Chinese Hackers Going After Russian and Mongolian IT Firms
- The TA428 is moving aggressively on the web again, targeting Russian and Mongolian IT entities now.
- The Chinese hackers are now using spoofed news websites to inject malicious DLLs into their targets.
- The payloads include Poison Ivy, PlugX, and Royal Road, while lateral movement is achieved through an EternalBlue exploit.
Chinese actors of the TA428 group have been attributed involvement in a campaign that targets various Russian and Mongolian government and private IT entities. According to a report by Recorded Future’s Insikt Group that has been following TA428’s activity, the first indications appeared on January 21, 2021, and it seems that the attacks are ongoing. TA428 is a very active actor who has been around since at least 2011, utilizing Poison Ivy payloads, the Cotx RAT, sending spear-phishing emails, and sophisticated post-exploitation techniques.
This time, the actors are using spoofed domains that mimic Mongolian and Russian news sites' themes. The researchers also noticed the presence of Bloomberg, a US-based news outlet, but it is clear that no American companies or entities are in the scope of this campaign.
The following websites are used by TA428 right now:
- aircraft.tsagagaar[.]com – Tsag agaar (цаг агаар) is a Mongolian word for “weather”
- nubia.tsagagaar[.]com – Likely spoofing New Ulaanbaatar International Airport (NUBIA)
- gazar.ecustoms-mn[.]com – Likely spoofing Mongolian e-customs
- govi-altai.ecustoms-mn[.]com – References the Govi-Altai region of Mongolia
- gogonews.organiccrap[.]com - Likely spoofing Mongolia news agency GoGo News
- niigem.olloo-news[.]com – Likely spoofing Mongolian news agency Olloo
- oolnewsmongol.ddns[.]info – Likely spoofing Mongolian news-themed domain
- bloomberg.mefound[.]com – Additional spoofed news-themed subdomain
- bloomberg.ns02[.]biz – Additional spoofed news-themed subdomain
- ecustoms-mn[.]com
- f1news.vzglagtime[.]net
- news.vzglagtime[.]net
- nubia.tsagagaar[.]com
- olloo-news[.]com
- nmcustoms.https443[.]org
- tsagagaar[.]com
- vzglagtime[.]net
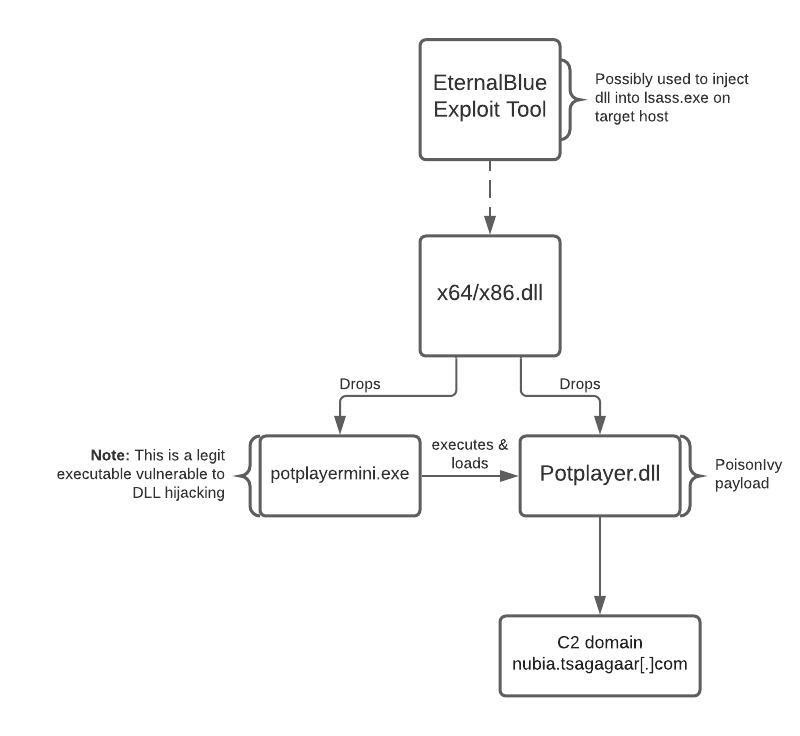
The payloads used by the actors include Poison Ivy, PlugX, and Royal Road, but various port scanners are used too. The researchers sampled two distinct DLLs designed to run in 32-bit and 64-bit environments, respectively, and which drop two files each. One is the payload itself, and the other is a legitimate executable that is vulnerable to DLL hijacking. Apparently, the actors are still using the same EternalBlue exploit for lateral movement that was discovered by NTT researchers back in October 2020.