Cybercriminal Gang UNC3944 Runs VMs Inside Victims’ Infrastructure via vSphere and Azure
- UNC3944 has reoriented from ransomware to targeting SaaS applications.
- The threat actor suspected to be behind the Snowflake security incidents attacks Azure and vSphere to run VMs.
- On occasion, they used fearmongering tactics to gain access to victim credentials.
UNC3944 started including data theft from software-as-a-service (SaaS) apps to attacker-owned cloud storage objects and lateral movement via SaaS permissions abuse using tools, services, and support from underground communities like Telegram, as observed by incident response firm Mandiant.
UNC3944 also uses persistence mechanisms against virtualization platforms, accessing vSphere and Azure using stolen credentials on single sign-on (SSO) apps to create new virtual machines (VMs). They also used exposed login details to access apps like vCenter, CyberArk, SalesForce, Azure, CrowdStrike, GCP, and Amazon Web Services (AWS).
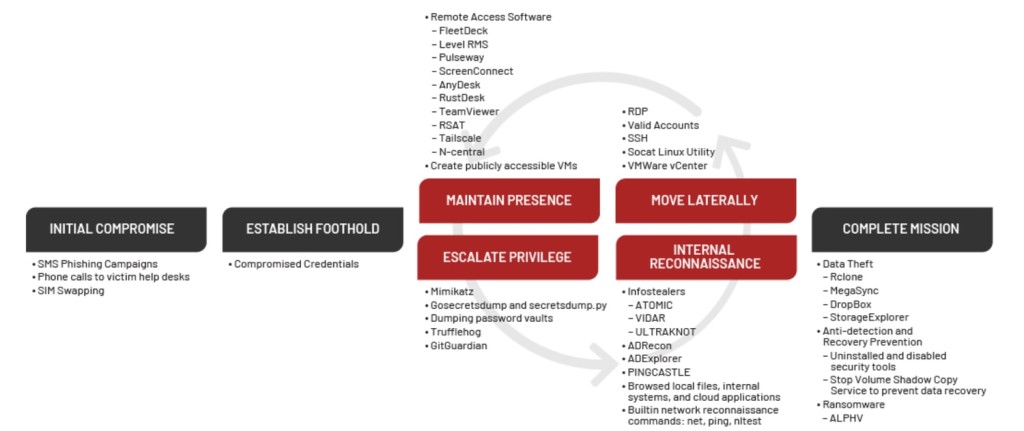
Initially focusing on credential harvesting and SIM-swapping attacks, then moving to ransomware and data theft extortion, UNC3944 has now remained with the latter alone, expanding its targeted industries and organizations. They occasionally get victim credentials via fearmongering tactics, which include threats of physical harm to victims and their families, doxxing personal information, and distributing compromising materials.
UNC3944 operators used personally identifiable information (PII) already in their possession to bypass help desk administrators' user identity verification, as observed in multiple engagements leveraging social engineering techniques to gain initial access to existing privileged accounts. For instance, they often called pretending the victims were receiving a new phone to warrant a multi-factor authentication (MFA) reset.
UNC3944 exploited legitimate third-party tools to gain remote access to compromised environments. The group conducted internal reconnaissance of Microsoft applications, such as SharePoint, frequently targeting internal help guides and documentation for virtual private networks (VPNs), virtual desktop infrastructure (VDIs), and remote telework utilities on victims' SharePoint sites.
Privilege escalation via authentication service Okta abuse techniques enabled UNC3944 members to go beyond on-premises infrastructure to Cloud and SaaS applications, exploiting applications with Okta single sign-on (SSO) and using the Okta web portal to see what application tiles were available.
However, the cyber threat group employed a more aggressive persistence method by accessing vSphere and Azure using SSO apps to create new VMs, which occurred via abuse of administrative groups or administrator permissions. They then used publicly available utilities such as MAS_AIO and privacy-script.bat to make the new VM remove default Microsoft Defender protections and some Windows telemetry helping forensic investigation.
Additionally, a lack of endpoint monitoring allowed the group to download Python libraries, such as IMPACKET, tools like Mimikatz and ADRecon, and various covert tunneling tools, such as NGROK, RSOCX, and Localtonet to access the device without a VPN or MFA.
The threat actors attached an optical disc image file (ISO) called PCUnlocker to existing VMs through the vCenter appliance to bypass authentication controls, resetting local administrator passwords.
The group’s main objective seems to be to discover key infrastructure and potential exfiltration targets, using these VMs to exfiltrate data to high-reputation resources such as Google Cloud Platform (GCP) and AWS.
UNC3944 is a financially motivated threat group that significantly overlaps with public reporting of "0ktapus," "Octo Tempest," "Scatter Swine," and "Scattered Spider." It was connected to the data theft incident affecting approximately 165 Snowflake customers.