‘Ficker’ Infostealer Is After Your Credit Cards and Crypto Wallets
- ‘Ficker’ is out there, looking to grab your credit card info, login credentials, crypto, and email accounts.
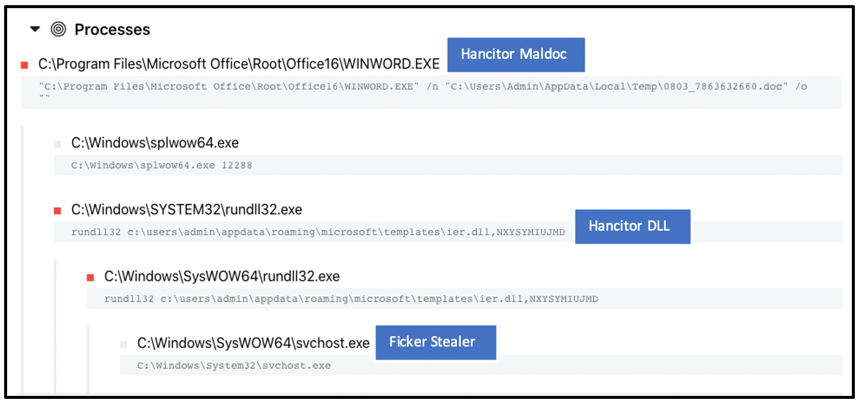
- The malware is dropped through laced Word documents that arrive via spam mail campaigns.
- The data is encrypted and exfiltrated on the fly, sent directly to the C2 without storing anything locally.
‘Ficker’ is an infostealer written in Rust and targeting Windows systems, offered to cybercriminals as a MaaS (malware as a service) on Russian-speaking hacker forums. It was first uncovered last year, noticed distributed via Trojanized websites that promised free access to Spotify and YouTube Premium. This year, the program is expanding and getting more impactful. ‘Ficker’ can target and steal information stored or entered in web browsers, FTP clients, and other apps, going mainly for credit card details as well as crypto-wallets. As such, it’s going directly for the money.
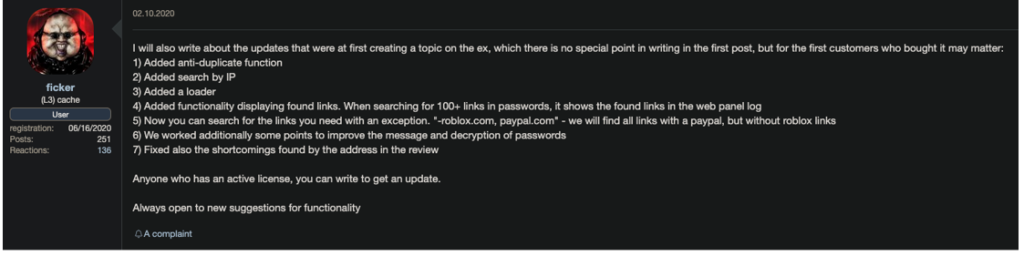
A report on the BlackBerry blog describes a malware that’s being actively developed and promoted on various forums, with the author posting periodically to update the community of the latest improvements implemented on Ficker. Recently, the deployment of the malware begun involving ‘Hancitor’, a malware that uses Trojanized MS Word documents delivered as extensions on spam emails. These documents feature malicious macro that runs when opened and fetches Ficker right from the C2 of the operator.
The malware is injected into a svchost.exe instance on the compromised system to evade detection and hide its activity, and it first runs a keyboard layout check to exclude the following countries: Russia, Belarus, Uzbekistan, Armenia, Kazakhstan, and Azerbaijan. If any of these layouts is detected, the malware terminates. Ficker also checks the victim’s IP address through a web API call to ensure that no tricks are played.
The data targeted by Ficker for exfiltration includes the following:
- Chromium web browsers – Saved login credentials, Cookies, Auto-complete history
- Mozilla-based web-browsers – Saved login credentials, Cookies, Auto-complete history
- Credit card information
- Cryptocurrency wallets
- FileZilla FTP client
- WinSCP FTP client
- Discord login
- Steam accounts
- Pidgin accounts
- Thunderbird accounts
Instead of writing this information on the disk prior to exfiltration, as most infostealers do, Ficker sends the data directly to the C2 (asfasfvcxvdbs.com) after passing it through an elementary XOR encryption, thus retaining some control over who is allowed to use the malware and rendering any leaks useless. As the same XOR key is used across all analyzed samples, the encryption isn’t very strong, but it is enough to evade detection in most cases.
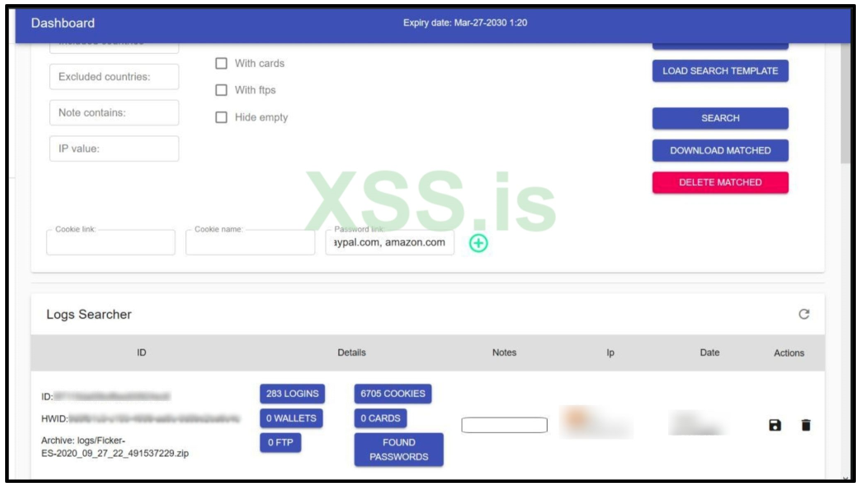
In addition to the above, Ficker can also capture screenshots by allowing the remote user to send the relevant command right from the dashboard. This opens up a very wide spectrum of exploitation possibilities, as the actors may potentially steal any information from the victim.