Clop Ransomware Leak Portal Publishes Bombardier Data
- Bombardier was compromised by ransomware actors of the Clop gang.
- The actors accessed, stole, and are now leaking sensitive data on their leak portal.
- Bombardier is only one of many victims of Clop attacks relying on the exploitation of Accellion FTA bugs.
The ransomware actors of the “Clop” gang have published data samples that appear to belong to Bombardier, the Canadian train and airplane manufacturer. The firm has admitted the incident by publishing an official statement.
They explained that, unfortunately, its forensic analysis revealed that personal and other confidential information relating to 130 employees (based in Costa Rica) and an undefined number of customers and suppliers were compromised. The manufacturing operations or customers support services haven’t been impacted in any way due to the incident.
The Clop actors have managed to break in through Accellion FTA, exploiting several vulnerabilities on the legacy product and managing to compromise about a hundred targets out of a total of 300 FTA clients still using it. That said, Clop isn’t extorting only Bombardier right now, but also ‘Fugro,’ ‘Danaher,’ ‘Singtel,’ and ‘Jones Day.’ More victims may be added to the Clop extortion list, as the crooks are currently sorting what they got and deciding what to leak.
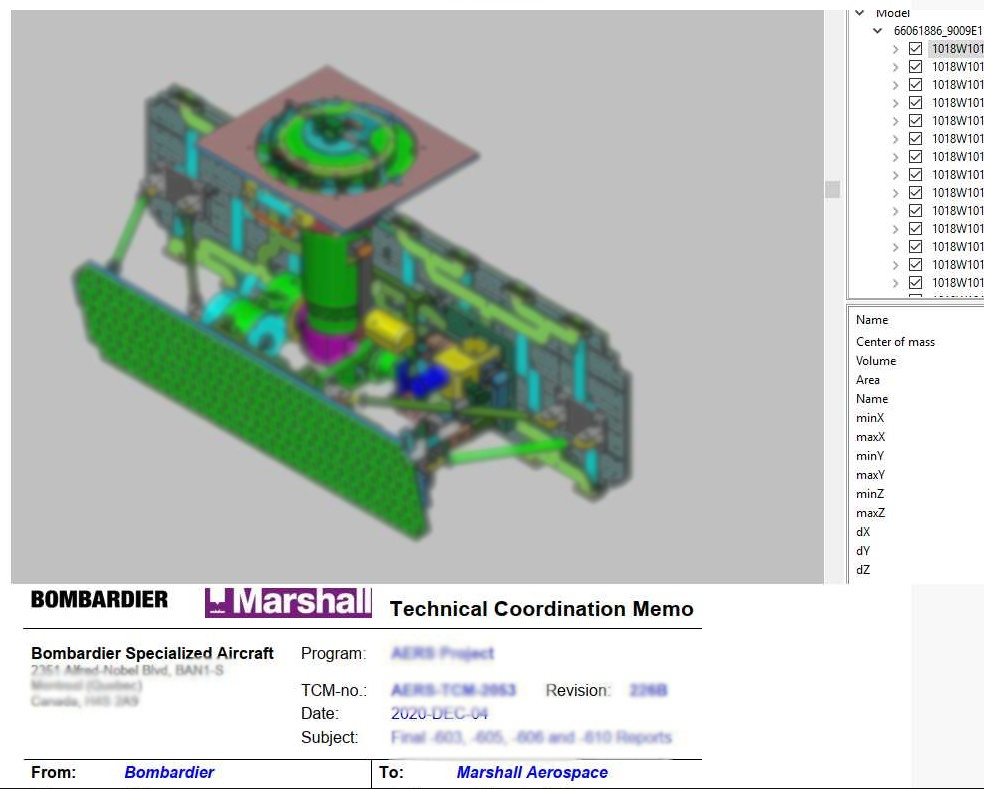
With the help of KELA’s cyber-intelligence tools, we were able to locate the leak and access the sample documents which contained 3D model designs of aircraft fuselage and parts, memos, addendums, and technical reports excerpts. We have blurred a sample for you below, but this is only the beginning for the Clop gang. If Bombardier doesn’t meet their demands, which we don’t expect them to, the actors will soon let out many more pieces of confidential information.
If you are a client, supplier, employee, or stakeholder of Bombardier and you fear the chances of having had your sensitive information accessed by the Clop actors, keep an eye on your inbox. Bombardier has promised to send alerts to everyone that may be potentially affected by this breach. However, this also increases the chances of being approached by scammers, so beware.
The last time we covered news about an incident attributed to the Clop ransomware group was back in April when they hit ExecuPharm and stole the PII and financial details of the pharmaceutical’s employees. However, that doesn’t mean that the actors remained dormant in the meantime. Clop kept targeting high-ranking executives and managers of prominent organizations and copied techniques from other groups that were confirmed to be particularly effective.