Cylance Confirms Data Breach Connected to Unnamed Third-Party Service
- A threat actor took to the Dark Web to advertise selling a huge database stolen from Cylance.
- The cybersecurity company has confirmed the data breach but dismissed it as old data.
- The security incident allegedly occurred via a yet unnamed third-party platform.
Cybersecurity company Cylance confirmed the legitimacy of a trove of data currently sold on a hacking forum but said the access point was a third-party service that has not been named. BlackBerry Cylance says the hacker owns old marketing data from a previous third-party data breach dating from before BlackBerry acquired Cylance.
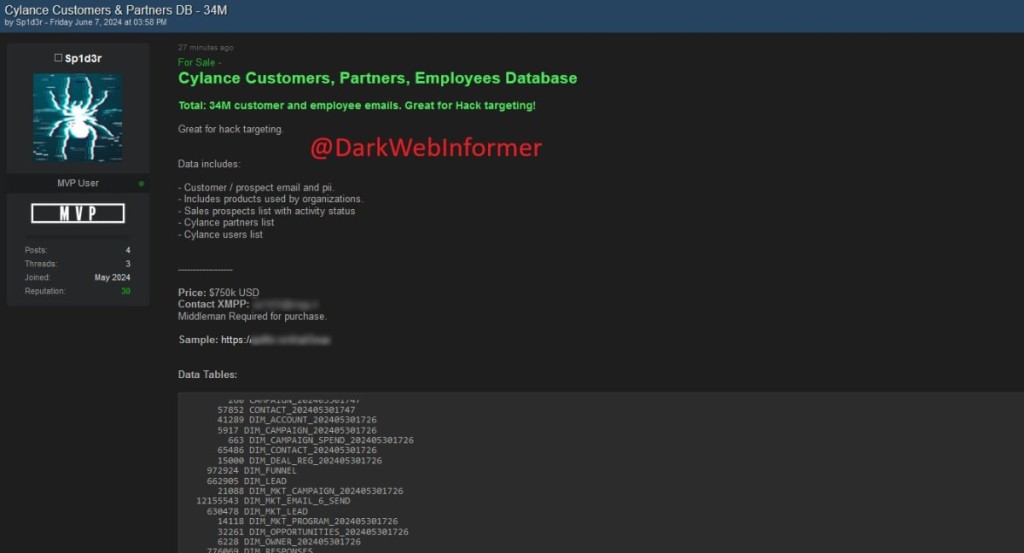
A threat actor known as Sp1d3r is allegedly selling data belonging to Cylance customers, partners, and employees for $750,000. Data includes 34 million customer, prospect, and employee emails, Cylance partners and users lists, customer and email and personally identifiable information, products used by organizations, and sales prospects lists complete with activity status.
BlackBerry Cylance is investigating the threat actor's claims, stating: “Based on our investigation to date, we do not believe that BlackBerry data and systems related to our customers, products, and operations have been compromised.”
The statement mentions current Cylance customers are not impacted, and no sensitive information is involved, while “the data in question was accessed from a third-party platform unrelated to BlackBerry and appears to be from 2015-2018, predating BlackBerry’s acquisition of the Cylance product portfolio.”
However, the same threat actor is also selling an alleged 3TB of data from automotive aftermarket parts provider Advance Auto Parts obtained from a breach of the company's Snowflake account – and Cylance is also a Snowflake customer, which may be an indicator of who the unnamed third party is.
The number of affected companies using Snowflake environments hasn’t been disclosed until now. However, incident response firm Mandiant says approximately 165 companies may have had their data stolen through the use of leaked credentials of Snowflake customer accounts without multi-factor authentication (MFA) exposed via several info-stealer malware variants.