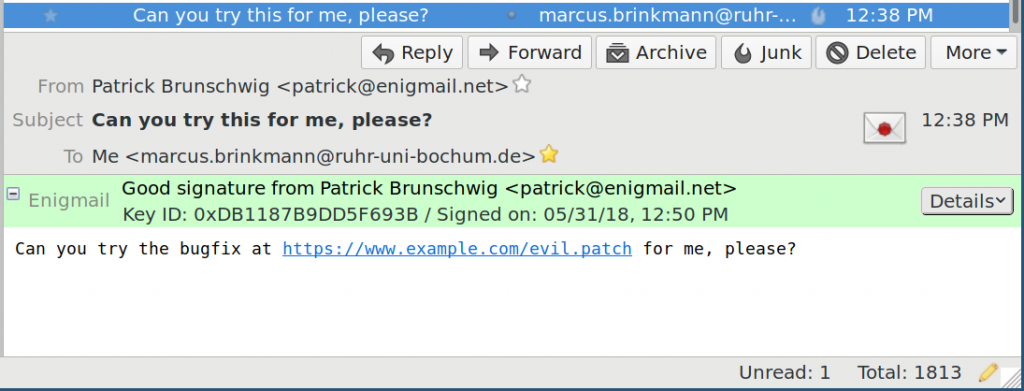
SigSpoof Vulnerability Found in Most Email Encryption Tools
- A researcher revealed on Wednesday that most of the widely used email encryption tools were vulnerable to digital signature spoofing.
- The researcher notified email providers who have already patched their encryption tools, and users should be safe.
- Among the affected encryption tools GPGTools, GnuPG, Enigmail, and python-GnuPG have said to be affected for decades.
Some of the most popular email encryption tools were discovered to be vulnerable. The vulnerability dubbed SigSpoof allowed hackers to spoof email signatures of any person who owns a public email key. The discovery of SigSpoof was made by Marcus Brinkman, a software developer who has already notified email providers and patches have already been pushed out to safeguard email users. Among the encryption tools affected by SigSpoof, GPGTools, GnuPG, Enigmail, and python-GnuPG have already been updated to patch the vulnerability. Similar vulnerabilities were found in Enigmail and Simple Password which required multiple patches for spoofing bugs.
The vulnerability could allow decades of email messages and sensitive files to be spoofed and stolen, and it is likely that the tool could be used beyond the realm of email. The exploit can be used for potentially accessing secure backups and tamper with software updates to email services as well in some cases. The extent of the usage of SigSpoof is unknown as the exploit cannot be detected as malicious without forensic analysis.
Image Courtesy of Marcus Brinkman
According to Brinkman, the attacks are very simple and can be used in platforms like Apple Mail and Thunderbird to show fake emails from anyone with a public email key. The oldest instances of the vulnerability date back to 1998, in GnuPG v0.2.2. Despite updates over the decades, the vulnerability was not discovered or patched by security experts. Brinkman released a publicly available fix to the vulnerability, and its Git repository is available to the public. It is recommended to email users that they back up their email messages and files to a local computer to avoid the risk of losing data.
This is the second instance of a critical email vulnerability being found in 2018. An encryption vulnerability was found earlier this year that made it possible for emails encrypted with S/MIME or PGP in popular email programs like Apple Mail, Thunderbird, and Microsoft Outlook.