Threat Actor ‘Velvet Ant’ Exploits F5 Load Balancers for Persistence in the Target Systems
- Velvet Ant was seen compromising Internet-exposed legacy F5 BIG-IP appliances.
- One of their campaign’s goals was to maintain access to the target network for espionage.
- The cybercriminal group infiltrated critical systems to obtain access to sensitive data.
A cybercriminal group tracked as Velvet Ant achieved remarkable persistence within the environment of one victim company, leveraging legacy F5 BIG-IP appliances that were exposed to the Internet through an internal Command and Control (C&C) server, as per a Sygnia report. The threat actor hijacked execution flow via DLL search order hijacking, Phantom DLL loading, and DLL sideloading.
The report focuses on a sophisticated cyber attack targeting a large organization for espionage. The attack exploited various entry points across the victim’s network infrastructure to deploy malware. It was discovered in late 2023 after lingering in the organization’s on-premises network for about three years.
After the cybersecurity company proceeded with eradication, the threat actors focused on legacy operating systems, targeting Windows Server 2003 systems without Endpoint Detection and Response (EDR) and with limited logging. They achieved persistence by activating previously unused malware in the victim environment – the well-known Remote Access Trojan (RAT) PlugX, which has been used by multiple Chinese state-sponsored groups since 2008.
PlugX has a modular plugin system based on the Windows SDK ‘OLE/COM Object Viewer‘ executable, and the cybercriminals hijacked its DLL search order to load the malicious PlugX DLL, which, in turn, loads the malicious payload, even tampering with the EDR product before installing PlugX.
Lateral movement and remote code execution were facilitated by Impacket, an open-source collection of Python classes, via the native Windows Management Instrumentation (WMI).
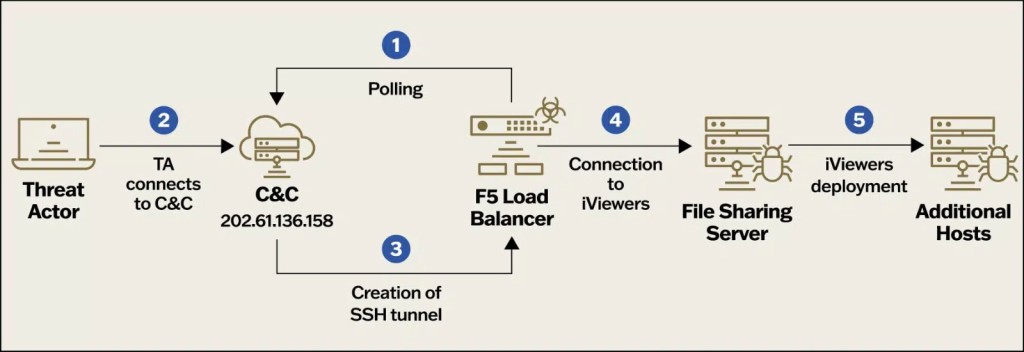
Velvet Ant can return after eradication by infecting new systems and deploying a reconfigured PlugX. They directed traffic through an internal file server used as C&C, which helped blend in with legitimate internal network traffic.
PlugX created a local firewall rule on compromised endpoints and listened on a high, random port number. Security specialists identified an internal IP address of an F5 load balancer communicating with it on the same port, but the appliance was not supposed to be operational in the production network.
F5 BIG-IP appliances are trusted within the network architecture, and once compromised, these enable attackers to use a hidden backdoor to evade detection from traditional log monitoring solutions.
The target organization had two compromised F5 BIG-IP appliances running an outdated, vulnerable operating system. These appliances were directly exposed to the Internet while handling firewalls, WAF, load balancing, and local traffic management. These were not protected by the main corporate firewall, so they revealed a reverse SSH tunnel connection to the same C&C IP address that was previously blocked on the corporate firewalls.