Leaky Peloton API Allowed Anyone to Access Private User Data
- The Peloton app API allowed any user to access someone else’s data even if they were in “private” mode.
- Peloton failed to address the flaw quickly enough and had to be warned by the press to take proper fixing action.
- It is not unlikely that someone has already scraped all user data from the leaky API, planning to publish it soon.
When U.S. President Joseph Biden was preparing to move into the White House in January, his cybersecurity experts stopped his favorite Peloton indoor exercise bike in order to “dumbify” it first. They figured a device connected to the internet to enable riders to live stream their exercise sessions, or take on-demand classes, or compete on online leader boards, and more is too great of a risk for the next U.S. President. As security researcher Jan Masters has now proven, they were absolutely right about that.
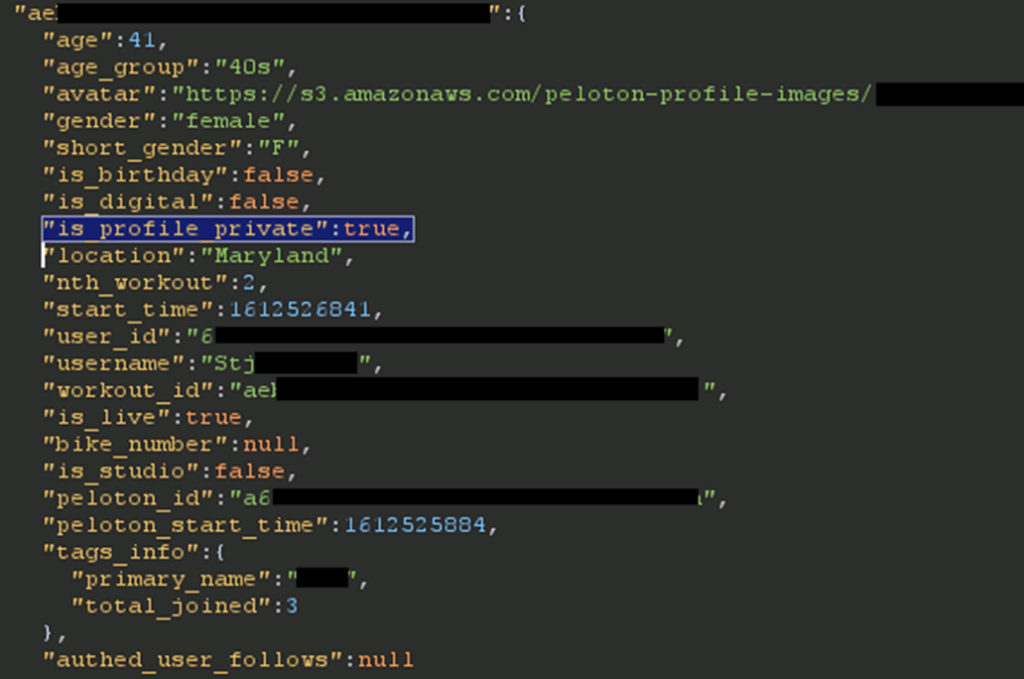
The researcher has found out that an unauthenticated user could view sensitive information for any user of the Peloton network, snoop on their activities, and collect potentially useful data that could be used for a variety of nasty stuff. More specifically, the information that could be accessed includes the following:
- User IDs
- Instructor IDs
- Group Membership
- Location
- Workout stats
- Gender and age
- If they are in the studio or not
The location and presence status is maybe the most critical, as one could take advantage of this crucial piece of information in many useful ways. Also, considering that Peloton has over three million subscribers and one million connected fitness subscribers, this was a very important finding, no doubt. Thus, the researcher reached out to the company on January 20, 2021, and disclosed the matter privately.
Technically, the problem was in the back-end APIs of the mobile and web apps, with the endpoints revealing the information to everyone with no consideration about whether they are authenticated or not. Such flaws can lead to automated attacks through scoopers, leading to massive data leaks at once.
Peloton acknowledged the report's reception immediately, but they then went silent, and the fix they implemented shortly afterward didn’t exactly work in stopping the attacks. The firm added a requirement for the user to be authenticated in order to access the API, but since anyone can register, that wouldn’t be a problem. Also, the fact that three million people could still access one another’s data even if they used their bike in “private” mode isn’t exactly addressing the flaw.
Not being able to convince Peloton to get back to him, the researcher reached out to Zack Whittaker of TechCrunch. A week after the journalist undertook the communications, the vulnerabilities were eventually addressed, so the matter is now public but fixed.
It wouldn’t be surprising if anyone posts the entire Peloton userbase data on a hacking forum soon, as the API stayed open for at least four months. The firm can check the logs and see if there’s any evidence of that, but for now, they haven’t commented on this possibility.