Emergency Zero-Day Micropatch for Windows 7 and Server 2008 Is Free for All
- A newly discovered privilege escalation zero-day on Windows 7 is forcing wide-spread patching.
- The zero-day is addressed by a micro-patch that is freely available to all users out there.
- Microsoft will soon push a patch through the ESU program, as the closed circle of clients is vulnerable as well.
Even though Windows 7 and Windows Server 2008 R2 are no longer supported by Microsoft, it cannot be ignored by the community when something severe surfaces. After all, there’s still a respectable number of users who are stuck with these older operating system versions for a range of reasons. That said, “0 Patch” is now pushing a fix for a zero-day bug that concerns a local privilege escalation vulnerability affecting the aforementioned OSes.
To be precise, Microsoft offers a special “Extended Security Updates” program for these operating systems, covering a small number of critical clients. The fix for the discovered bug is to land through that program soon.
However, the update will be free for all through the “0 Patch” program, so everyone is covered. All that you’ll have to do in order to get the patch is to register on the platform and grab the micropatch.
The discovery of the zero-day came from Clément Labro, who has published a detailed write-up on his website. As the researcher explains, the discovered flaw affects both those who are covered by the ESU program and those who received their last patch in January, when the support for Windows 7 ended.
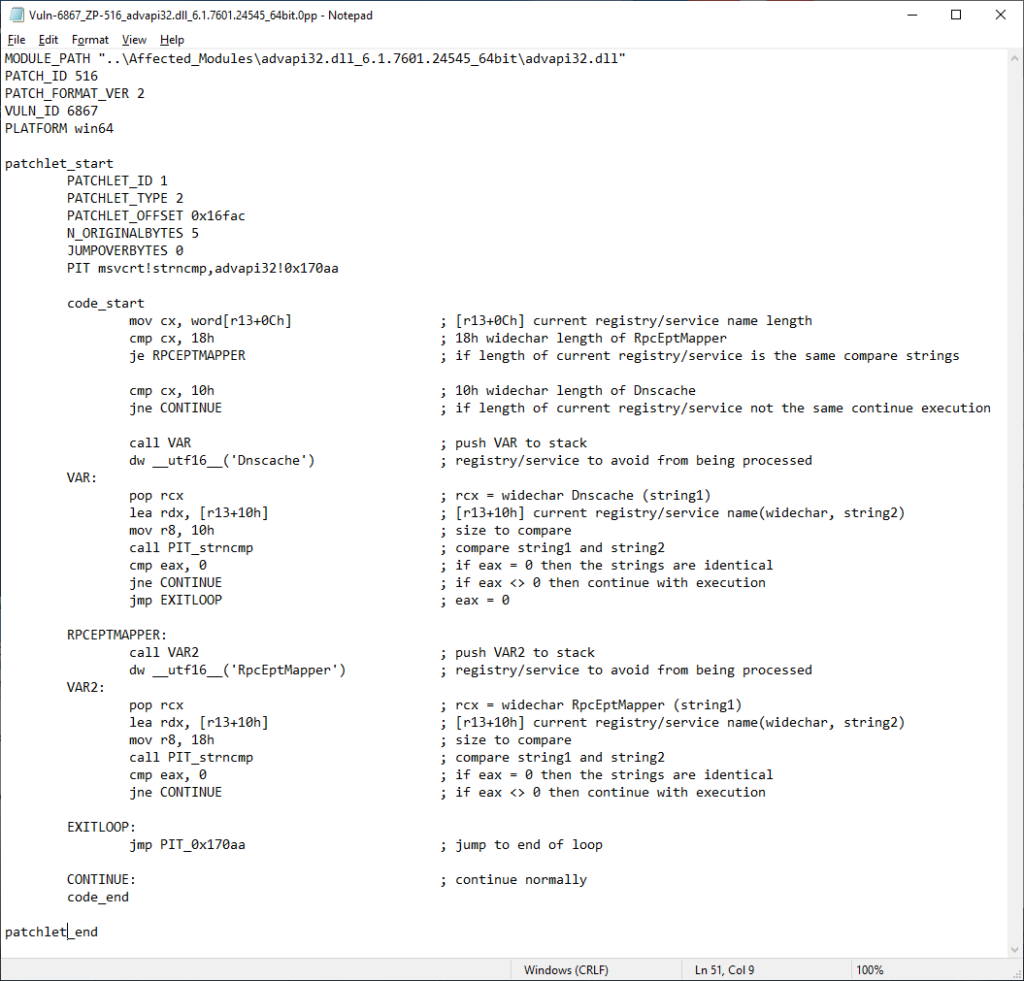
The vulnerability lies in the exploitation of two registry keys by using the Windows Performance Monitoring mechanism to load libraries (DLL) from the privilege of the Local System and not just a local user.
All that an attacker would need is to create a “Performance” subkey in one of the following two keys:
- HKLM\SYSTEM\CurrentControlSet\Services\Dnscache
- HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper
Then, the actor would have to populate the subkey with some values and trigger the performance monitoring, eventually leading to the loading of the DLL and finally to the execution of code. So, in summary, the zero-day bug is a case of incorrect permissions handling.
The fixing micropatch is not making any system-wide changes but instead addresses the problem in the code. Not even a system reboot will be required for the micropatch to be applied, so it’s just a tiny bit that makes a huge difference in security. If you insist on using these older systems, register onto the “0 Patch” platform and keep an eye on the updates and advisories to keep your systems as safe as possible.