‘Mozi’ Botnet Is Coming for Your Old and Unpatched Network Gateways
- The Mozi botnet has returned with notable activity in the wild and new persistence tricks.
- The botnet is targeting mainly network gateways from Netgear, Huawei, and ZTE.
- If patching is impossible or a fix not available, at least use a strong password on the devices.
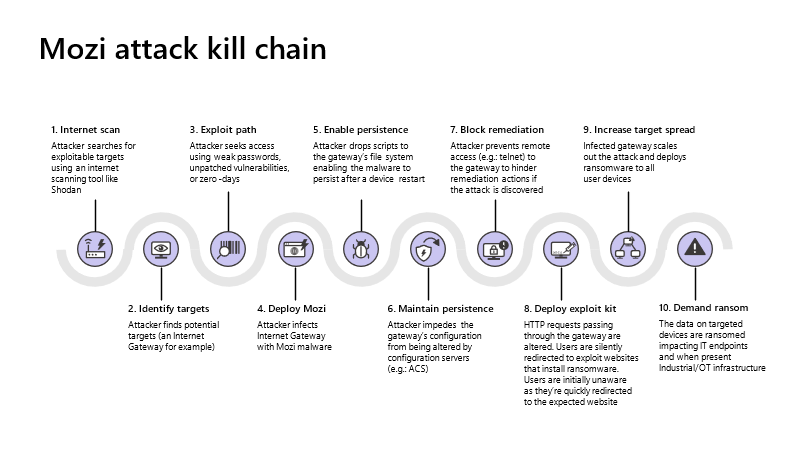
Microsoft warns about a spike in the activity of the ‘Mozi,’ a peer-to-peer botnet that targets mainly IoT network gateways and digital video recorders. The malware exploits weak telnet passwords and several vulnerabilities it has hardcoded in its list to carry out damaging DDoS attacks, perform data exfiltration, run commands remotely, or fetch and execute additional payloads. Microsoft’s threat researchers have found out that the latest versions of Mozi have gotten a lot more potent than previously, as they’ve evolved to achieve persistence on Netgear, Huawei, and ZTE network gateways.
Network gateways are ideal targets for hackers as they’re basically entry points to valuable corporate networks. They are facing the net so they can be scanned through Shodan, categorized based on the unpatched vulnerabilities they carry, and then targeted in wide-scope attacks. The new persistence capabilities rely on the exploitation of the following flaws:
CVE-2015-1328: Improper check of permissions during file creation in the upper filesystem directory, allowing local users to obtain root access by leveraging a configuration in which overlayfs is permitted in an arbitrary mount namespace. The prerequisites for this to work are the existence of the /overlay folder and the malware’s write permissions to the /etc folder. If they are met, Mozi places a script in these folders, which runs /usr/networks or /user/networktmp.
CVE-2014-2321: This is a ZTE specific vulnerability affecting the F460 and F660 cable modems, enabling a remote attacker to obtain administrative access via sendcmd requests and enable a TELNET service. Mozi checks for the existence of the /usr/local/ct folder, and on a positive return, it executes a set of commands that change the modem’s remote configuration to allow full access.
On Huawei modems, Mozi adds three “sh” (executable) files on the /mnt/jffs2/ folder to establish persistence, and it also runs port-blocking commands to shut specific TCP ports that could be used by other adversaries.
These vulnerabilities are pretty old, indicative of the fact that EOL products are still out there and oftentimes used in critical environments. In the cases where firmware/software updates or equipment replacement is impossible, Microsoft suggests the deployment of ‘Defender for Endpoint,’ which can detect and stop Mozi. Additionally, admins should change the passwords used in these devices with something strong and at least apply the most recent patches released by the vendor, even if these date years ago.