TeamTNT Has Compromised Nearly 50,000 Vulnerable Kubernetes Endpoints
- TeamTNT has already entered 50,000 misconfigured Kubernetes servers using a worm-like attack.
- The actors are using open source network scanning tools and exploit open kubelet API ports.
- Mining Monero on Kubernetes servers is ideal because these endpoints have access to limitless resources.
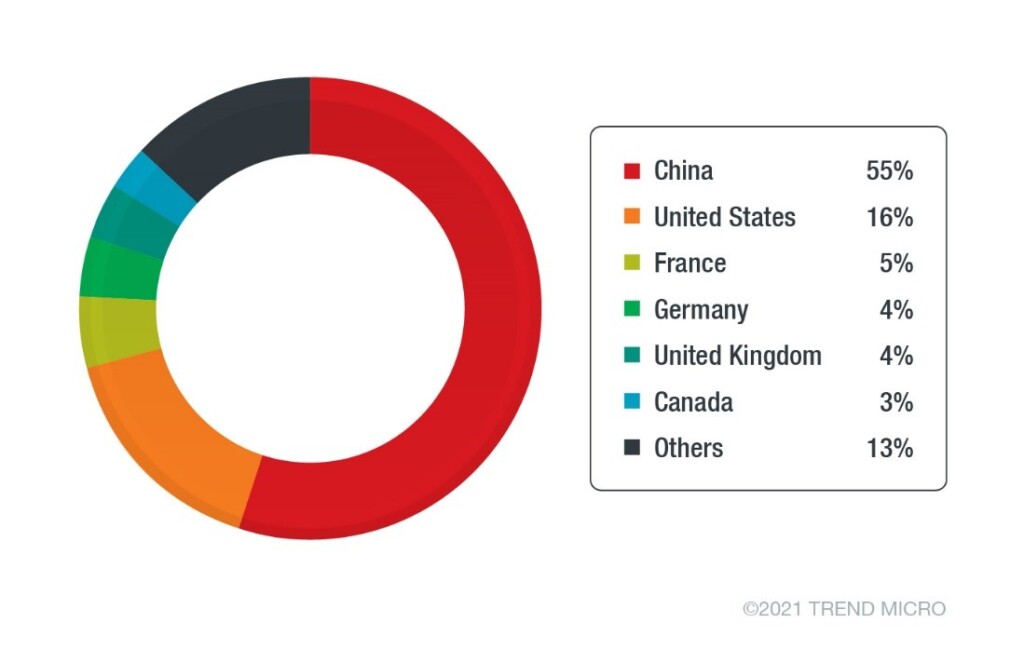
It looks like TeamTNT’s worming attacks are working exceptionally well against misconfigured and vulnerable Kubernetes endpoints, as according to a recent TrendMicro report, the malicious actors have compromised nearly 50,000 of them. Most of the intrusions target Chinese servers, while the United States, France, Germany, the UK, and Canada are also significantly affected. As the researchers report, some of these servers got repeatedly exploited, indicating the automation that goes in the scanning and worm-like spreading of the malware onto vulnerable endpoints.
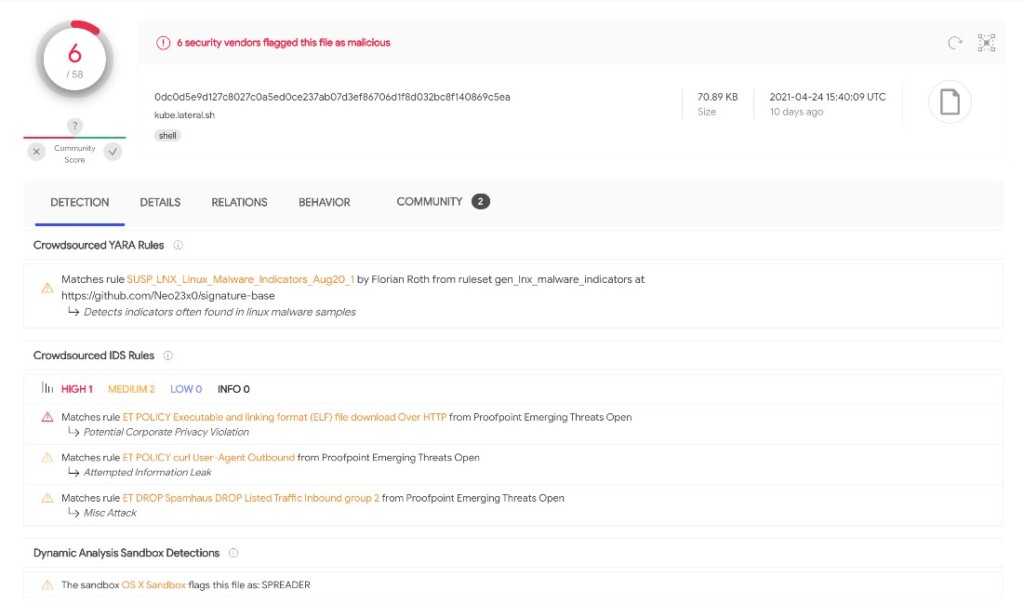
TeamTNT appears to be using an executable named ‘kube.lateral.sh’, which is only detected by a fraction of AV engines in VirusTotal, so the chances to raise any red flags are slim. The hackers also disable the bash history on the target host and set up the C2 server communications to accommodate the Monero miner (XMRig) that’s dropped later.
The script also installs masscan and Zgrab, two off-the-shelf open-source network reconnaissance tools. Masscan is checking for any hosts with port 10250 open, which is left to open by default as part of the kubelet API.
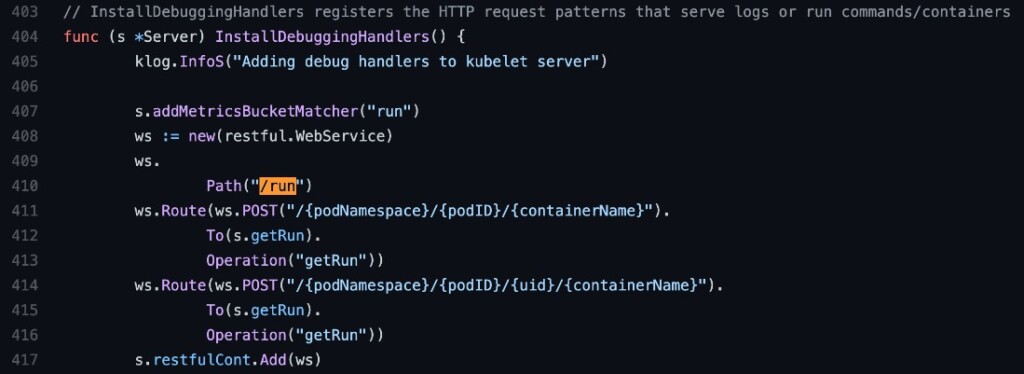
The malware then lists all the running pods inside the node and then takes advantage of the /run endpoint to execute the following four commands:
- Update the package index of the container
- Install bash, wget, and curl
- Download a shell script called setup_xmr.sh from the C&C server and save it on the tmp folder
- Execute the script that starts the mining of Monero
In order to shut the door to TeamTNT’s attacks, you should close port 10250 on operational K8s clusters and protect Kube API servers from exposure. By running “curl -k https://API-SERVER-IP:PORT/api.”, you can check if any of your APIs are public-facing and remediate the issue. Moreover, running cloud security products would be a wise thing for sure.
Only a week ago, we analyzed why ‘TeamTNT’ is now considered a serious threat, having evolved from an “opportunistic actor” status. This latest report about Kubernetes targeting specifically underlines the fact that TeamTNT is targeting a wide scope of vulnerable systems, and with its worm-like attacks, the scale of the compromise is already impressive.