APT-C-23 Using New Android Spyware in the Middle East
- The APT-C-23 group of actors is now using a novel spyware for their Middle East operations.
- The spyware mimics Telegram only to the point that is needed for the granting of permission requests.
- The malicious abilities of the malware are pretty extensive and the entire spectrum of the device’s functionality is enslaved to it.
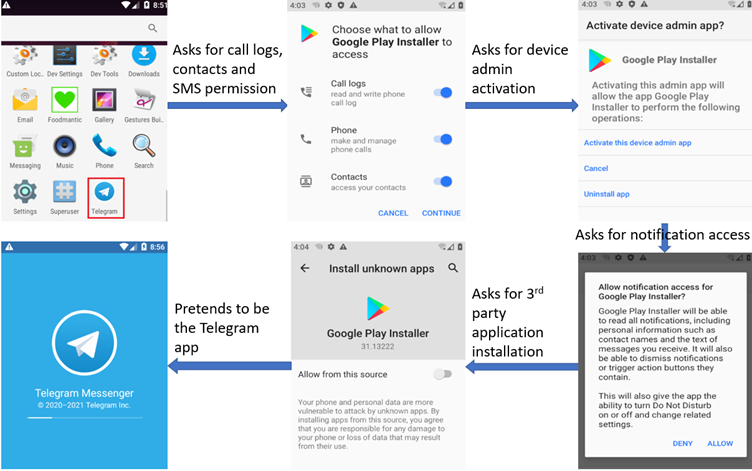
APT-C-23, aka “Two-Tailed Scorpion” or “Desert Falcon,” is using a new Android spyware variant in its Middle East-focusing operations. According to an analysis by the cyber-intelligence firm Cyble, it is a very potent threat. The malicious APK that is distributed through a fake app store uses the name ‘Google Play Installer,’ while its icon mimics that of Telegram. However, it’s nothing of the sort, as it just grabs multiple permissions and then dives deep into the stored data or comes and goes from the infected device.
The spyware requests contacts, call logs, and SMS permissions, the granting of admin rights, access to notifications, permission to install third-party applications, and more. Telegram is somewhat simulated for the trick to work, at least its user interface is, leading victims to believe they are about to use the e2ee messenger app. This is needed for convincing the victim to grant all the aforementioned permission and access requests, giving the spyware full power on the device.
The main capabilities of APT-C-23’s new spyware are the following:
- Read, delete or modify SMSs, call logs, and Contact data.
- Make calls without user interaction
- Delete SMS data
- Kill background processes of other apps
- Receive and send SMSs
- Reads current cellular network information, phone number and the serial number of the affected phone, the status of any ongoing calls, and a list of any phone accounts (for example: firmware accounts such as Samsung account) registered on the device.
- Read, delete or modify the files on the device’s external storage
- Disable the keylock and any associated password security measures such as biometric verification.
- Steal files with the following extensions: PDF, doc, docx, ppt, pptx, xls, xlsx, txt, text, jpg, jpeg, png
- Capture screenshots or even video recordings of the victim device’s screen
- Record incoming and outgoing calls, even when these take place through WhatsApp
The particular spyware is used for specific targeting of users in the Middle East, but it could easily find deployment elsewhere in the future. In this case, we see a dual-masquerading approach that doesn’t make much sense, as Google Play Installer and Telegram don’t match together in any logical context. However, it appears the trick works well in convincing the victims not only to install the APK themselves but also to grant access to over 18 risky permissions.