Spear Phishing Campaigns Target Institutions in Ukraine with HATVIBE and CHERRYSPY Malware
- A scientific research institution in Ukraine was targeted by a spear phishing campaign in July.
- The reported cyberattack deployed the HATVIBE and CHERRYSPY malware via a compromised employee email.
- The attackers used a Microsoft Word attachment with a malicious macro as a lure.
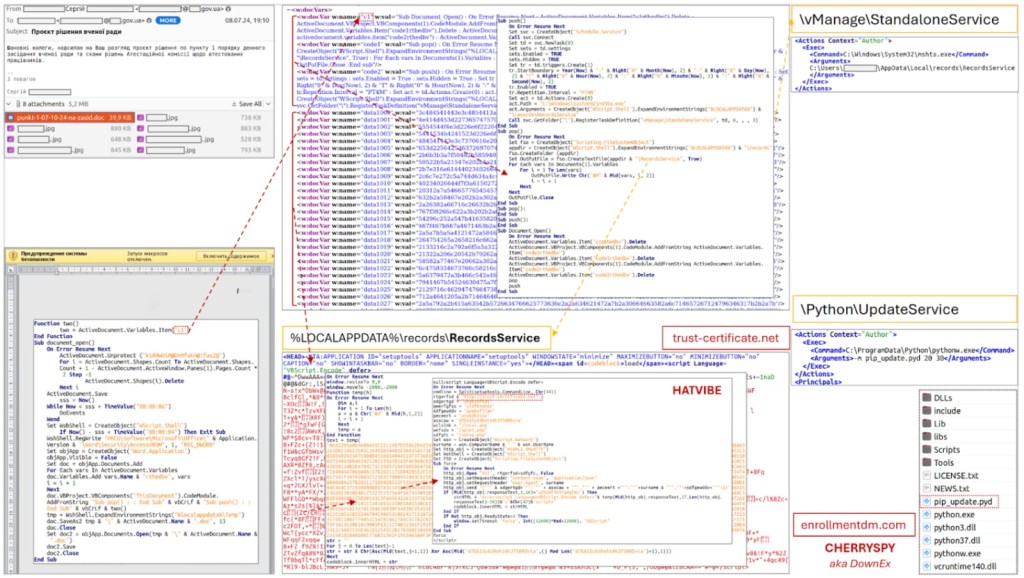
The group tracked as “UAC-0063” carried out a cyber attack on July 8 against one of the Ukrainian scientific research institutions using HATVIBE and CHERRYSPY malware, the Computer Emergency Response Team (CERT-UA) of Ukraine announced on Monday.
CERT-UA said it detected several cases of HATVIBE backdoor installations that exploit a security flaw in the HFS HTTP File Server for initial access, which may be known as the CVE-2024-23692 vulnerability.
The initial attack was carried out via a compromised email account belonging to an institution employee. The account was used to send a macro-laced Microsoft Word (DOCX) attachment to dozens of recipients, including the sender, making it look like a copy of a legitimate previously sent document.
Opening the malicious DOCX file and enabling macros eventually led to the creation of an encoded HTML Application (HTA) file called HATVIBE. Then, the CHERRYSPY Python backdoor was planted, which can execute commands and communicate with a command and control (C2) server.
CHERRYSPY was downloaded to the "C:\ProgramData\Python" directory and compiled into a PYD (DLL) file.
The organization mentioned the lack of two-factor authentication (2FA) for an email account with admin rights and no policies to block the ability to run macros, mshta.exe, and more are to blame for this cyberattack.
The UAC-0063 threat actor was previously observed targeting various government entities to gather sensitive information using keyloggers and backdoors, and CERT-UA believes the group could be associated with the activity of the Russia-backed APT28 group (UAC-0001).
Virustotal detected a DOCX file with a similar macro that was downloaded from Armenia on July 16 containing a lure for the Ministry of Defense of the Republic of Armenia pretending to come from its correspondent in the Kyrgyz Republic, CERT-UA said.
This month, the Chinese APT17 cybercriminal group directed its 9002 RAT against companies and government entities in Italy, employing malicious URLs to download a custom Skype for Business MSI package that harbored malware.