XLS Attachments Carrying Obfuscated Macros Wreak Havoc onto Email Inboxes
- A duet of French hackers has managed to do well in authoring an obfuscated malware and selling it for profit.
- The two didn’t do equally well in hiding their online identities, making elementary and silly mistakes.
- The researchers who discovered them have now shared all the juicy details with the French police.
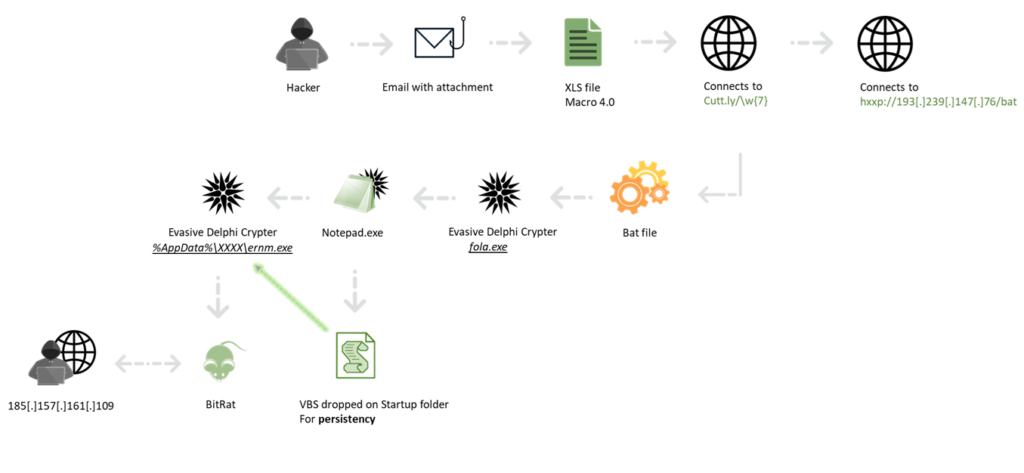
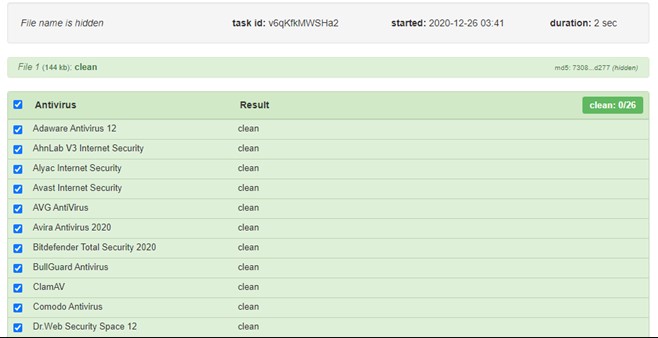
A theme-shifting malware is being actively distributed out there, and according to Check Point researchers, it has already reached at least 80 high-profile customers of the security firm. The malware lands via an XLS document file, which in turn comes as an email attachment. The author of the tool is updating it on a daily basis to evade detection by Windows Defender, and the trick seems to be working well.
The infection starts with a request to enable macros, and if the user approves of it, malicious code runs to fetch a Windows system command script. The document contains obfuscated Macro 4.0, and the downloaded script is a BAT file that’s fetched from cutt.ly, for obfuscation again. The command that’s executed is “attrib,” which basically hides the script onto the victim’s computer.
The email uses various subjects like an inquiry from a biotech company, a royal mail notification, a boat inquiry, random dates, or even Bulgarian phrases. The filenames of the laced XLS documents are tweaked to match the subject. The malware itself is a DelphiCrypter followed by a BitRAT, and as Check Point’s analysts confirmed during their testing, security solutions are missing the threat.
The malware is actually for sale by two users who go by the nicknames “Apocaliptique” and “Nitrix.” According to the Check Point team, it has made the actors about $5,000 in 1.5 months. The list of customers that the researchers managed to retrieve by analyzing the server files enumerates 53 clients. Nitrix is also operating a Discord channel where he claims to be the tool's author, the "APOMacroSploit." On this channel, buyers may find help, advice, and discuss hacking stuff in general.
Check Point investigated these users' identities, as the same persons are hosting the malware on their servers. Apocaliptique even has a pretty unpopular YouTube channel where he demonstrates the malicious tool's power and features, so these people weren't operating carefully enough. The researchers searched some more and found a Skype address that was related to this channel, and by digging into YT comments, they’ve found two ‘League of Legends’ player profiles.
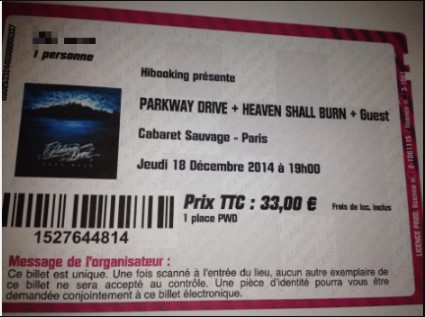
Naively enough, Apocaliptique and Nitrix were using the same usernames for LoL too. This has led to the discovery of the Nitrix Skype account - and eventually, the hacker’s real name. The man actually gave that valuable information away on Twitter by himself, as he posted a concert ticket with his name on it back in December 2014.
This then led to the Facebook account and a real home address in France. We’re sure the man will have a lot of regrets to go through for giving away his own identity for a vanity-satisfying social media presence.
Check Point has already reported the identification details and the C2 IP address to the relevant law enforcement authorities, so the two hackers must already be in the hands of the French police.