Tens of Thousands of VoIP Devices From Around the Globe Are Publicly Exposed
- There’s a large number of public-facing VoIP/SIP devices that are easy to discover, evaluate, and target.
- Many of these devices are vulnerable to multiple known and disclosed CVEs, and some are over a decade old.
- These VoIP devices should be properly secured and masked, ideally replaced with a new model if no longer supported.
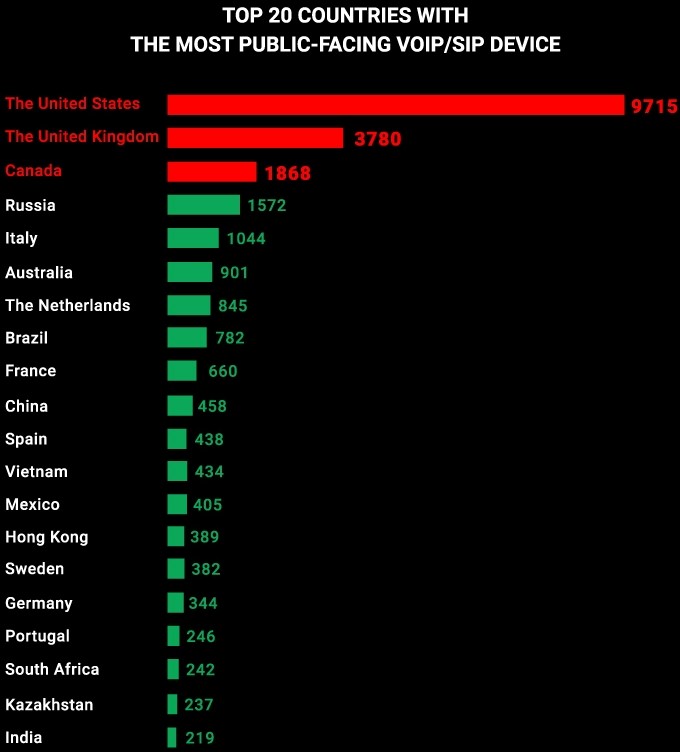
Researchers at CyberNews have scanned and found at least 38,335 public-facing VoIP/SIP devices on the net, many of which carry severe vulnerabilities. The majority of those are based in the United States, which accounts for approximately one-fourth of the total number of publicly exposed devices. Significant numbers are also found in the United Kingdom, Canada, Russia, Italy, Australia, and the Netherlands.
VoIP/SIP devices are supposed to be connected to the internet, of course, as they need to provide internet telephony services to their users. However, publicly declaring them as phones is problematic because it automatically makes them a target. In the worst-case scenario, a malicious actor would explore the existence of potential vulnerabilities and use the device as a pivoting point into more valuable systems in the network. In the best case, you may have to deal with SIP server hijacking and crooks making money at your expense.
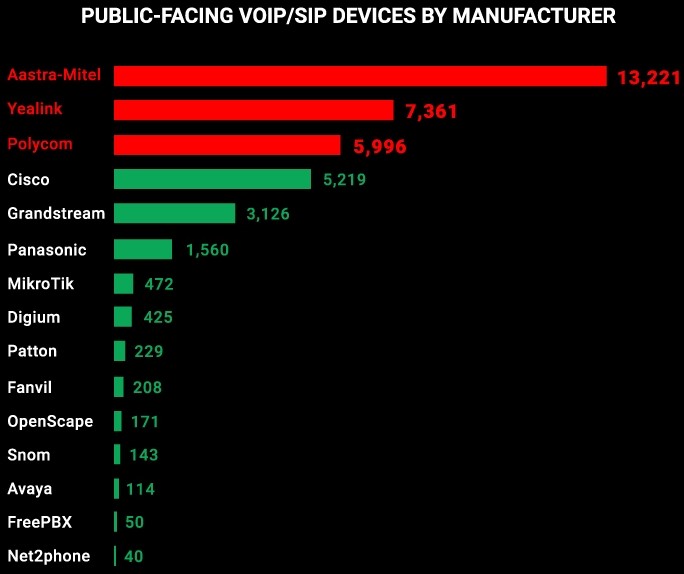
As the CyberNews report details, many of those exposed devices are pretty all, some having been released ten years ago or more. In fact, most of the public-facing devices were made by Aastra Technologies, a company that Mitel Networks acquired in 2013. Then, there are over seven thousand devices made by the Chinese Yealink, six thousand made by Plantronics, and five thousand made by Cisco.
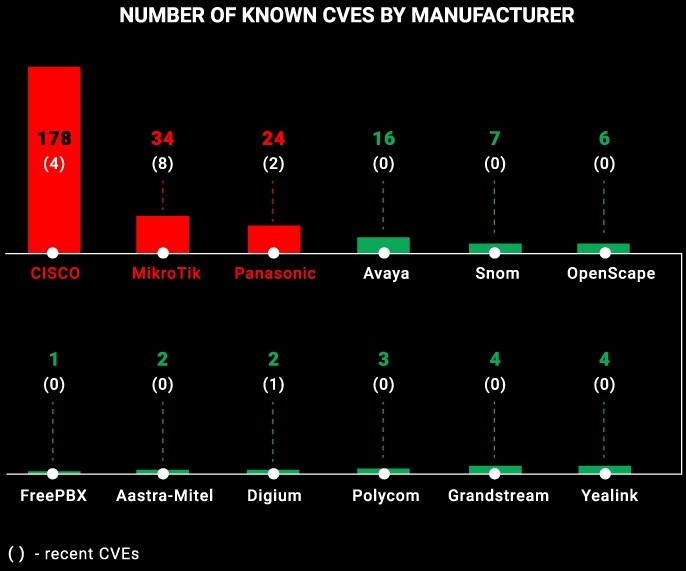
Cisco, for example, has the biggest number of recorded vulnerabilities, counting 178 - four of which are recent. This large number is the result of Cisco’s vigilant security research, and it doesn’t mean the devices of other manufacturers are safer. On the contrary, it is possible that they are systematically zero-dayed by hackers and the victims don’t ever get to learn about it.
If you are using a VoIP/SIP device, make sure to use strong passwords, enable NAT as an additional layer of protection, set your firewall to shut port 80, disable the web configuration interface, and only enable it when needed to use it. If your device is old and no longer supported by the manufacturer, you should replace it with a new one. In that case, take the old devices for electronics recycling and don’t try to resell them.