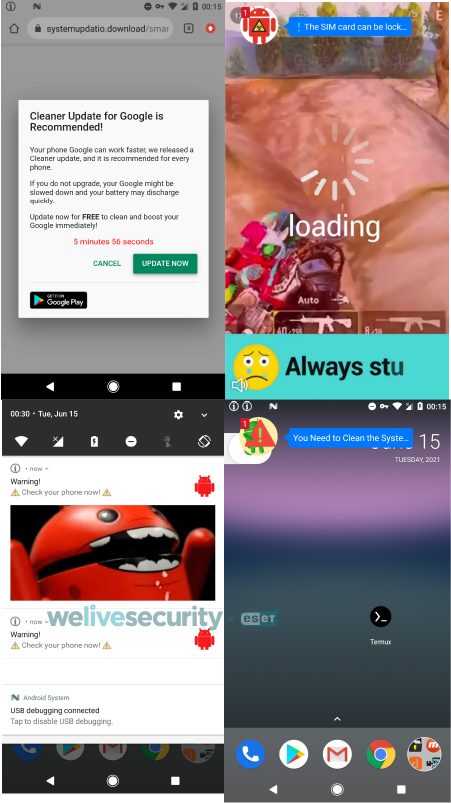
Malware Distributors Abuse URL Shortener Services to Spread Dangerous Apps
- URL shortener services are being increasingly abused by malware distributors who exploit the lack of policy enforcement.
- Users are typically tricked into downloading risky apps through the serving of “scareware” ads.
- The apps request the granting of extremely risky permissions, and in tens of thousands of cases per year, they get approval.
URL shortener services are always a gamble as you can never be sure about what comes out of the machine if you don’t actually test it. As it is to be expected, there are quite a few platforms with loose policies that allow malicious individuals to take advantage of the URL transformation and infect those who click on the “shortened” links with malware, banking trojans, and info-stealers. The latest ESET report from malware analyst Lucas Stefanko dives deeper into the problem, presenting some of the most active real-world examples right now.
The problems start with the delivery of “scareware” ads to the person who clicked on the shortened URL, informing them that their mobile devices have been infected with malware. To respond to the risk, the users are urged to download an app from the Google Play Store or the Apple App Store (depending on the platform). In the case of Android, the apps that are downloaded are basically banking trojans and adware under disguise, while on iOS, calendar-event-creating items are being downloaded.
In the following video, Stefanko demos an example of a URL shortener service message which urges the user to download another APK file from a source outside the Play Store. The names used for these APKs are always deceitful, pretending to be something useful like an adblocker or a security utility. In some cases, if the victim clicks on the download button twice, they will get the correct installation file on the second try.
The abused URL shortener services do mention that the transmission of malicious files is prohibited, but they do nothing to enforce the policy or investigate cases of potential abuse. The ads that their partners are using are solely their responsibility, so the platforms give them full freedom to do whatever they want, including distributing malware.
ESET’s telemetry shows that this particular type of problem started all the way back in September 2019 and has been growing steadily. In 2021 alone, ESET recorded 150,000 instances of Android malware downloads happening through abused URL shortener platforms. This tells us that the scale of the problem is already pretty big, and some regulation needs to be enforced immediately. To make matters worse, the C2 servers analyzed by ESET have the ability to distribute different payloads, so this is a well-organized operation of an unpredictable nature.
If you have downloaded any apps of this kind following the advice of an unexpected pop-up, go ahead and manually uninstall it immediately. Then, run a full system scan using a mobile security tool from a reputable vendor. If you’re on iOS, use a Calendar cleanup tool.