‘U-Admin’ Phishing Panel Author Arrested in Ukraine
- The author of a widely used phishing panel named ‘U-Admin’ has been arrested in his home in Ukraine.
- The malicious kit that he sold to hundreds if not thousands of hackers was used in billions of phishing messages.
- The country that led the investigations was Australia, which had a severe problem caused by the particular malware.
The Ukrainian police have arrested the author of a phishing panel tool named ‘U-Admin’ in his home in the city of Ternopil. The 39-year-old was offering his panel and “complete phishing package” to a large number of crooks on various dark web marketplaces, as well as on a dedicated portal.
The hackers then used the tool to target financial institutions in Australia, Spain, the United States, Italy, Chile, the Netherlands, Mexico, France, Switzerland, Germany, and the United Kingdom.
In total, it is estimated that U-Admin was deployed in more than 1.5 billion phishing attacks, incurring tens of millions of USD in financial losses for the targets. Also, the Australian authorities claim that over half of all phishing attacks carried out in the country were relying on the tool created by the Ukrainian hacker.
These admittedly dizzying numbers underline the importance of the arrest. At the same time, the law enforcement authorities claim to have already identified another 200 buyers of the tool during the first round of inspections carried out on the confiscated hardware. Thus, it is very likely that we’ll see more arrests in follow-up operations across the globe.
The arrested man is now facing criminal charges, including unauthorized interference in the work of computers, automated systems, computer networks, or telecommunication networks, and for the creation of malicious software for the purpose of use, distribution, and sale. Based on Ukraine’s Criminal Code, the sanctions would bring penalties of six years of imprisonment or more.
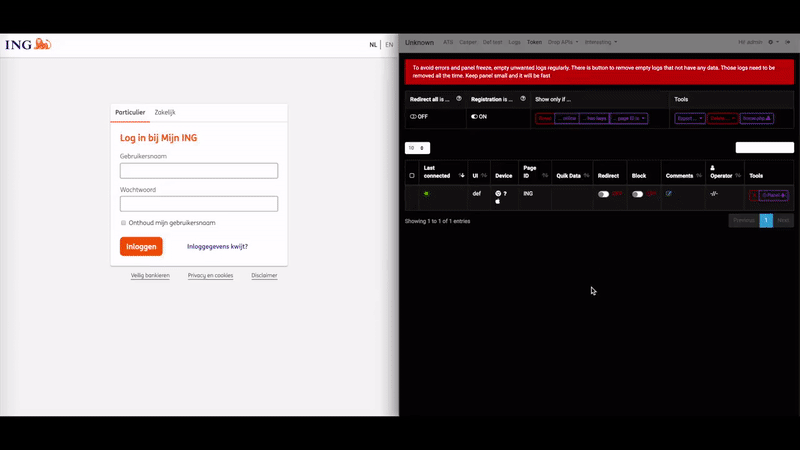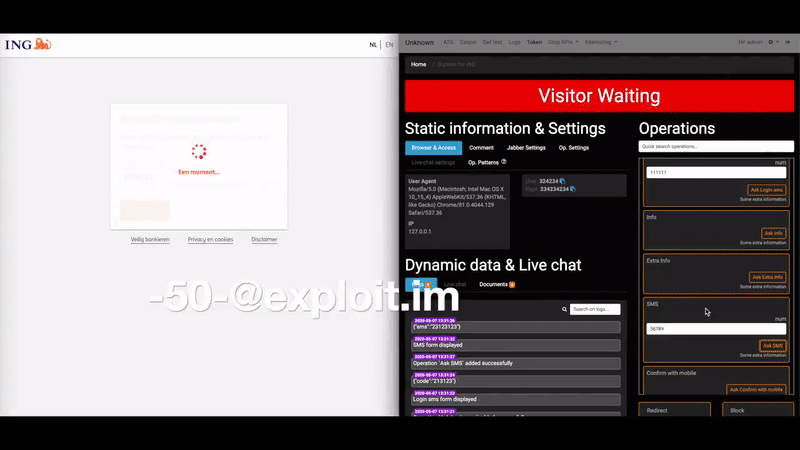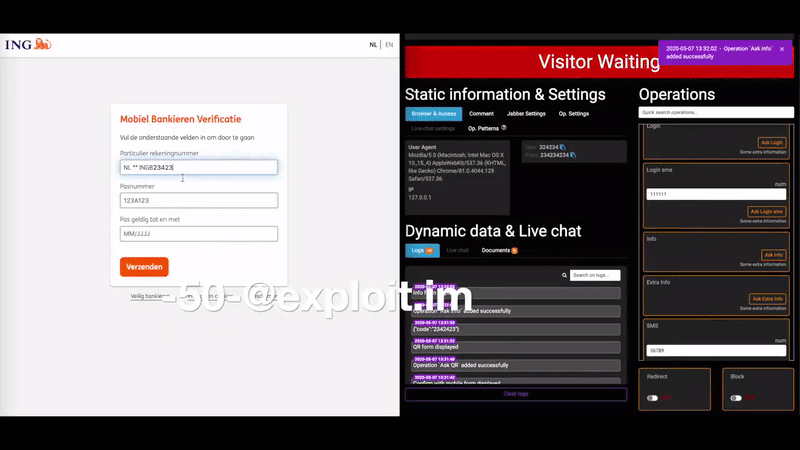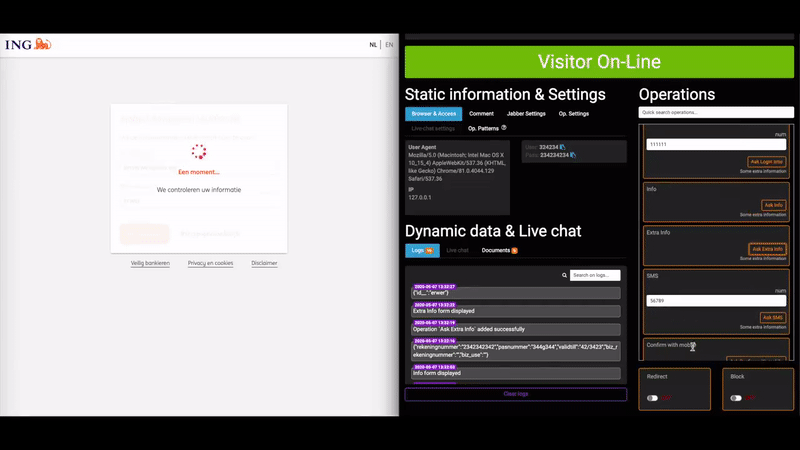
According to Krebs on Security, the biggest selling point for U-Admin is the fact that it can intercept multi-factor authentication codes, enabling the crooks to successfully get through 2FA steps. Also, the “web inject” functionality of the tool made it possible for the phishing actors to interact with their victims in real-time and inject whatever they saw fit each time.
Now that the author of the tool and operator of the project has been arrested, phishing actors have reservations about using the tool. Several discussions between the crooks on the dark web suggest that it should be safe to use the tool since it’s not phoning back anywhere.
However, Brad Marden, the head of operations of the Australian Federal Police, stated that “he wouldn’t be unhappy with the crooks continuing to use that piece of kit,” indicating that they have a way to pinpoint the users. Since the man is involved in the investigations since late 2018, he may know something the kit users don't.