Israeli Spyware Vendor Linked With Microsoft Windows Zero-Day Exploits
- An Israeli spyware firm named ‘Candiru’ was linked with the exploitation of recently patched zero-days.
- The company has made an OpSec mistake which allowed researchers to link its spyware with its infrastructure.
- The latest government campaigns targeted at least 100 victims in several countries.
Researchers at the CitizenLab and the Microsoft Threat Intelligence Center have discovered the spyware (“DevilsTongue”) of a previously obscure vendor based in Tel Aviv, in Israel, operating under the name ‘Candiru.’ Reportedly, the vendor was using spyware that exploited two (CVE-2021-31979 and CVE-2021-33771) of the four zero-days that Microsoft fixed with the latest Tuesday patch.
Moreover, the investigators confirmed that there are over 750 websites that support the particular spyware, and there are at least a hundred victims located in Palestine, Israel, Iran, Lebanon, Yemen, Spain, United Kingdom, Turkey, Armenia, and Singapore.
The malware that Candiru promotes only on a government level is presented as “untraceable” and can infect iOS, Android, macOS, and Windows. Even cloud accounts can be compromised and monitored by the spyware, allegedly without raising any alarms no matter what service is used. Microsoft has posted a complete technical analysis of “DevilsTongue,” so if you’re interested in diving deeper, check out this page.
As a company, Candiru makes a sincere effort to not draw the attention of the public. Having been established in 2014, the company registered four more corporate names in the years that followed and also spun a subsidiary. According to a lawsuit of a former employee spotted by CitizenLab, Candiru has sold $30 million worth of spyware licenses between 2014 and 2016 alone, with clients reportedly based in Europe, Russia, the Persian Gulf, Asia, and Latin America.
This sounds like the typical spyware firm that sells its tools to oppressive regimes around the globe without considering the ethical aspect of its business. Starting from 2019, Candiru was fully uncovered as a seller of cyberweapons, and various media stories linked them with the government of Uzbekistan, Saudi Arabia, the United Arab Emirates, Singapore, and Qatar.
However, Candiru has a list of restricted territories for deploying its products, including the United States, Russia, China, Israel, and Iran. This is exactly the same restriction list used by the NSO Group. As Microsoft’s investigation confirmed, though, Iran was still targeted in recent campaigns nonetheless.
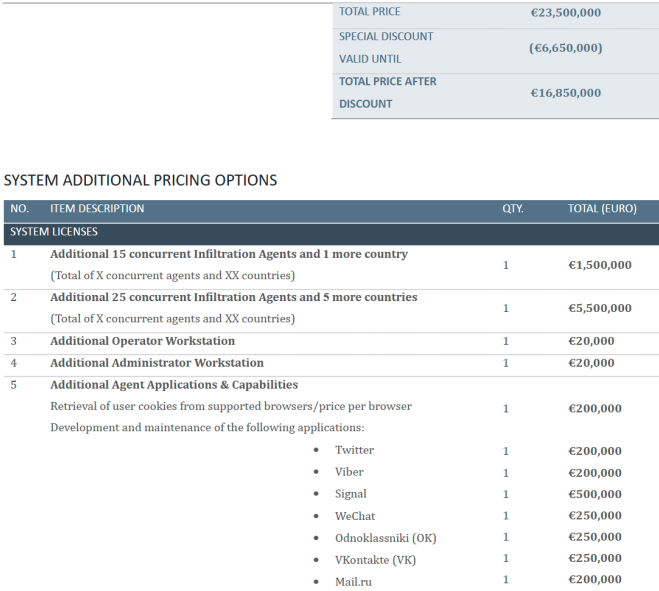
Through a leaked confidential project proposal, we learn that Candiru sells its main product for €16 million, and then adding on top of that for the simultaneous monitoring of multiple devices, conduct espionage operations in more countries, etc.
The linking between the spyware caught in the wild and Candiru was a case of OpSec failure, as CitizenLab was able to find an email address from a self-signed TLS certificate that belongs to Candiru’s main domain. From there, more matches were made as more IP addresses and certificates were correlated, leading to SQL queries and the final mapping of the firm’s infrastructure.
Many websites sitting on this infrastructure masquerade as international media portals, advocacy organizations like ‘Black Lives Matter’ or Amnesty International, tech giants like Microsoft, Google, and Apple, social media platforms such as Facebook and Twitter, international organizations like the United Nations, and Wikipedia. This pluralism is nothing else than a pool of entrapment possibilities for activists, journalists, politicians, human rights defenders, and freedom of speech advocates.