Apple Releases macOS Fix to Plug Zero-Day Flaw Exploited by the “XCSSET” Malware
- Apple has pushed security patches for all its software products, fixing one notable zero-day in macOS.
- The particular flaw was being under active exploitation by the “XCSSET” malware gang to exfiltrate screenshots from the infected machine.
- The iOS, iPadOS, tvOS, and watchOS have also received rich sets of fixes, so it’s time for patching for everyone.
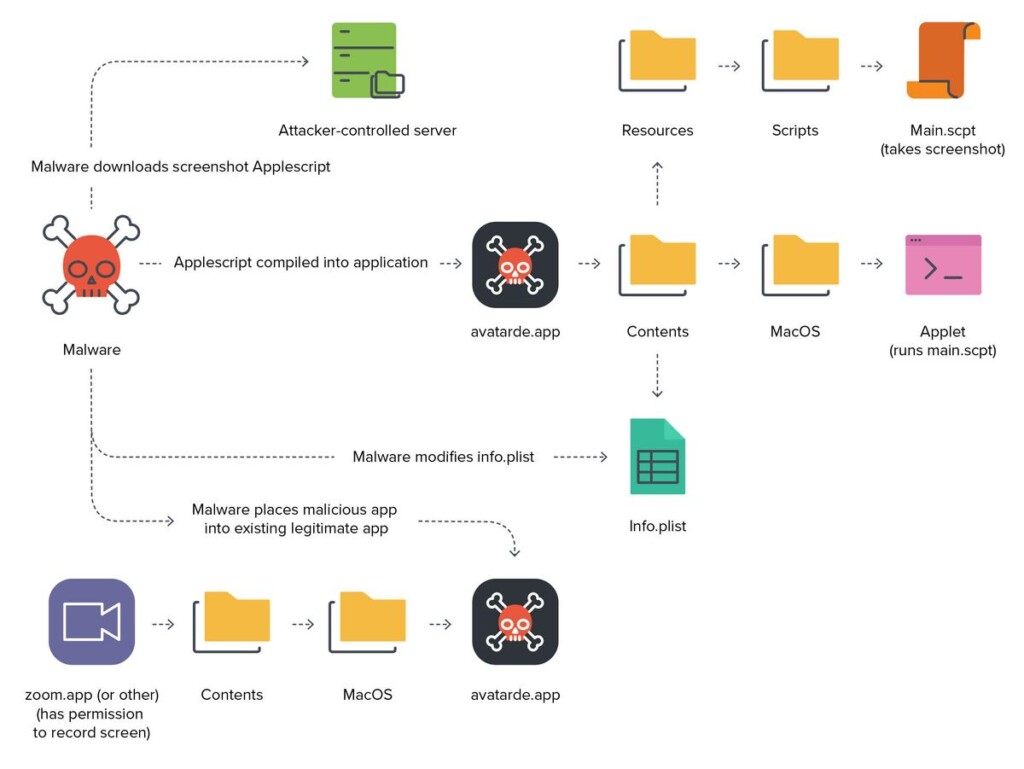
Apple has released security updates for its various software products. The most notable this time is a macOS fix that addresses a zero-day, which was under active exploitation by the “XCSSET” malware group. The flaw is tracked as “CVE-2021-30713” and allows bypassing the Transparency Consent and Control (TCC) framework, which is the system’s control module that gives apps access to resources. For example, TCC is what gives Zoom access to the camera and microphone, or the screenshot tool access to recording and disk access (for storing).
By bypassing this security system, the XCSSET malware was able to take screenshots of the victim’s system or record keystrokes, essentially stealing all kinds of sensitive information and exfiltrating them to an attacker-controlled server. The malware itself is written in AppleScript and is to be found in multiple Xcode projects, spreading via laced Github repositories.
Previously, it was thought to be limited in stealing Safari cookies also through the exploitation of two separate zero-days. But as researchers at Jamf discovered, this was not the entire story around XCSSET.
Due to the criticality of this finding, Apple’s patching covers Big Sur (11.4), Catalina (2021-003), and also Mojave (2021-004), the three latest macOS releases. If you’re using anything older than that, you’re on your own. The majority of macOS systems, though, are covered by the latest fixing patches, so get updating immediately.
As for the release of the iOS 14.6 and iPadOS 14.6, apart from the galore of new features (for a point release) that have landed with it, there is also a set of 43 security vulnerabilities that Apple’s engineers have addressed, some of which are pretty significant. It is important to point out, though, that the firm is marking none of them as actively exploited.
Typically, we have an actively exploited zero-day in Safari’s WebKit engine being addressed with a patch every month or so. We don’t see this urgency this time, but the component is still carrying two remote code execution flaws that look pretty nasty nonetheless. These are CVE-2021-30749 and CVE-2021-30734.
On the rest of Apple’s software lineup, we have 25 security fixes on the watchOS 7.5 and another 26 flaws addressed on the tvOS 14.6. As always, Apple chose not to give away many details about any of these fixes, but so the main takeaway for everyone here is to update your Apple devices as soon as possible.