This Is How Iranian State Actors Steal User Credentials From Their Targets
- TA453 is using webinar invitations to trick professors into handing over their account credentials.
- The hackers send convincing emails to their targets and lead them to a compromised page.
- Next, a phishing pop-up opens up to steal credentials on a wide range of services.
Proofpoint has had an interesting interaction with ‘TA453’/APT35, an Iranian state-supported actor who is also known as “Charming Kitten” or “Phosphorus,” and has published a report to present the phishing method of the particular group. In their recent campaign, TA453 members masquerade as UK scholars at the University of London’s School of Oriental and African Studies (SOAS) to target British individuals of high intelligence collection interest. For this reason, Proofpoint calls the campaign “Operation Spoofed Scholars.”
Starting in early 2021, someone using the name “Dr. Hanns Bjoern Kender” and also “Tolga Sinmazdemir” sent emails through “hannse.kendel4[@]gmail.com” and “t.sinmazdemir32[@]gmail.com” to the group’s targets, using well-articulated language and no spelling errors, which something atypical to phishing emails. The email invites the recipient to speak to a webinar, presenting a relevant subject to the target’s expertise and including registration guidelines. Here’s a sample of an email sent by TA453 to a target.
The actors show no reluctance to engage in video conferencing communication with the target, demonstrating their English skills once more. Additionally, they have shown interest in phone numbers, possibly to plant malware or carry out smishing acts.
In general, Proofpoint reports that “Operation Spoofed Scholars” targets professors, senior think tank personnel, and journalists who cover Middle East topics. These people potentially hold useful information for the Iranian government but are very selectively targeted, so some form of a pre-evaluation goes on.
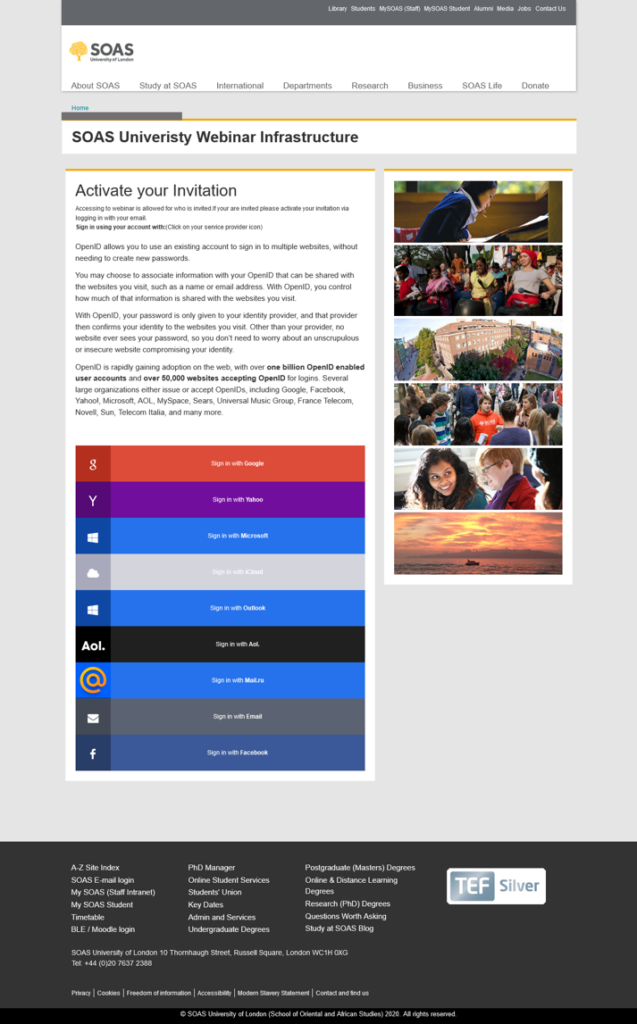
The phishing part comes when the target is convinced to click on the shared link, which takes them to a compromised SOAS page. This is particularly nasty because other pages on the same site continue to host legitimate content, so the victim could be easily convinced that they’re dealing with a real invitation from the University of London.
The harvested credentials include usernames and passwords from Google, Yahoo, Microsoft, iCloud, Outlook, AOL, mail.ru, Email, and Facebook. In some cases like Google and Microsoft accounts, the target’s email address is even pre-filled. Proofpoint tested this step and confirmed that the validation from the actor’s side takes place manually, almost immediately.
The only thing that would save victims from this phishing lure would be to have activated two-factor authentication on their accounts. Possibly, this is why the actors want to learn the target’s phone number so dearly. Besides that, you should always verify any invitations of this kind by calling the university directly. Something as simple as validating the existence of the presented webinar would clear the fog.