Annke Video Recorder Vulnerable to Critical Remote Code Execution
- An Annke NVR was found to be vulnerable to remote exploitation that would give the attacker full control of the device.
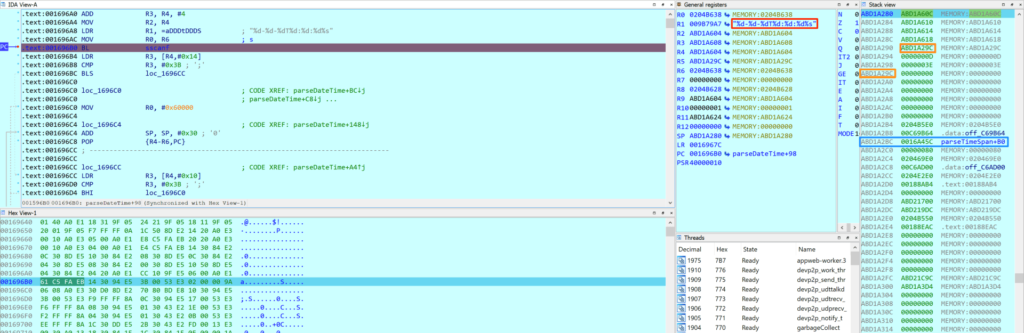
- The issue lies upon a memory corruption issue that can be exploited remotely without authentication.
- The vendor has released a fixing firmware patch very quickly after they got the relevant report.
The Annke N48PBB, a widely deployed video recorder that is commonly part of IoT security camera installations, was found to be vulnerable to a critical remote code execution (RCE) vulnerability that is tracked as “CVE-2021-32941”. The finding comes from researchers at Nozomi Networks Labs. Due to the massive deployment of the product in critical commercial facilities, the CISA has also published an alert to warn owners of the risks and offer advice on how to mitigate the problem.
The particular device is an NVR (network video recorder) which captures and stores video footage from a network of IP cameras. NVRs are central points in security camera stems, not only serving as storage and access channels but also as management solutions. As such, they are excellent targets for malicious actors as they can help them peek into a company and stalk people without anyone realizing it, delete footage, change the configuration of motion detection alarms, stop the recording of some or all cameras - or shut down the NVR altogether.
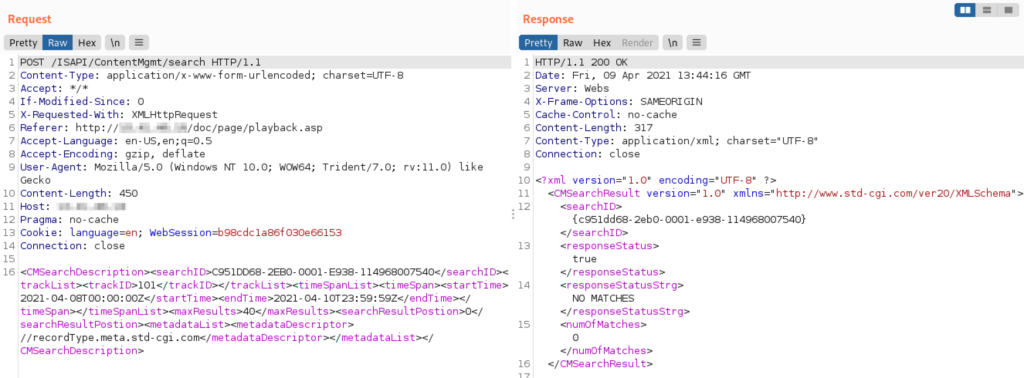
In the case of the Annke N48PBB, the NVR is capable of linking to up to eight IP cameras, watch live streams, manage users and their permissions, search through the catalog, etc. By digging deeper into the HTTP request that any user can send to the device to search in the clip storage, the Nozomi researchers found a denial-of-service flaw, which was later evaluated as a remote code execution issue with root privileges.
Practically, this means that anyone could SSH into the device and do whatever they please. Because there’s no anti-Cross-Site Request Forgery mitigation either, a legitimate admin could be entrapped into a “drive-by download” attack situation, involuntarily executing the malicious code on the device without realizing the fact.
Nozomi reported this to Annke on July 11, 2021, and the company fixed the issue by releasing a firmware update on July 22, 2021, which was admittedly a swift response. As such, the solution to the problem is to upgrade your firmware to the latest available version. If you are running v3.4.106 build 200422 and prior, you are vulnerable to remote exploitation.
In general, IoT security camera systems shouldn’t be exposed to the network if that’s not absolutely necessary, should be hiding behind firewalls, and should be isolated from more critical, business networks. If you have to access an NVR remotely, do so through VPNs to ensure that man-in-the-middle attacks won’t yield anything useful for the hackers.