Clusters of Chinese State-Sponsored Threat Activity Found Targeting Southeast Asian Government
- Security software and hardware company Sophos discovered cyber espionage threat clusters targeting a government agency.
- Actors attempted to collect intelligence documents, infrastructure architecture data, and credentials.
- These activity clusters may be part of a coordinated campaign under the direction of a single organization.
Sophos cybersecurity researchers have discovered new threat activities involving malware that are backed by the Chinese state and target a government agency in Southeast Asia for cyber espionage, as the actors tried to access intelligence documents. The campaign, which they have named “Crimson Palace,” has precursors dating back to early 2022. MDR also discovered previously unreported malware and improved variants of previously reported ones.
The discovery of a DLL sideloading technique that exploited a VMware component, VMNat.exe, led the Sophos Managed Detection and Response (MDR) to unveil the complex, long-running Chinese state-sponsored cyberespionage operation in May 2023. The campaign targeted a high-profile government organization for cyberespionage in Southeast Asia.
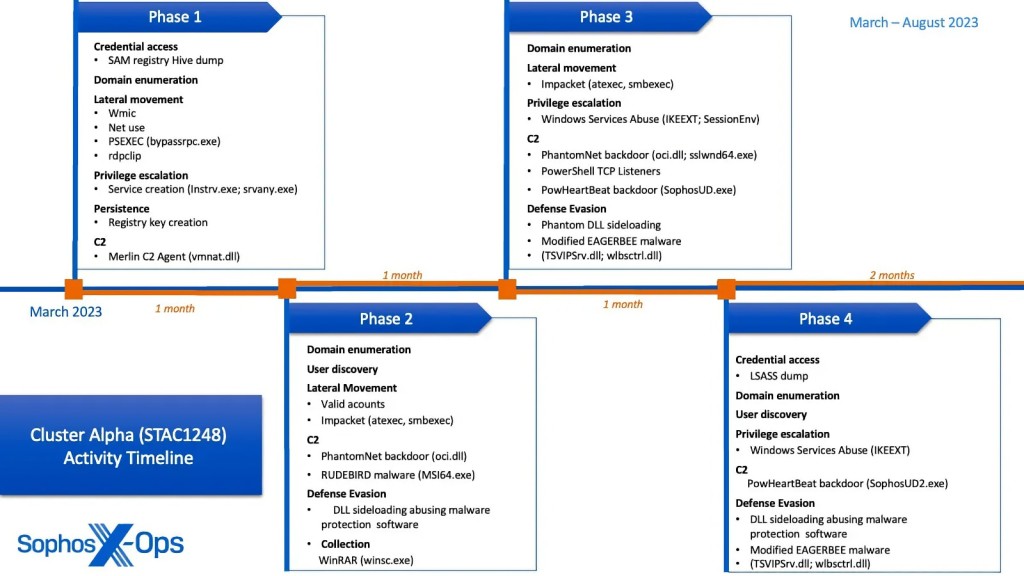
Observed malware variants include NUPAKAGE, Merlin C2 Agent, Cobalt Strike, PhantomNet backdoor, RUDEBIRD malware, and the PowHeartBeat backdoor. The use of previously unreported malware PocoProxy and CCoreDoor (concurrently discovered by BitDefender) was also identified, as well as an updated variant of EAGERBEE malware, which showed new capabilities to discard the targeted organization’s network communications to anti-virus (AV).
The threat actors leveraged many novel evasion techniques. The Crimson Palace campaign included over 15 distinct dynamic link library (DLL) sideloading scenarios abusing Windows services, legitimate Microsoft binaries, and AV – even overwriting DLL in memory to remove the Sophos AV agent process from the kernel.
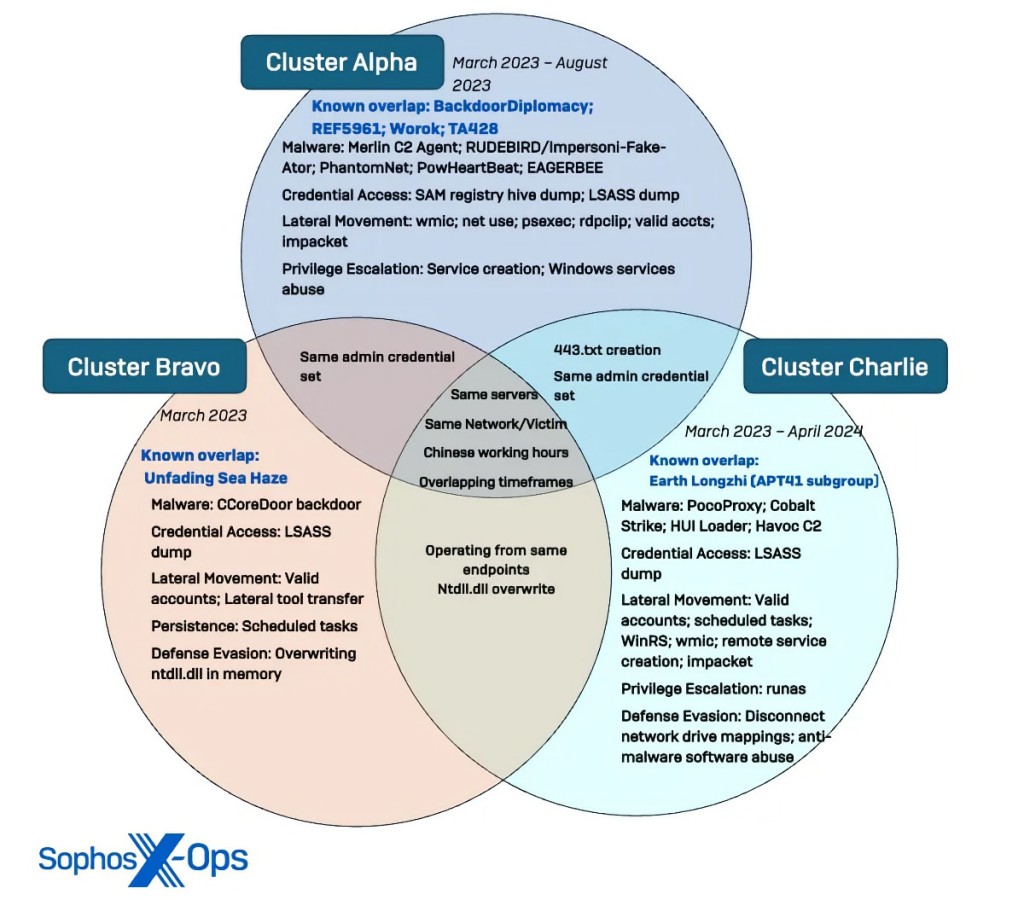
The Sophos researchers found Cluster Alpha (STAC1248), Cluster Bravo (STAC1807), and Cluster Charlie (STAC1305) showing intrusion activity from March to December 2023. They used tools and infrastructure similar to Chinese threat actors BackdoorDiplomacy, REF5961, Worok, TA428, Unfading Sea Haze, and the APT41 subgroup Earth Longzhi, which were publicly reported by other researchers.
Appearing to highly prioritize access management, Cluster Charlie deployed multiple implants of PocoProxy to establish persistence on infected systems and rotate to new external C2 infrastructure, with the longest activity in the target network – from March to at least April 2024.
Cluster Charlie focused on collecting and exfiltrating a large volume of sensitive military and political files, data on infrastructure architecture, credentials/tokens to gain in-depth access, and more.
The cybersecurity researchers believe accessing critical IT systems, reconnaissance of specific users, sensitive military and technical information, and deploying various malware implants for C2 communications suggested the overall goal behind the campaign was to “maintain access to the target network for cyberespionage in support of Chinese state interests.”
The timing of operations, the overlaps, and the objectives suggest there is at least some level of awareness and/or coordination between the clusters, MDR says.