‘AdLoad’ Malware Campaign Plaguing macOS With New, Undetectable Variants
- ‘AdLoad’ campaign is infecting macOS systems for months now, and XProtect appears unable to stop it.
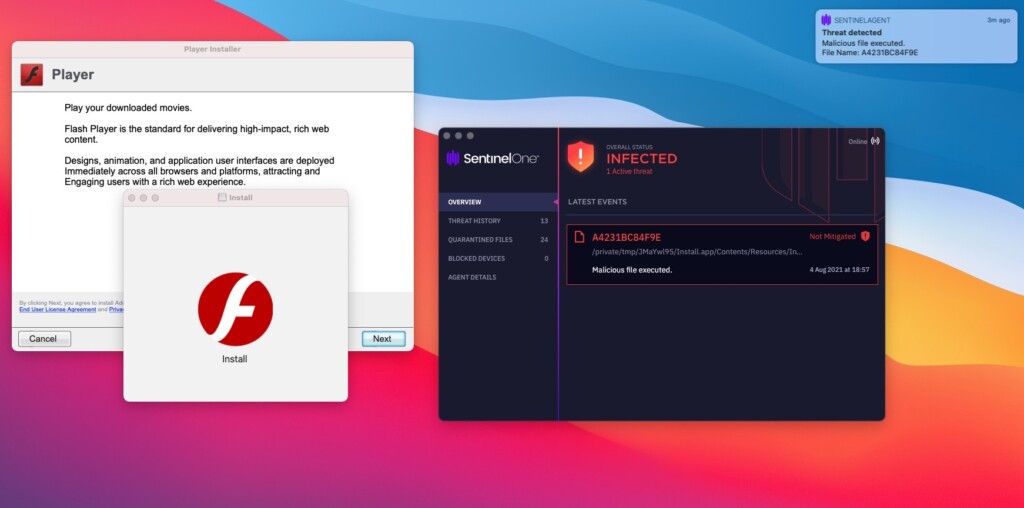
- The adware is dropped through fake Flash installers, which is typical of macOS malware.
- In several cases, researchers noticed samples of the latest variant to be notarized by Apple.
The ‘AdLoad’ malware is back to targeting Apple devices with a new variant that can successfully evade detection from XProtect, the built-in macOS antivirus solution. As reported by researchers at SentinelLabs who have analyzed the recent campaign, some samples of AdLoad even come signed by Apple’s notarization service, which wholly excludes them from Gatekeeper and XProtect checks, giving them a green pass to deliver ads to its victims. In total, SentinelLabs has recorded 150 unique samples that are used in the most recent campaign, all operating undetected.
AdLoad has been around since 2017, and its authors never really stopped trying to bypass Apple’s protection systems and stay ahead of security engineers. XProtect has added 11 signatures for AdLoad today. Still, since these cover very specific variants that are no longer in use, there’s no detection and/or protection against the most recent versions. This cat and mouse game has Apple always one step behind, responding to new variants after the fact.
The 2021 variant relies on a file extension that is either “.system” or “.service” and around 50 unique label patterns pertaining to these two. AdLoad establishes persistence by executing a binary that is hidden in the same folder (~/Library/Application Support/) where the rest of the bundle files end up. The “trojan” used to bring the adware into the system is a fake Player.app Flash installer, which is the same that is used as a dropper for Shlayer.
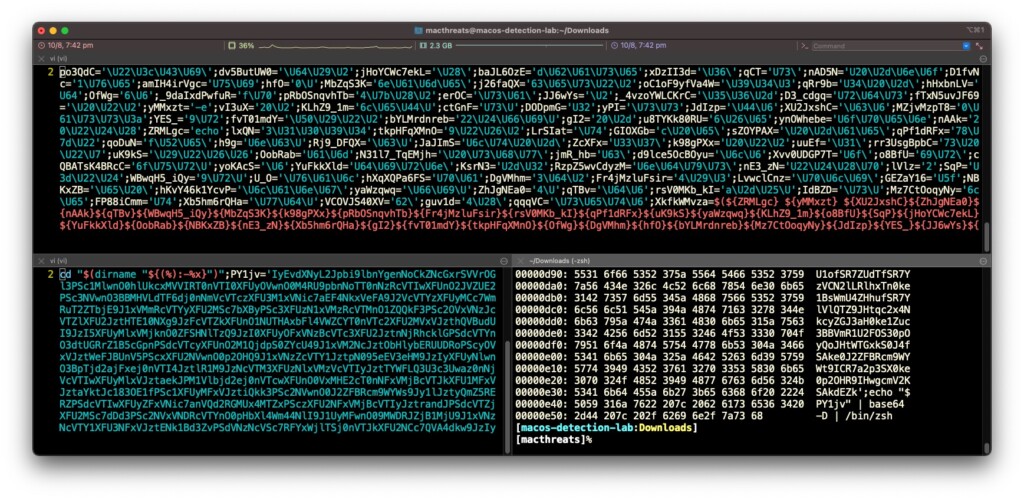
The dropper executes a shell script that features several layers of obfuscation, as well as a custom string encryption scheme. While this is enough to trick even the latest version of XProtect (2149), it isn’t for most engines in VirusTotal, so third-party AV tools for the macOS should be able to catch the threat.
If left unchained, ‘AdLoad’ will hijack search engine results on the compromised systems and inject ads into websites the user attempts to visit. This severely disrupts and degrades the user experience as it’s like having a persistent promoter by your side all the time. This is precisely the problem many macOS users have been having for over 10 months now - roughly when the ongoing campaign started. However, Apple’s built-in detectors are still unable to catch up with the problem and address it decisively.