Amazon SES Token Stolen From Kaspersky Used in Phishing Campaign Targeting Office 365 Users
- Kaspersky discovered its Amazon Simple Email Service (SES) was being used by hackers in an Office 365 phishing campaign.
- The actors did not impersonate Kaspersky, but rather chose to go with a missed fax notification disguise.
- The cyberattack did not lead to any breaches on servers and databases routing the emails.
A recent discovery by Kaspersky revealed phishing scammers using one of its legitimate Amazon Simple Email Service (SES) tokens issued to third-party contractors to target Office 365 users. The Kaspersky team also found several cybercriminals using this token in their phishing attempts using kits like Iamtheboss and MIRCBOOT.
SES allows developers to send emails via any linked app for various purposes, such as marketing and mass email communications. The team also said that the token in question was issued to a third-party contractor while testing for the website "2050.earth" and it's now revoked for its use in malicious activities. The cyberattack did not actually lead to any server or database breach on the "2050.earth" website and related services.
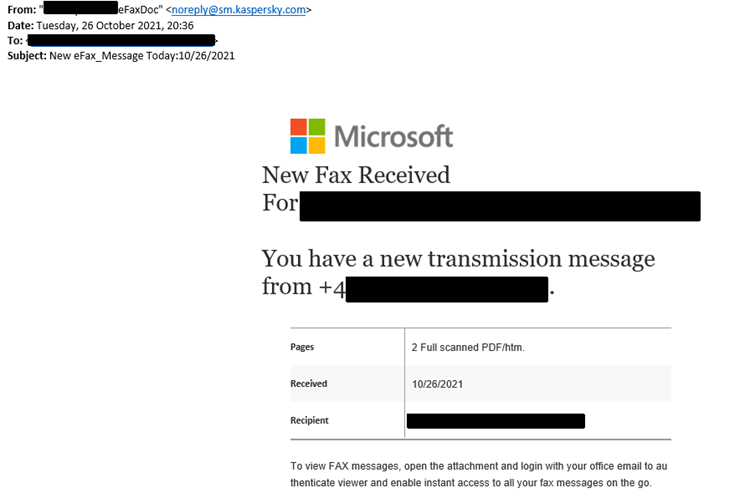
The attackers masked their phishing messages as missed fax notifications, redirecting potential victims to phishing landing pages used for making Microsoft Office 365 users give up their credentials. These emails had multiple sender addresses, including "[email protected]."
While they did not directly use fake Kaspersky emails, they were using official Kaspersky emails and sent via Amazon Web Services to avoid Secure Email Gateway (SEGs) and get to intended targets. Kaspersky recommended users keep vigilant against phishing emails even if sent through verified domains.
In September, Microsoft’s investigators discovered a massive phishing campaign featuring 300,000 unique subdomains and over 100 phishing templates made to mimic known brands and services as part of a “phishing-as-a-service” (PhaaS) operation called ‘BulletProofLink’ (aka ‘Anthrax’).