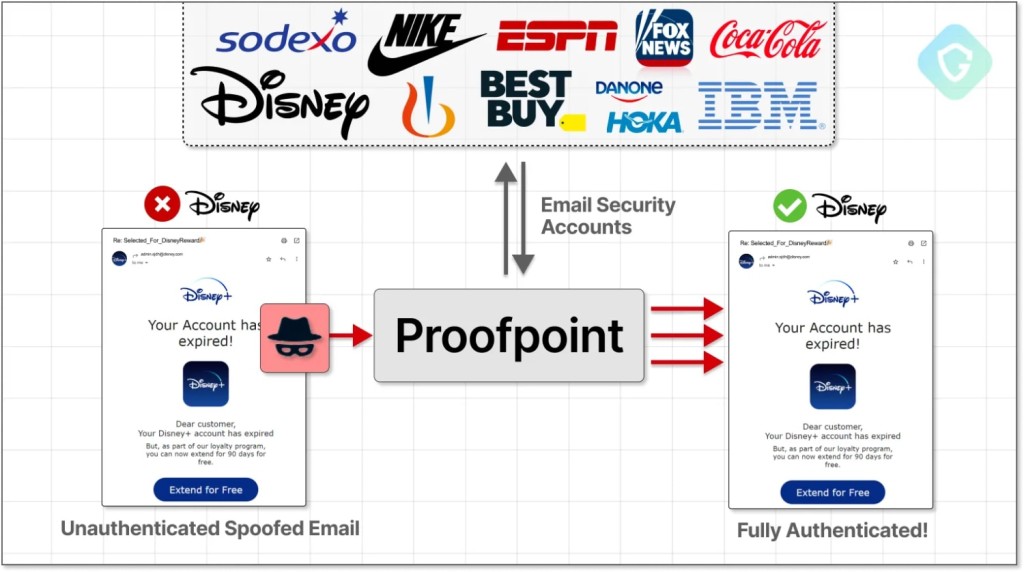
Proofpoint secures 87 of the Fortune 100 companies, and its customer base includes huge companies and brands such as Disney, IBM, Coca-Cola, Nike, Best Buy, and more.
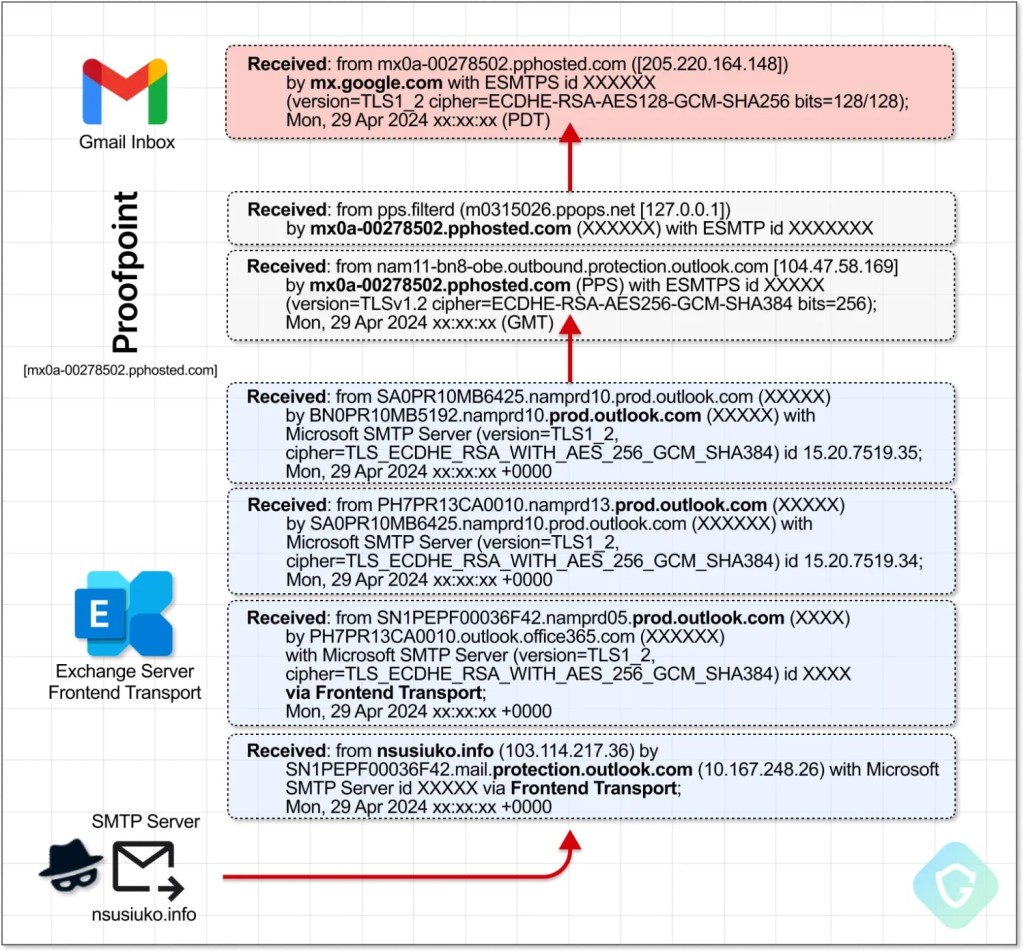
The observed campaign involved the abuse of Microsoft’s Office365 accounts, as the emails’ path started at different SMTP servers on a virtual server, then went to various Office365 Online Exchange servers and then a domain-specific Proofpoint server.
One of the analyzed samples showed that the threat actors sent an email using a spoofed Disney+ account from the authenticated real Disney domain. The email used a free subscription extension for Disney Plus as a lure and contained a button leading to a phishing website.
The fake Disney+ offer presentation mentioned card details were required for verification, but a small font at the bottom of the fake page said a fee would be retained for entering an alleged sweepstakes entry.
The sender addresses cybercriminals used randomly generated a portion of their characters for each email in the campaign, followed by the real disney.com domain and the Disney logo next to it. These authentication and security measures were explicitly built to fight SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail).
Proofpoint Advanced BEC Defense powered by NexusAI is designed to stop email fraud, including payment redirect and supplier invoicing fraud from compromised accounts.
Its customers authorized Proofpoint to send authenticated emails on their behalf by configuring their private DKIM signature key on the Proofpoint service and setting their SPF records on their domain.
Attackers made the Office365 account send an email with spoofed headers that originated from their own controlled SMTP server that Microsoft relays. The Proofpoint outgoing server only accepts approved servers configured in Email Flow, and authentication is not usually required for hosted services like Office 365, which have a single-click configuration.
Any Office365 account can interact with the Proofpoint relay server if no other special rules are manually added later on, and the attackers exploit this misconfiguration flaw. Proofpoint customers get specific hosts to handle authenticated traffic that Disney set on their MX record, publicly available under the DNS protocol.
The security experts said that most operations are initiated with a cluster of VPSs (Virtual Private Servers) mainly hosted on OVH and managed with a legitimate enterprise-grade email delivery software owned by Bird called PowerMTA.
However, signing the phishing emails with the genuine private DKIM key suggests Disney could have suffered a data breach.
This month, a hacktivist group claimed to have leaked roughly 1.2TB of data from Walt Disney over AI concerns. The data, which they reportedly obtained via the company’s internal Slack messages, includes logins, APIs, and more.