A Backdoor Account Is Present in 100,000 ‘Zyxel’ Network Equipment Products
- A large number of networking devices from Zyxel are vulnerable to remote exploitation.
- Anyone can ssh into port 443 using cleartext passwords that are stored in the firmware.
- The company planted the backdoor itself by mistake, for auto-updating purposes.
Approximately 100,000 'Zyxel' networking devices such as VPN gateways, AP (access point) controllers, and VPN firewalls, are running a firmware version that’s vulnerable to “CVE-2020-29583” (7.8 high). The particular vulnerability concerns the existence of a backdoor account that has the username “zyfwp” with the unchangeable password “PrOw!aN_fXp”. According to Zyxel’s security advisory, the existence of this account isn’t the result of a supply chain attack, which is so hot these days, as they planted it themselves to deliver automatic firmware updates to connected access points through FTP.
The problem with this admin account's existence is that its password is stored in cleartext form in the firmware, so anyone can remotely ssh on the server or web interface with admin privileges and do what they wish. This possibility was discovered by researcher Niels Teusink who reported it to Zyxel on November 29, 2020. The networking equipment company released a patch on December 24, 2020, but naturally, there are still many devices that haven’t applied it yet.
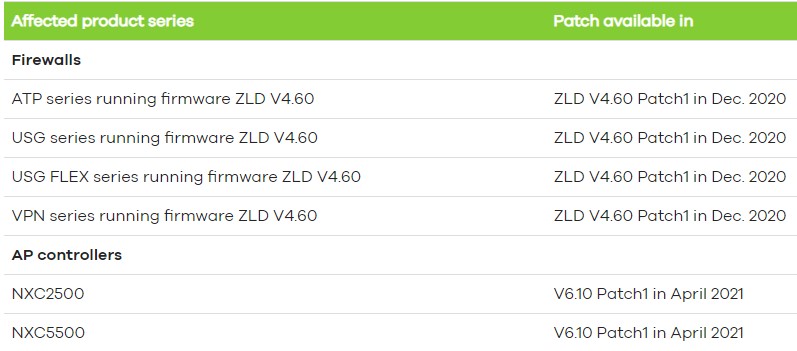
The vulnerable products are all firewalls running firmware version 4.60 and two AP controllers running firmware version 6.10. This includes the ATP series, USG series, USG Flex series, VPN series, the NXC2500, and the NXC550. If you are using one of these products, you should apply the available updates immediately. Unfortunately, the patch for the AP controllers is going to be made available in April 2021, so these products may better be decommissioned until then. Zyxel clarified that firewalls running a firmware version earlier than 4.60 or the SD-OS are not affected by the particular flaw, but using older software is obviously vulnerable to other fixed bugs.
Obviously, the now-published vulnerability has intrigued hackers who are sharing the credentials in a frenzy, looking for still-exploitable products to access. The attacks are very simple to carry out, so hackers of all levels are joining the party. The most capable authors could write botnets to automate scanning and exploiting, and that shouldn’t take long, definitely well before April 2021.
The last time we covered news about Zyxel products, it was about fixing an actively exploited flaw (CVE-2020-9054), which was being sold on the dark web for $20,000. The flaw was on the firmware (5.21), which contained a pre-authentication command injection error enabling hackers to perform RCE attacks on a range of NAS devices.