4 Novel Techniques Help Phishing Emails Evade Detection
- Microsoft warns about four new methods phishing actors follow in order to evade detection.
- In most cases, the tricks involve adding obfuscation in the HTML code without affecting what the recipient sees.
- Unfortunately, some of the new techniques cannot be blacklisted as the repercussions would be wide.
For phishing actors, success boils down to delivery rates, as sending out millions of emails and managing to get only a few hundred through the filters is a waste of time, effort, and resources. As such, these crooks are constantly trying new techniques that could help them evade detection and keep those “red flags” of warning down. Microsoft’s Threat Intelligence team has spotted four new practices that are getting traction in the underground phishing community and is detailing them in a blog post.
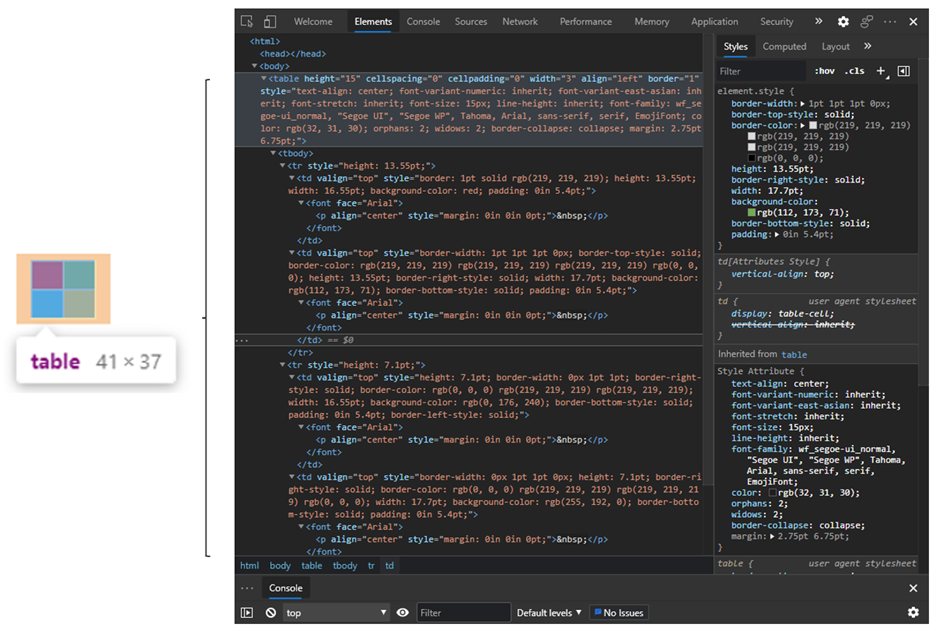
The first trick is to use HTML tables to imitate the logos of the impersonated brand in phishing emails instead of using an image file for the purpose. The number of detected cases using a 2x2 HTML table and CSS styling to resemble a logo is falling for some reason, but it remains significant. Because there is no image file to scan, and because inserting an HTML table into the email isn’t considered malicious on its own, security solutions and anti-phishing filters won’t be triggered.
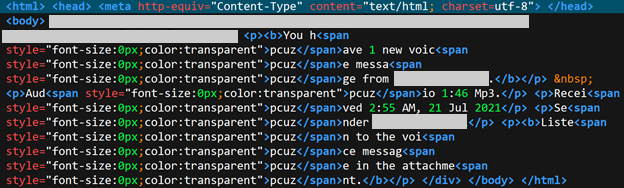
The next method which is currently on a steep rise in deployment is text padding with invisible characters. In most cases, the Unicode characters used for breaking up keywords in the email body and the subject line are Soft hyphen (U+00AD) and Word joiner (U+2060). The idea is to insert invisible characters between “keywords” that are typically in the blacklist of anti-spam solutions. In this case, too, the invisible characters are not inherently malicious, so they can serve their purpose of tricking the recipients without raising any alarms.

Thirdly, there’s the technique of inserting hidden words with a font size of zero into the email body. This approach is also on the rise in deployment as it appears to be working well for the actors. The idea here is to add “garbage” HTML and CSS into the email body, right between words and phrases that could trigger security solutions.
And finally, there’s the technique of victim-specific URI, seeing a stable usage trend at the moment. This method involves the inclusion of custom URI parameters utilizing PHP to display information about the target. This approach can convince the victim by presenting a level of personalization that is not typical of large-scale phishing. Simultaneously, because the data interaction to draw the user’s details isn’t intrinsically malicious, security solutions won’t express any objection to it.