Hackers Are Targeting UK Bank Clients With 2FA-Bypassing Toolkits
- At least eight British banks are being impersonated by smishing actors right now.
- The hackers send tricky SMS with URLs leading the phishing sites that ask for the 2FA code.
- The “work from home” wave is helping the malicious actors, and fingerprint-based alerts go unnoticed.
A group of actors who goes by the alias “Kr3pto” is reportedly responsible for a massive smishing campaign targeting UK bank customers in the United Kingdom. According to Akamai, the campaign has been active since at least July 2020 and continues to this day. The hackers use sophisticated tools that feature administrative panels and complete exploit kits that enable them to bypass two-factor authentication steps and take over target accounts.
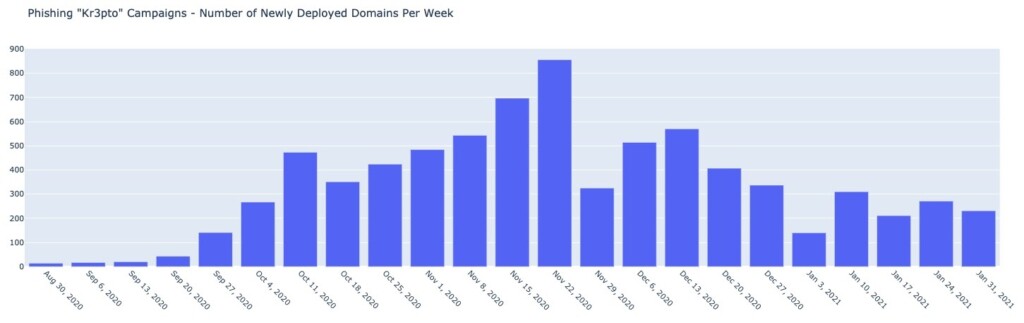
Akamai’s analysts have tracked over 7,600 domains that are being deployed with the Kr3pto kit, abusing eight banking brands by mimicking them for purposes of sensitive data collection. These kits are cracked and recirculated as new packages, some of which use new admin tools.
These campaigns' power lies in their sophistication, and the very fact that they target one-time password (OTP) tokens is indicative of that. They are also a strong reminder that SMS-based 2FA solutions are by no means bulletproof.
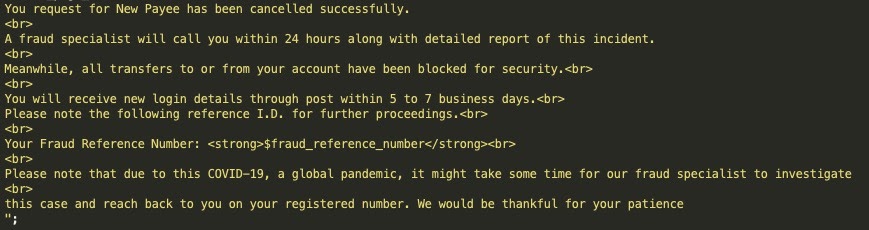
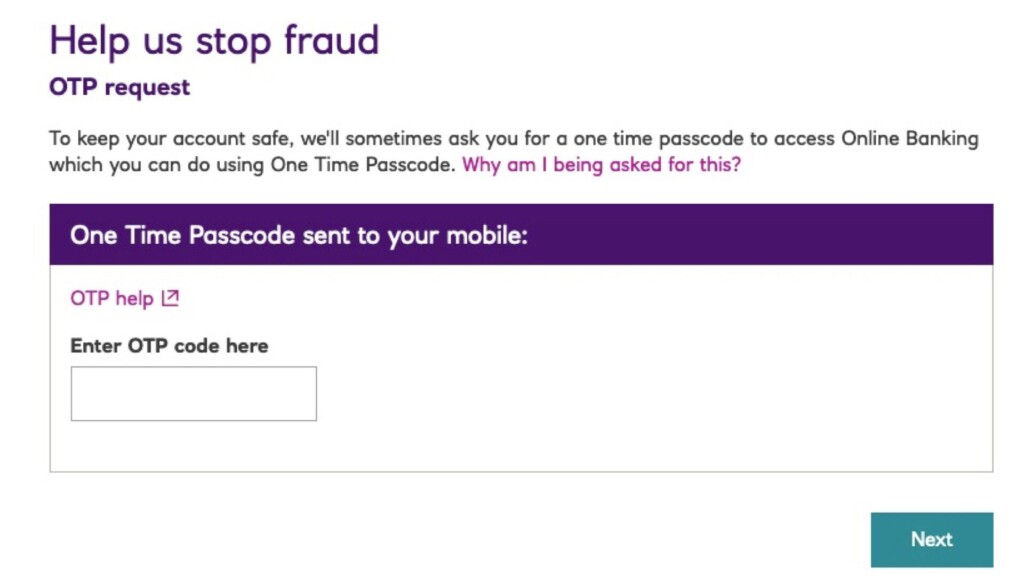
The attack begins with an SMS reception that informs about a problem with the target’s account. There’s a variety in the presented problems, but the recipient is urged to take immediate action in all cases. A URL is provided in the SMS, which takes the victim to the Kr3pto kit’s phishing landing page if tapped.
The OTP trick happens at this stage, which the crooks being prepared to act live. The victim is served a convincing OTP request, he enters the number in the box, and then the hackers log into the real bank platform with the provided credentials and the code.
To do this, they are actively engaging with the victims in real-time and are using the entered details immediately as they come. This shows an amazing level of devotion, but of course, the payout is often big for the actors, so it’s worth the effort.
The banks could identify that something “phishy” is going on if their fingerprinting systems raised alarms - and in some cases, they do. However, because many bank security employees work from home now, such incidents go largely unchecked and often unobstructed. Hackers know that this period is ideal for them to act, and they are giving it their best.
Smishing campaigns in the UK are going rampant. Although the law enforcement authorities have recently uprooted a large player in the field, there are apparently a lot more to identify and stop. If you receive an SMS, keep your sangfroid and don’t follow any links provided in the message. Call the bank and ask for clarifications. Finally, you may want to use a FIDO2 hardware authentication key instead of relying on SMS OTPs.