New EstateRansomware Group Abuses Now-Patched Veeam Backup Software Flaw
- A new ransomware group known as EstateRansomware has been observed leveraging a now-patched flaw.
- The security vulnerability in Veeam Backup & Replication software permits access to encrypted credentials.
- The attack seemed rather oriented toward harvesting credentials and exploiting Backup & Replication flaws.
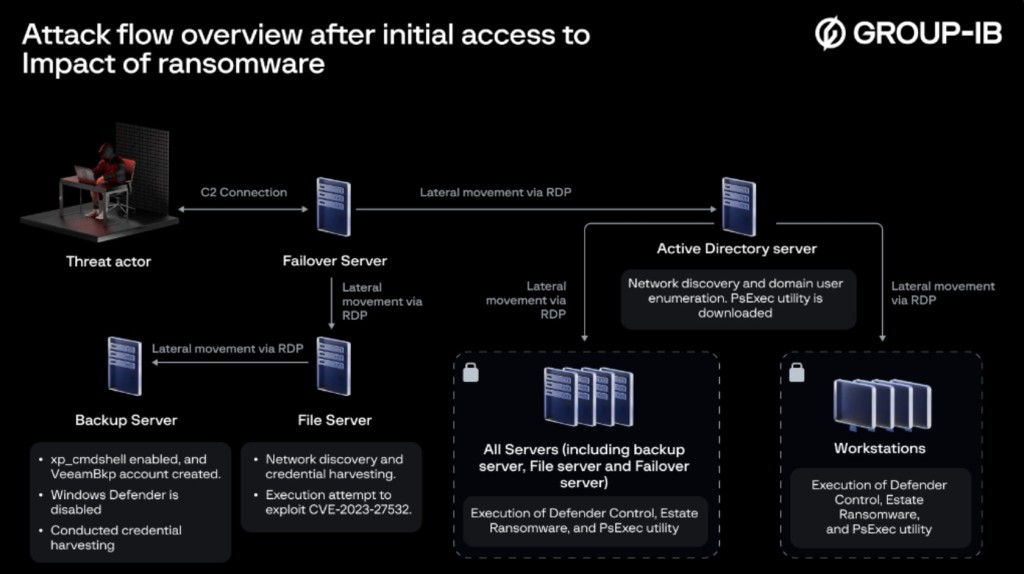
A novel ransomware operation known as EstateRansomware exploits a now-patched vulnerability in the Veeam Backup & Replication software, as reported by the Group-IB security experts, who discovered this threat actor in early April 2024.
The cybercriminals were observed exploiting CVE-2023-27532 in their attacks, which allows unauthorized third parties to obtain encrypted credentials stored in the configuration database.
The aim was to enable an SQL server-stored procedure that allows the execution of Windows shell commands and create a rogue user account to conduct network discovery, enumeration, and credential harvesting activities via tools like NetScan, AdFind, and NirSoft, as per the report.
The attack leveraged the SSL VPN service dormant account to move laterally from the FortiGate Firewall to the failover server. EstateRansomware deployed a persistent backdoor on the failover server and conducted lateral movement via the Remote Desktop Protocol (RDP).
The security researchers say they noticed VPN brute-force attempts via a dormant account in April 2024, and the hackers managed to log into the same VPN account several days later successfully.
According to the security report, the actor’s primary focus seemed to be harvesting credentials and exploiting vulnerabilities in the Veeam Backup & Replication software. The attackers managed to permanently disable Windows Defender using Defender Control, which permitted ransomware deployment and execution.
The Arctic Wolf Incident Response reported on a new ransomware operation called Fog in early May. This variant targeted US organizations, 80% of which were in the education sector, accessing victim environments via credentials from breached VPNs.
Fog ransomware threat actors wanted to quickly encrypt VM storage data and obtain a fast payout to decrypt that data. They used administrator accounts to establish RDP connections to Windows Servers running Hyper-V and Veeam and facilitated lateral movement through credential stuffing.