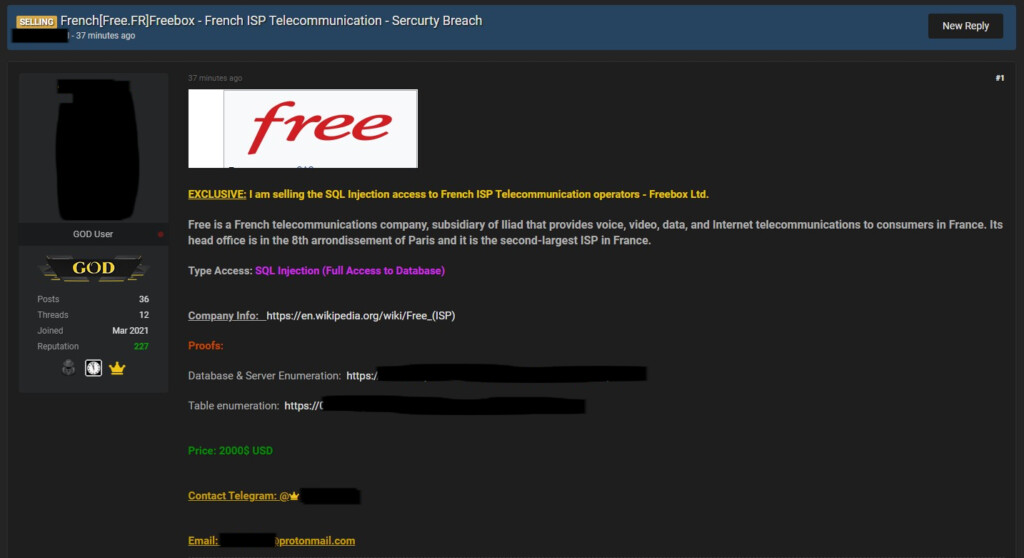
Hacker Broke Into French ISP ‘Free’ and Is Now Selling Database Access
- A hacker claims to have accessed the French ISP ‘Free’ database and is now selling it for $2,000.
- There has been no data exfiltration yet, even though the hacker claims to be able to see subscriber details.
- If the data breach is confirmed to involve customer data, it’ll be a GDPR violation and a massive exposure.
A hacker has gained access to the database of ‘Free,’ a Paris-based telecommunications provider - which is actually a subsidiary of Iliad. Having failed to receive a response from the company when he alerted them about the SQL injection, the hacker proceeded to list the database access for sale on a popular forum, setting the price to $2,000 for anyone interested.
If the seller's claims are true, the buyer could gain access to a trove of valuable and sensitive data, potentially causing great troubles for the French firm and its customers.
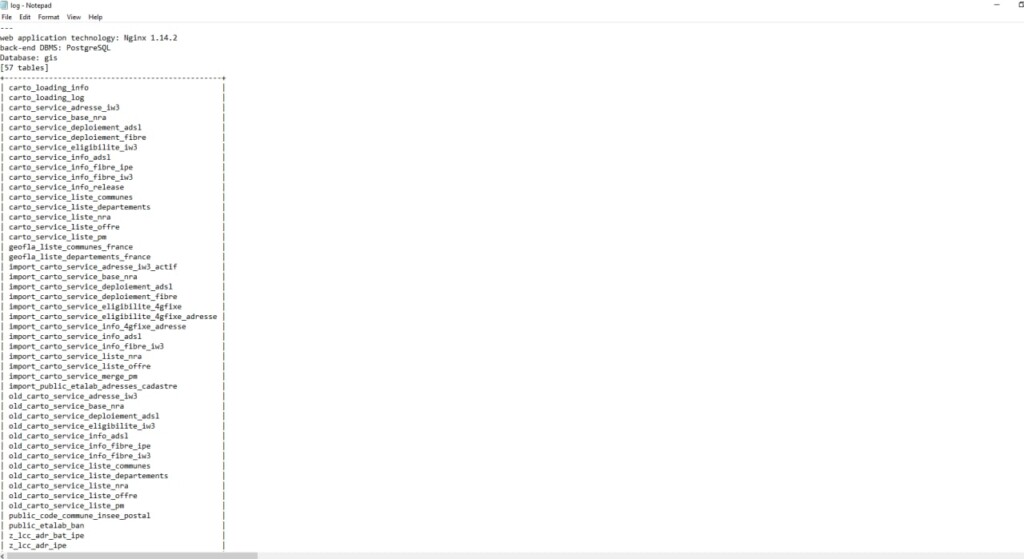
We have reached out to the hacker to ask for more details and also additional proof of the validity of the claims, and we got a confirmation of the access in the form of screenshots. Also, it is noteworthy that other “prominent” members of the forum claim to have access to that data, too, implying that the database has been vulnerable for a long time now.
To the “million-dollar” question of whether the access exposes customer/subscriber details, the hacker responded affirmatively - so if this hack is confirmed by the company, it will automatically qualify as a GDPR violation. This would incur an investigation from the data protection authority in the country, and depending on the results, a hefty fine could also be imposed. The hacker told TechNadu that if ‘Free’ continues to ignore his messages, he will soon release client data too.
We are working towards verifying this alleged security incident with ‘Free’ through our contacts in France, and we will hopefully have a response from the company soon. If the database access is confirmed to be true, it could mean that information like customer names, email addresses, mobile numbers, member credentials, user ID, IP address, etc., will have been exposed. As of now, it is important to clarify that such an exposure has not been officially confirmed.
Notably, the actor had to resort to selling access to the database to get the company's attention - and to cash in his hacking efforts, of course. The alternative route would be an immediate response from the firm and possibly also the payout of a bug bounty for pointing out the vulnerability and helping the company fix it.
This confirms the breach but devalues it at the same time. The hacker indeed accessed the company's systems but 'Free' claims that there's nothing valuable in the datasets that were accessed. We chatted with the hacker again and he told us that the access to the company's systems is still open, and soon, client data will be published online.