Kaspersky Password Manager Was Generating Easily Guessable Passwords
- Passwords generated with older versions of the Kaspersky Password Manager are easily crackable.
- This is due to a series of fundamental cryptographic errors that create a probabilistic guessing model.
- Kaspersky suggests replacing older passwords with newly generated ones.
The Kaspersky Password Manager was found to be generating weak passwords that are easy to brute-force by researchers at Ledger Donjon, who began analyzing the software two years ago. Password generation is a key side-function of password managers, helping users create and assign lengthy passwords with random characters that make up for a strong result. In the case of Kaspersky’s tool, though, it appears that any passwords generated on it could be guessed by a computer in mere seconds.
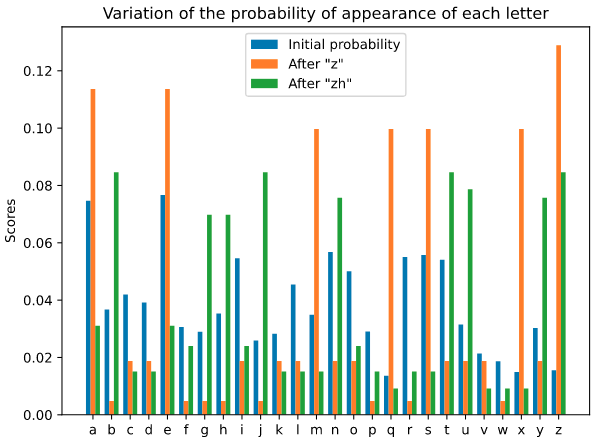
The way Kaspersky Password Manager was set to generate passwords is seemingly complex, involving random floats, a multiplication step for increased entropy, and character picking based on dictionary infrequency. Additionally, the password generator uses the system time as a seed, and if a hacker correlates this with the account creation, they could narrow down the results to 100 probable passwords. Even in more vague cases, the number of passwords wouldn’t be more than a thousand.
This creates a probabilistic model upon which a password cracker would rely. If the password isn’t long enough (less than 12 characters), free tools like ‘John the Ripper’ would be able to guess it quickly, as long as the cracker knows the pass was generated on Kaspersky and sets the parameters accordingly. If the password is longer, but the cracker knows the time of creation, it would take a couple of minutes to brute-force it.
All of that was discovered and reported to Kaspersky back in June 2019, and the security company pushed the first fix in October of that year. However, that fix wasn’t completely free of defects, so it took another year to address the problem properly on all platforms, assign a CVE code (CVE-2020-27020), and alert users that they need to re-generate their passwords.
In April 2021, Kaspersky published an advisory, and in May, technical information for the vulnerability was published. If you have generated any passwords on KPM versions prior to those shown below, consider them easily crackable. In this case, update your software and generate new ones.
- Kaspersky Password Manager for Windows 9.0.2 Patch F
- Kaspersky Password Manager for Android 9.2.14.872
- Kaspersky Password Manager for iOS 9.2.14.31
As for Kaspersky’s engineers, they have learned never to use "time" for seeding passwords, never to use floats in cryptography, always use a cryptographic random number generator, and to convert from bits to an alphabet of symbols.