Researchers Discover Remotely Exploitable Flaw that Results in File Exposure on Gurock TestRail
- An information disclosure vulnerability on Gurock TestRail could expose very sensitive files and data.
- The particular product is used by government entities and leading organizations in the United States.
- The researchers who figured it out have alerted the software vendor but got no response.
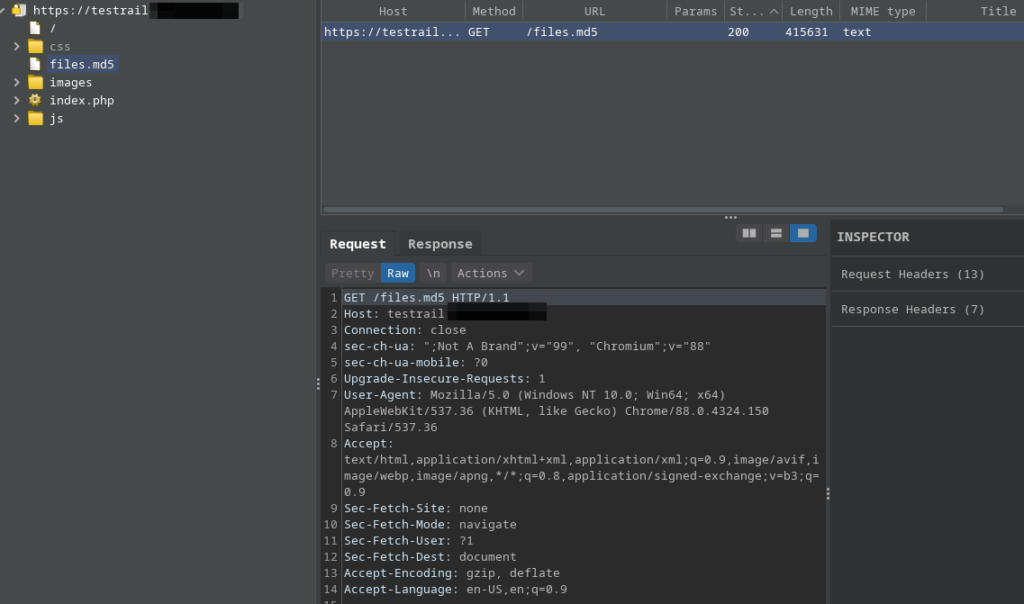
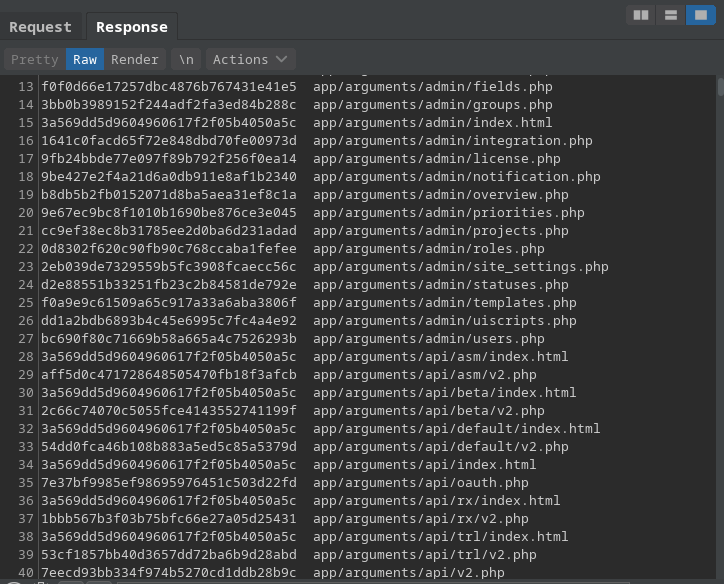
Researchers John Jackson and “SickCodes” have discovered and figured a way to remotely exploit “CVE-2021-40875”, a client-side vulnerability in Gurock TestRail versions 7.2.0.3014 and older, which results in file exposure. As detailed in the technical report, a threat actor may access the ‘/files.md5’ file on the client app and get a full list of app files and file paths. Then, the paths can be tested, oftentimes leading to the disclosure of sensitive information like hardcoded credentials, API keys, etc.
TestRail is a centralized software testing and management platform to control, track, and organize software testing efforts. It features bug tracker integration, powerful reports, and metrics and can be scaled or customized according to the client’s needs.
It’s used by government agencies and organizations like NASA, as well as companies like Cisco, Salesforce, Paypal, eBay, HP, Autodesk, Adobe, Amazon, Sony, Intel, Apple, FedEx, etc.
After accessing the file paths and testing a couple of them, the researchers got mixed results, with some working and others returning an “access forbidden” error. The next step would be to develop a custom Python script that would automate this process and determine what is actually within reach. The finalized bash script tool is now published and available for download on GitHub.
The reason why using the script to grab a custom list of files and then evaluate the results is preferable to using a list of sensitive files is that TestRail uses custom files that may be interesting but missed by standard lists. The parsing can be done manually or automatically, depending on how much control over what gets downloaded the tester wants to achieve.
The researchers reported the problem to Gurock nine days ago after accessing a couple of very worrying examples of sensitive credentials. The root cause of this flaw is an access control restriction, but securing the files.md5 path from public scrutiny would be effective mitigation.
However, the product vendor hasn’t responded with any messages and didn’t acknowledge the reception of the report, so the researchers decided to go ahead with the publication of the flaw. Of course, some things have been omitted since the issue remains unpatched.
Sick.Codes has told us the following: