Hackers Took Over Telegram Accounts in Israel Through SS7 Attacks
- Actors who knew how to exploit SS7 communication network flaws took over email and IM accounts.
- The targets are high-ranking individuals who are involved in successful cryptocurrency projects.
- There was no financial gain for the hackers, but the breach has happened, highlighting the risks of SS7 flaws once again.
Researchers from Tel-Aviv based ‘Pandora Security’ have discovered a new wave of SS7 attacks that targeted at least twenty subscribers of the ‘Partner Communications Company’ (former ‘Orange Israel’) telecom services provider. The targets are key members of cryptocurrency projects, so they were carefully picked by these hackers.
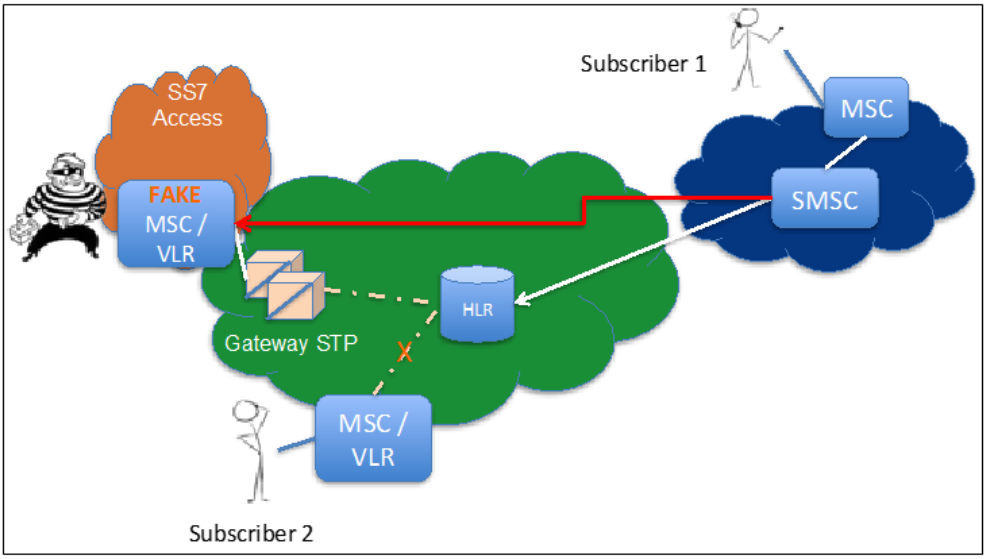
The actors moved by spoofing the short message service center of the network operator and sending an update location request to the target numbers. This resulted in routing all voice calls and SMS messages to the actors, which could be used to get past the 2FA steps.
In several cases, the hackers used the SMS codes to take over their targets’ Telegram accounts, access previous communications, and ask BTC and ETC from their contacts. In others, Gmail and Yahoo mail accounts were targeted. The actors were well prepared as it seems, as they already had the account passwords, possibly from data leaks.
Moreover, they had to know the MSISDN (Mobile Station International Subscriber Directory Number) and the International Mobile Subscriber Identity (IMSI) numbers - otherwise, the SS7 attacks would be practically impossible.
We have presented the risks of SS7 flaws in the past, and we have even analyzed real-world cases of exploiting the system’s intrinsic flaws. Waiting for an SS7 security reassessment that would plug the man-in-the-middle holes shouldn’t be your first choice, though, so setting up a non-SMS 2FA method would be a better way to secure your accounts. For example, use an authentication application or a USB key instead.
That is not to say that exploiting SS7 flaws is easy or simple, as only capable and knowledgeable actors can do that. So, there’s always someone willing to put in the effort if there are good reasons to do it.
In this case, the targets were linked with cryptocurrency projects and were important individuals (CEOs and vice CEOs), so they had credibility and a large circle of contacts that are cryptocurrency holders themselves. Still, though, and according to the researchers who discovered this, none fell for the trap, and so there was no money sent to the hackers.
Earlier reports from Israeli media confirmed that these attacks happened and that the country’s national intelligence and cybersecurity agencies are already investigating them. What has been clarified already is the fact that this is not a flaw in ‘Partner Communications Company’ and that any telecom service provider could have fallen victim to SS7 attacks.