‘Povlsomware’ Ransomware May Not Be Used Only by Researchers
- An “educational” ransomware tool called Povlsomware could turn into a powerful commodity for malicious actors.
- The particular ransomware tool is set to be innocuous, but being open-source, it could be modified.
- The fact that Povlsomware features Cobalt Strike integration makes it very enticing for malware authors.
"Povlsomware" is a proof-of-concept ransomware available on Github since November 2020, released with the goal of being a tool for research like testing anti-virus solutions that claim to offer ransomware protection. As researchers of the Trend Micro team warn, Povlsomware’s compatibility with post-exploitation tools like Cobalt Strike is actually making the sample potentially valuable in the hands of malicious actors.
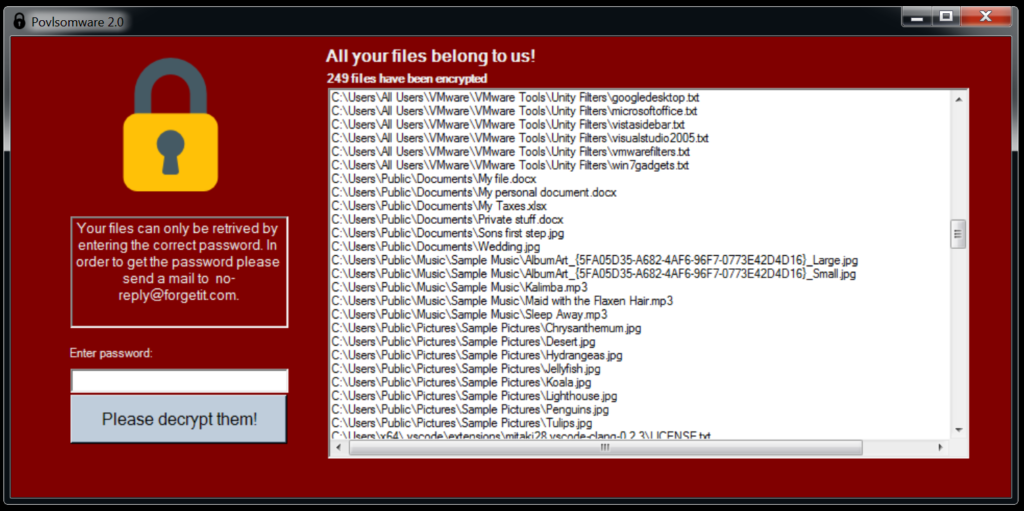
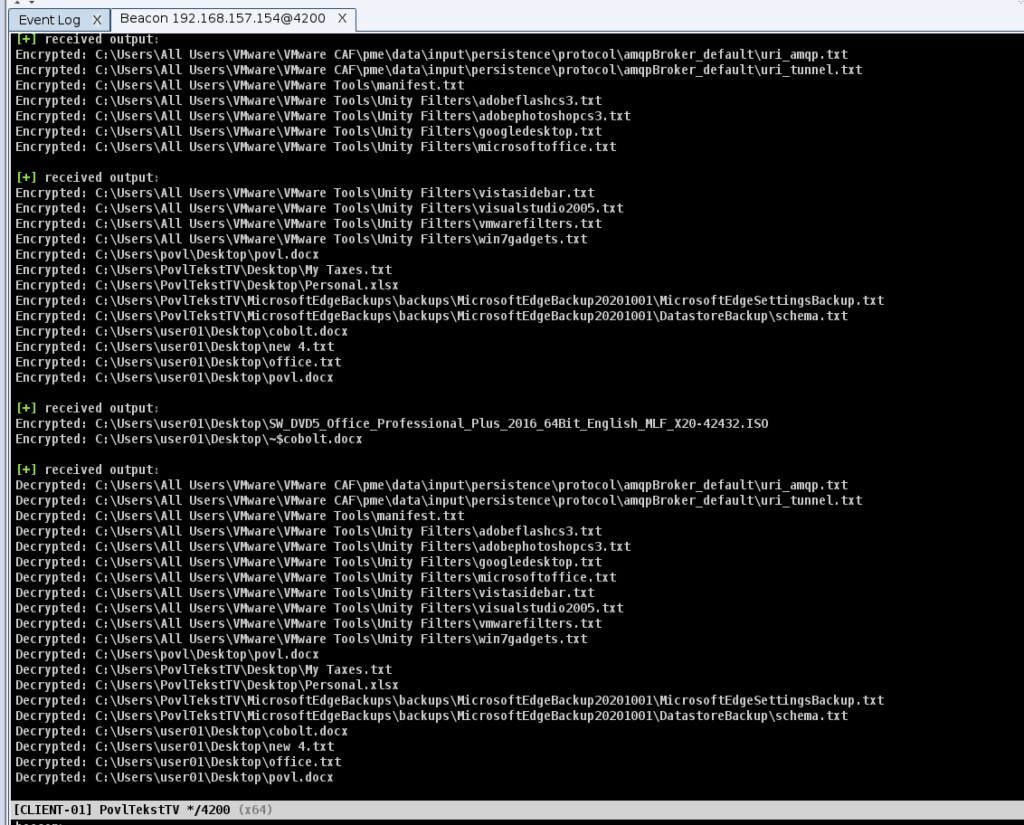
As distributed, the sample ransomware scans the file system and encrypts common personal files using AES256. All shadowcopies that would help restore the system are deleted, a registry entry ensures start-up persistence, and a pop-up is displayed to inform the infection user. The decryption password is “blahblah,” so the researchers can bring back their test files as if nothing has happened.
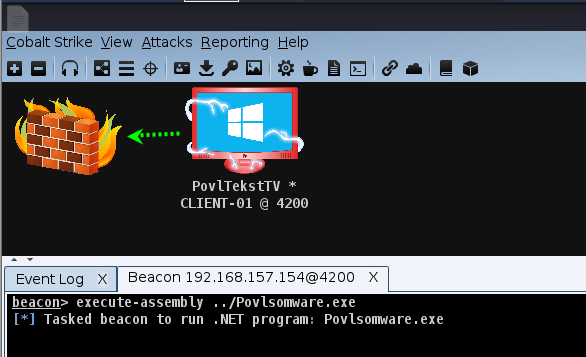
Being an open-source project, though, anyone can take Povlsomware and modify it, making it a lot more dangerous than what its authors intended. Because Povlsomware is integrated with Cobalt Strike, it can be executed directly in memory, not even requiring it to nest in the victim’s memory or drop any binaries there. This makes this particular strain very interesting and potentially powerful, as detecting and stopping it would be a lot harder.
Also, because Povlsomware doesn’t append any extension names onto the encrypted files, the victim would not see an apparent difference in the files beyond the fact that they aren’t working. This makes the encryption stealthy, following a diametrically different path than what’s the case with virtually any other ransomware strain.
For now, Trend Micro hasn’t noticed any real incidents involving a modified Povlsomware, but based on what can be deduced from all the inter-playing factors, this is just a matter of time. For this reason, the security firm has opted to warn the community, even if that means turning the attention of cyber-criminals to Povlsomware.
One key aspect of this is that AV and security solutions vendors, in general, could start treating Povlsomware for what it is, a potentially dangerous malware that should be stopped at the door. The compromise indicators are out there for everyone to use, but again, this is a piece that can run without dropping binaries on the victim’s storage. Hence, the main responsibility to security burdens the users and their practices.