New Android Trojan Targeted at PayPal App is Stealing Money in Seconds
- Malware running on the background to steal PayPal money after the user logs in the account
- The trojan also dubs as a phishing tool to maximize the exploitation period
- Google Play is getting more and more ridden by banking trojans
ESET researchers have discovered a new type of Android Trojan which combines advanced functionality features that allows it to draw money from Android PayPal accounts in seconds. The last known “disguise” of the trojan is a battery optimization tool that belongs to a popular category of applications in general and is by definition targeted to less tech-savvy users.
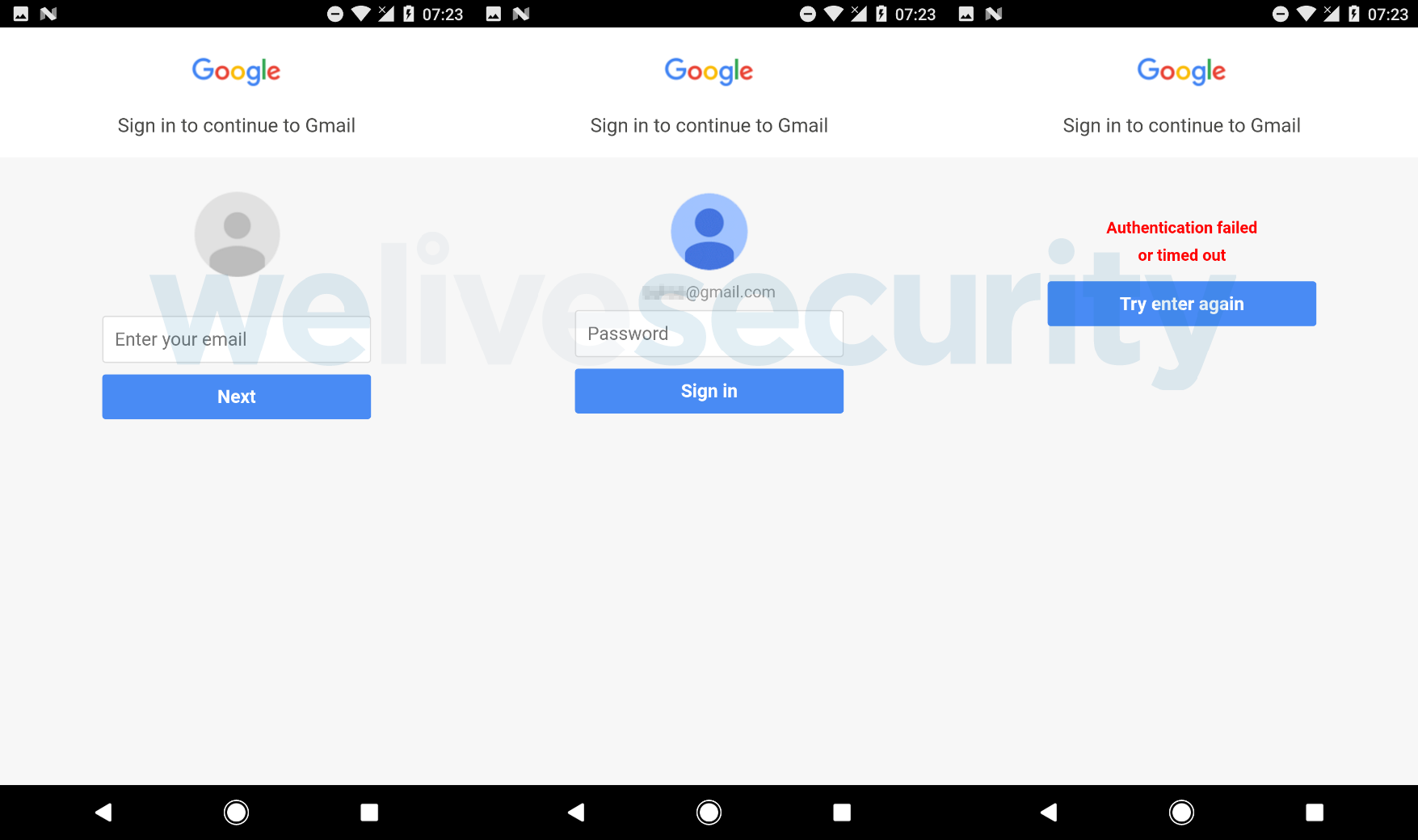
Once launched, the trojan is asking for the user’s permission to “enable statistics” through the usual permission granting screen that many people just access without too much consideration. If accepted, and if the PayPal app is installed on the device, the malware displays a popup notification to launch it. With the malware running on the background, the user logs in the PayPal account as usual and follows the two-step authentication process as well if enabled. When the login procedure is completed, the malware proceeds immediately to sending large amounts of money to the attacker’s PayPal address, and with the action taking place in just 5 seconds, it is quite hard for the user to suspect something is fishy and take action to prevent it.
It is notable that the malware does not target the acquisition of passwords and login credentials, as it lets the user do this work for it. During the analysis of the ESET researchers, the malware attempted to transfer 1000 Euros, but it may be set to incrementally reduce this depending on the available funds. If no funds are available in the PayPal balance, or if no payment cards are connected to the account, then the malware fails to act. However, and as the malicious trojan is activated every time the PayPal app is launched, it re-runs its checks on the user’s account and may steal money if made available on the future.
However, this is not the only weapon in this malware’s arsenal, as it also features phishing techniques. More specifically, it downloads HTML-based overlay screens for legitimate platforms such as Google Play, Viber, Skype, and Gmail, asking for credit card details and login credentials. The attackers have possibly implemented this functionality in order to gain access to the users’ email accounts and delete the transaction emails before the user notices the inexplicable withdrawals. This can potentially extend the exploitation period and maximize the gains for the attacker. The overlays do not go away unless the user fills out the forms, utilizing the “locked foreground screen” function, but of course, that doesn’t mean that the form must be filled with legitimate credentials.
Image source: welivesecurity.com
Unfortunately, Google Play seems to be filled to the brim with similar apps nowadays, with Malware authors constantly developing their techniques and hiding their software under the coverage of battery managers and device boosters. ESET has uncovered 29 of them between August and October, with the trend showing an increasing reliance on mimicking legitimate financial institutions as faithfully as possible.
Are you a PayPal Android app user? Have you ever installed bogus battery and system management apps? Let us know of your experience in the comments section below, and don’t forget to join the relevant discussions on our social pages on Facebook and Twitter as well.