Chinese APT17 Group Targets Italian Companies and Govt Entities with Malware
- The Chinese APT17 cybercriminal group was seen directing its 9002 RAT against companies and government entities in Italy.
- Two observed campaigns used malicious URLs to download a custom Skype for Business MSI package that harbored malware.
- The threat actors sometimes used a seemingly legit Italian government website as a landing page.
A China-linked threat actor called APT17 was seen targeting Italian companies and government entities with a variant of the 9002 RAT malware, aka Hydraq and McRAT, in diskless mode. The RAT was distributed via an email campaign using malicious URLs in the email body or attached MS Office documents.
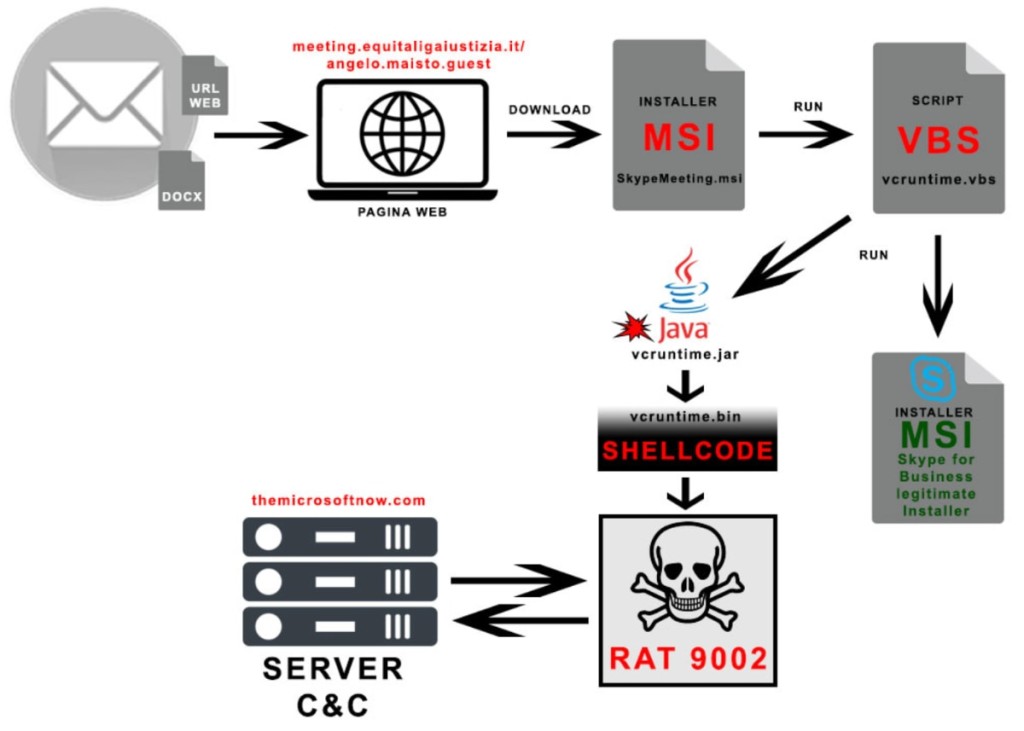
The first targeted attack occurred on June 24, and the second on July 2, 2024. Both campaigns downloaded a seemingly legit, customized Microsoft Software Installer (MSI) package for Skype for Business via a link. The malicious URL led to an attacker-controlled domain that impersonated an Italian government website.
The custom MSI installed the basic Skype app and executed a Java app via a VBS script that contained a shellcode encrypted with RC4, which decompressed and executed the Remote Access Trojan (RAT).
9002 RAT then communicates with the attacker’s command and control server (C2) hosted on a domain that simulates a Microsoft domain, shows network discovery abilities, performs proxy functions to monitor network traffic, downloads additional diskless plugins that can add various features to the malware.
The variant of RAT 9002 analyzed contains an old value indicator, which shows that it continues to be actively developed in 2024.
RAT 9002 and other variants named RAT 3102 are notoriously linked to APT17, which was linked to Operations DeputyDog and Ephemeral Hydra due to exploiting zero-days Microsoft's Internet Explorer and targeting Japan and other countries.
The Chinese APT17 cyber-criminal group – also dubbed Aurora Panda, Bronze Keystone, Dogfish, Elderwood, Helium, Hidden Lynx, and TEMP.Avengers – is known for targeted attacks on companies and government entities.
RATs were lately seen distributed via various pirated software, including cracked versions of legitimate programs Microsoft Office and Windows downloaded from torrent websites.