Data Stolen in ‘Promutuel’ Insurance Firm Attack Now Leaking Online
- The first samples of Promutuel data have appeared on the dark web courtesy of the “DoppelPaymer” gang.
- The first set doesn’t contain sensitive client details but sends a clear extortion message to the firm.
- The insurer’s systems are still offline, and it will reportedly take a few more weeks to restore them.
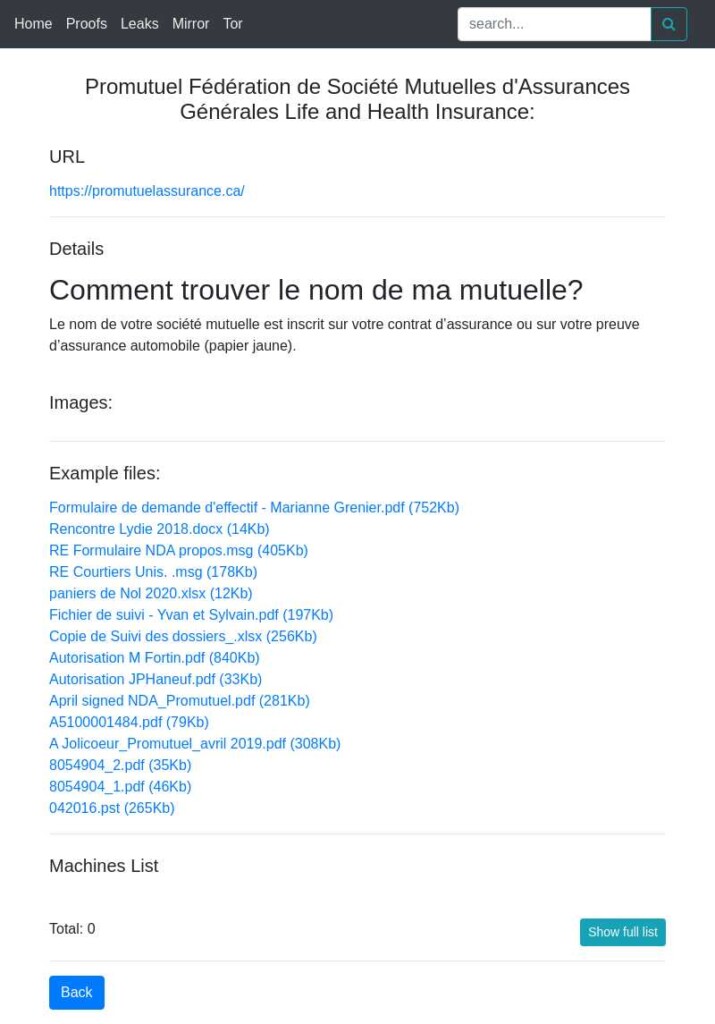
The Quebec-based insurance company ‘Promutuel Assurance’ has recently suffered a ransomware attack, which crippled its systems and prevented its customers from accessing their accounts through the online platform. To complete the catastrophe, the confidential details of some of the company’s customers have now leaked online, as we can confirm with the help of KELA’s dark web crawlers.
This is typical in ransomware incidents where the negotiation for the ransom’s payment doesn’t go the way the threat actors want.
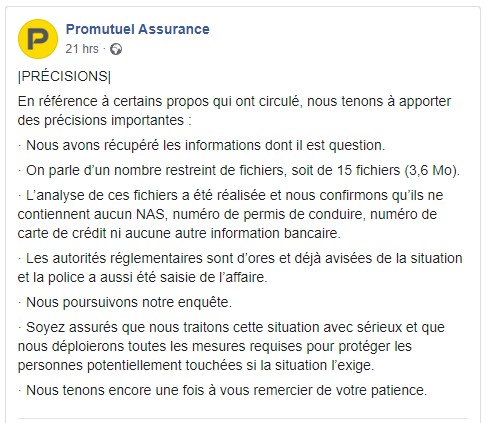
The company, which has around 630,000 customers, played down the data leak, saying that it’s only a set of 15 files that don’t contain any highly sensitive information like social insurance numbers, driver’s licenses, credit card numbers, or any banking information. As a Promutuel agent stated on Facebook, they are continuing the investigation with the help of the regulatory authorities and the Canadian police.
However, this small leak makes it clear that there’s a risk of a much bigger security event as the chances of the actors holding the more sensitive subsets back until the firm pays the ransom are very high. Also, reports of local media outlets accuse Promutuel of denying to share more information about the incident and claim that the customers haven’t received a notification about the possibility of their information being compromised.
Promutuel has made some reassuring statements on “LaPresse,” saying that no amount will be withdrawn from the clients’ bank accounts without first sending a written communication to them at least twenty days in advance. According to the firm, the contractual protections will remain in place even if pre-authorized withdrawals are delayed for a while. As for how long this is expected to take, broker sources have mentioned at least a “few more weeks.”
Finally, although the ransomware group responsible for this incident hasn’t been confirmed, we are seeing evidence of “DoppelPaymer” being involved, as they were the first to release the data on their extortion portal. This is a very capable group of actors who focus on larger targets rather than anything with an open door. Back in November 2020, “DoppelPaymer” compromised the systems of laptop maker ‘Compal,’ asking for a ransom payment of 1,100 Bitcoin for the unlocking key and the deletion of the exfiltrated data.