Researchers Find That SAP Admins Have Only 72 Hours to Secure Their Systems
- Researchers collected observations from hundreds of exploit attempts against SAP and have alarming results to report.
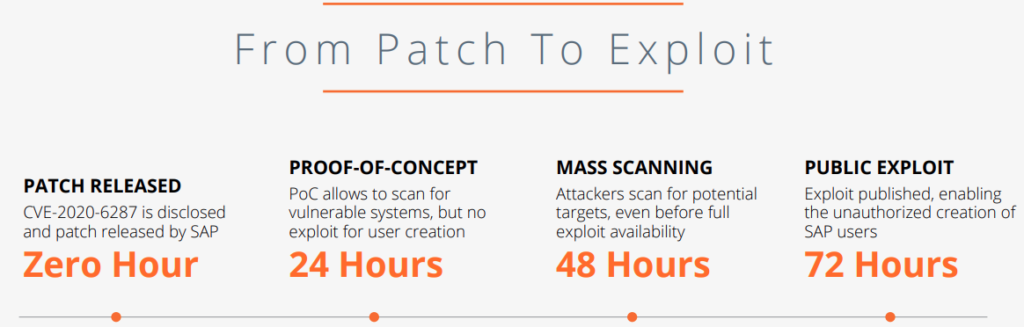
- Actors can develop fully-working exploits using published flaw details in as little as 72 hours.
- SAP admins don't have any margin to fool around, as their systems are considered top-value stuff for APTs.
The German software vendor SAP has worked together with infosec experts from Onapsis to figure out how SAP-specific attacks unfold, how long it takes actors to weaponize critical vulnerabilities published in security advisories, and what the entailed risks of being negligent are. Their findings are worrying enough to guarantee an alert by CISA (Cybersecurity & Infrastructure Security Agency), warning about the resulting risks of data exfiltration, financial fraud, disruption of mission-critical business processes, ransomware infections, and more.
According to the detailed Onapsis report, the most exploited vulnerabilities and misconfigurations in SAP products are the following:
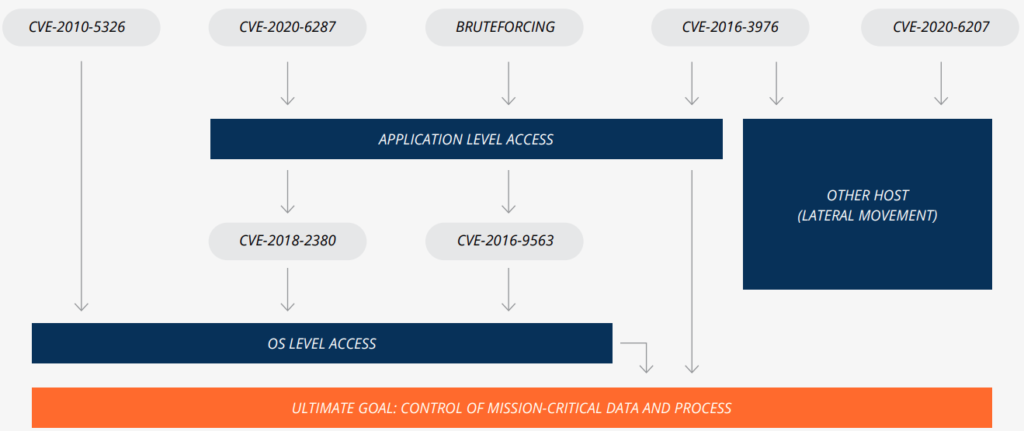
- Unsecured High-Privilege SAP User Accounts
- CVE-2020-6287 (application-level access)
- CVE-2020-6207 (cross-system compromise)
- CVE-2018-2380 (privilege escalation from the application to the OS)
- CVE-2016-9563 (privilege escalation from the application to the OS)
- CVE-2016-3976 (application-level access), (cross-system compromise)
- CVE-2010-5326 (direct OS-level access)
By observing a large number (over 300) of automated exploitation leveraging the above, as well as over 100 manual sessions launched by a range of threat actors, Onapsis concludes that 72 hours would be the average time for the weaponization of published flaws. Thus, this is about time that admins patch their SAP solutions, as any minute after that has their systems popping up on malicious mass scanning results.
Additionally, new unprotected SAP apps provision in cloud environments are being discovered and compromised in as little as three hours in the worst-case scenario. On average, scans will discover the systems in two days, and the exploitation will come in a week.
Considering that SAP software is used in over 400,000 organizations around the world and that 92% of them are in the Forbes Global 2000, these findings are both crucially important and at the same time somewhat expected. Targeting big military forces, defense and security organizations, pharma producers, global utility companies, and government agencies is something for top-level threat groups and APTs. These groups are skillful enough to develop exploits and weaponize published flaws quickly, and this is actually what they're working on full-time.
To mitigate the associated risks, SAP and Onapsis recommend organizations to take the following actions:
- Perform a compromise assessment on SAP applications that are still exposed to the vulnerabilities mentioned above.
- Assess all SAP environment applications for risk and immediately apply the relevant SAP security patches and secure configurations.
- Assess SAP applications for the existence of misconfigured and/or unauthorized high privilege users.
- If applying patches or mitigations is impossible, resort to vigorous activity monitoring.