Beware of ‘AlumniLocker’ and ‘Humble,’ Two New Ransomware Strains
- Two new ransomware strains are being actively distributed out there, and they are both very effective.
- The first one is already operating on a high level, demanding a lot of money and threatening with data publication.
- The second appears to be going through a testing phase, demanding a small, almost symbolic amount.
Researchers at Trend Micro have sampled two new ransomware variants, namely the "AlumniLocker" and "Humble," which exhibit worryingly sophisticated post-encryption techniques. The first strain is put in the same category as established players in the field, as it’s asking for high ransom amounts and features a data leak portal for extortion right from the beginning of its operation.
This is a very alarming finding in general, as it shows that ransomware actors now treat the double-extortion of data stealing and data encryption as a standard requirement.
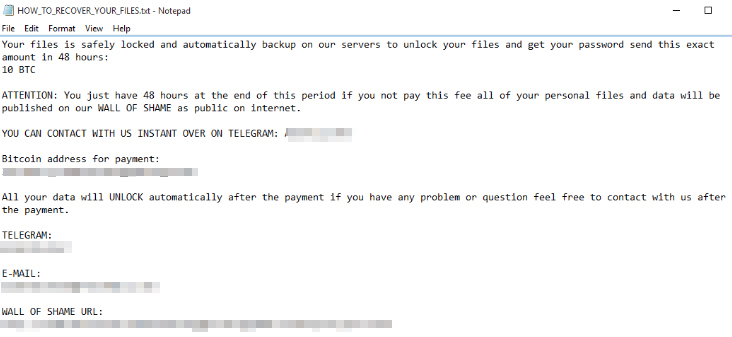
AlumniLocker appears to be a variant of the Thanos ransomware family, and its operators are asking for a ransom payment of 10 bitcoins. The victims are threatened that if they don’t send the requested amount within 48 hours, their data will be published on the actor’s leak site. That’s a pretty short time for such a large amount of money.
The infection channel for AlumniLocker is typically a PDF file that arrives via email as an attachment. Usually, the subject has something to do with an invoice that supposedly requires the recipient's attention.
Inside the PDF, there’s a URL link. If clicked, it downloads the ZIP archive - which contains the downloader. This activates a PowerShell script, and finally, the ransomware payload is fetched and executed through a BITS module.
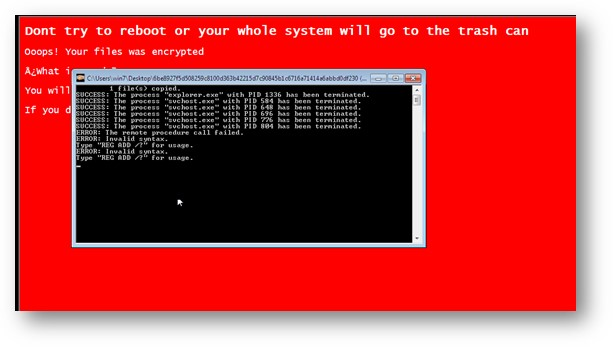
The second new strain, Humble, first appeared in the wild in February 2021, compiled with an executable wrapper and utilizing a public webhook service from Discord for infection reporting. Humble is very aggressive as it doesn’t even allow explorer.exe to access or view local storage drives, while it also threatens the victims that if they dare to restart their machine, it will rewrite the master boot record (MBR).
The malware abuses the Windows certificates service to generate a key from a randomized input and then use it on the "extd.exe" component to encrypt the victim’s files. In total, Humble targets 104 file types including .exe, .pdf, .mp3, .jpeg, .cc, .java, and .sys.
Humble's ransom demand is pretty low, at just 0.0002 bitcoins, and the time to pay is a “comfortable” five days. The operators may have set the ransom amount so low because they are only testing out their payment processing system, so they need to ensure that the victims actually pay. That said, we may soon see Humble demands getting upgraded, as it’s very unlikely that the actors will focus their targeting on home users.