Spanish Users Targeted by Novel Campaign Using an Old Malware Strain
- A group of actors is targeting Spanish-speaking users with a 14-years old malware strain.
- The emails used in the campaign pretend to carry financial documents from South American companies.
- The actors are deploying the RAT to steal sensitive information like user account credentials.
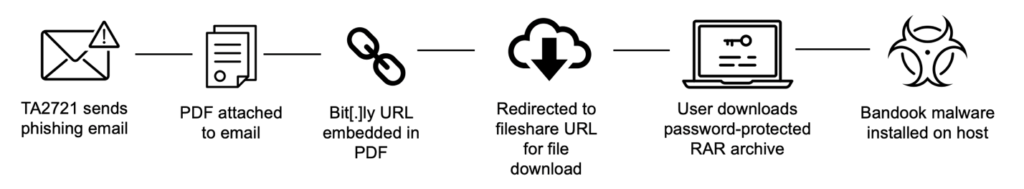
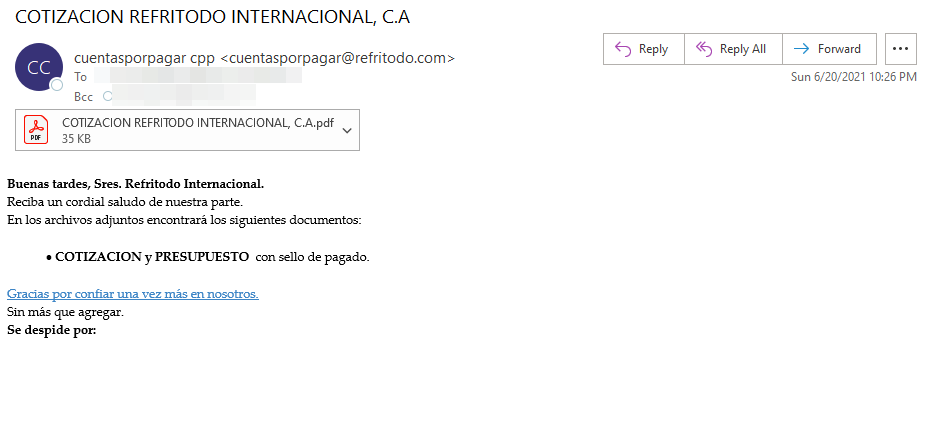
There’s a mass malware distribution campaign going on right now, spreading an old strain called “Bandook” to Spanish-speaking users. The group responsible for this is TA2721 (“Caliente Bandits”), tracked identified by Proofpoint researchers, and while the sophistication of their operations isn’t very high, the scale and activity are impressive. In most cases, the actors masqueraded as companies located in a South American company, sending financial-related emails to the targets.
The infection chain starts with the arrival of a PDF document via email, with a malicious URL contained in the file. If clicked, a redirection circle begins leading to the download of an encrypted RAR file is delivered onto the recipient’s system. Then, that file unpacks and installs the Bandook RAT locally. The emails and the filenames are all in Spanish, hence the targeting. Also, the RAR is protected with a password that is provided in the PDF file, giving a false sense of privacy to the recipient while also making it harder for some AV tools to catch the threat.
Proofpoint has noticed the following three C2 domains, which were used for extensive periods of time.
- “s1[.]megawoc[.]com” was used in January
- “d1[.]ngobmc[.]com” was used from March to June
- “r1[.]panjo[.]club” was used since June
It means that the actors didn’t have to deal with reporting and blacklisting problems, keeping the same C2 infrastructure for entire months.
The use of Bandook is a rare occurrence in the malware distribution world, as this is a RAT first seen in the wild in 2007, so it’s considered pretty obsolete at this point. However, it is worth noting that Bandook was never entirely gone from the cyberthreat space. Last year, we saw it being distributed globally again through macro-ridden documents arriving via email. It is a publicly available malware, so it's easy to source and deploy, even if passing it through AV protections is a hopeless procedure for the actors that choose to use it.
As for what this old RAT can do, capturing screenshots, video, audio, as well as performing keylogger duties are among its most powerful features. Bandook attempts to hide from defense tools by using base64 string encoding, using “Process Hollowing” for the payload injection, and also by using AES encryption for the C2 communications. Proofpoint reports that all samples of the malware sourced from the “Caliente Bandits” campaign use the same hardcoded AES key, so the actors appear to be using an off-the-shelf tool.