Privilege Escalation Vulnerability Impacts Google Cloud Platform’s Cloud Functions Service
- Security researchers discovered a new flaw in Google Cloud Platform services that permits privilege escalation.
- The recently observed vulnerability involves Cloud Functions and the Cloud Build CI/CD pipeline.
- An attacker with access to Cloud Function could escalate the default Cloud Build service account privileges.
A newly discovered flaw in Google Cloud Platform (GCP) affects its Cloud Functions serverless compute service and its Cloud Build CI/CD pipeline service, according to a new report from exposure management firm Tenable. A would-be attacker could leverage excessive user permissions to gain unauthorized access to storage and registries.
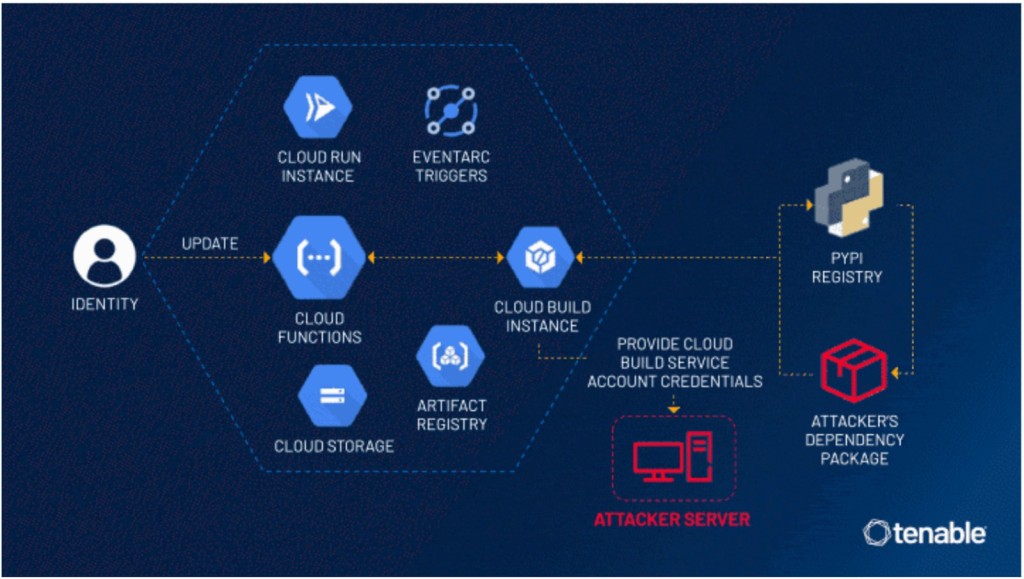
A multi-step backend process is triggered when a GCP Cloud Function is created or updated. As a Cloud Build instance is created for the function’s deployment, a default Cloud Build service account is attached to it, which offers excessive user permissions.
This background process can be exploited by an attacker with access to creating or updating a Cloud Function to escalate account privileges.
Leveraging the default Cloud Build service account’s high privileges in other GCP services that are born with a Cloud Function’s creation or update, an attacker could access Cloud Storage and Artifact or Container Registry, which would permit lateral movement, privilege escalation, and even unauthorized data access end updating or deletion permissions.
GCP remediated the vulnerability for Cloud Build accounts created after mid-June 2024, reducing the severity of the problem for future deployments. Yet, it does not address older existing Cloud Build instances because the account privileges created before the fix was implemented were not changed to support backward compatibility.
The fix did not completely eliminate the issue, considering a Cloud Function still triggers the creation of these GCP services, so the Cloud Build service account needs to have minimum but still relatively broad permissions to deploy the function. GCP can replace the default Cloud Build service account with a least-privilege one for every Cloud Function.
In recent news, some high-end Intel CPU generations were found vulnerable to branch target injection attacks that can manipulate the prediction of indirect branches and precisely redirect sensitive information to a malicious target address.