The Ryuk Ransomware Gang Is Surely Not Dead or Replaced by Conti
- The Ryuk group of actors has re-emerged from the shadows, targeting a corporate network with new tricks.
- The hackers demonstrate a shift from botnets to “hands-on” tools like Cobalt Strike and GMER.
- The attack relied on the launch of a sophisticated phishing campaign that served as an entry point.
A couple of weeks ago, we covered the news about a ransomware attack against ‘Universal Health Services,’ which appeared to be the work of Ryuk actors. This was somewhat of a surprise in the field. Many researchers previously believed that a new group named “Conti” had essentially replaced Ryuk, which was largely inactive since the end of 2019. A new report by Sophos confirms that Ryuk isn’t dead and hasn’t been replaced by Conti - they just paused activities for a while, and now they’re back.
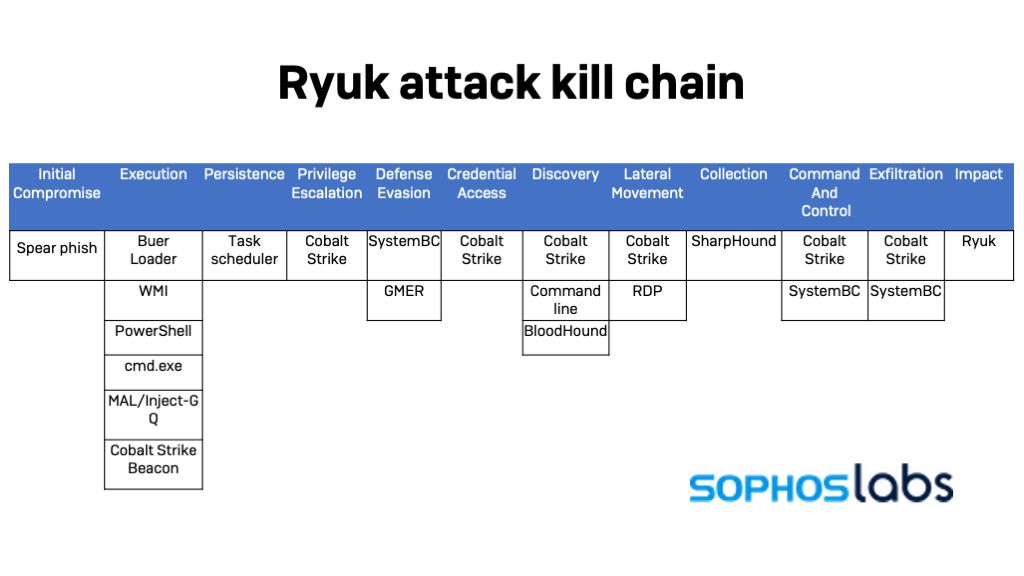
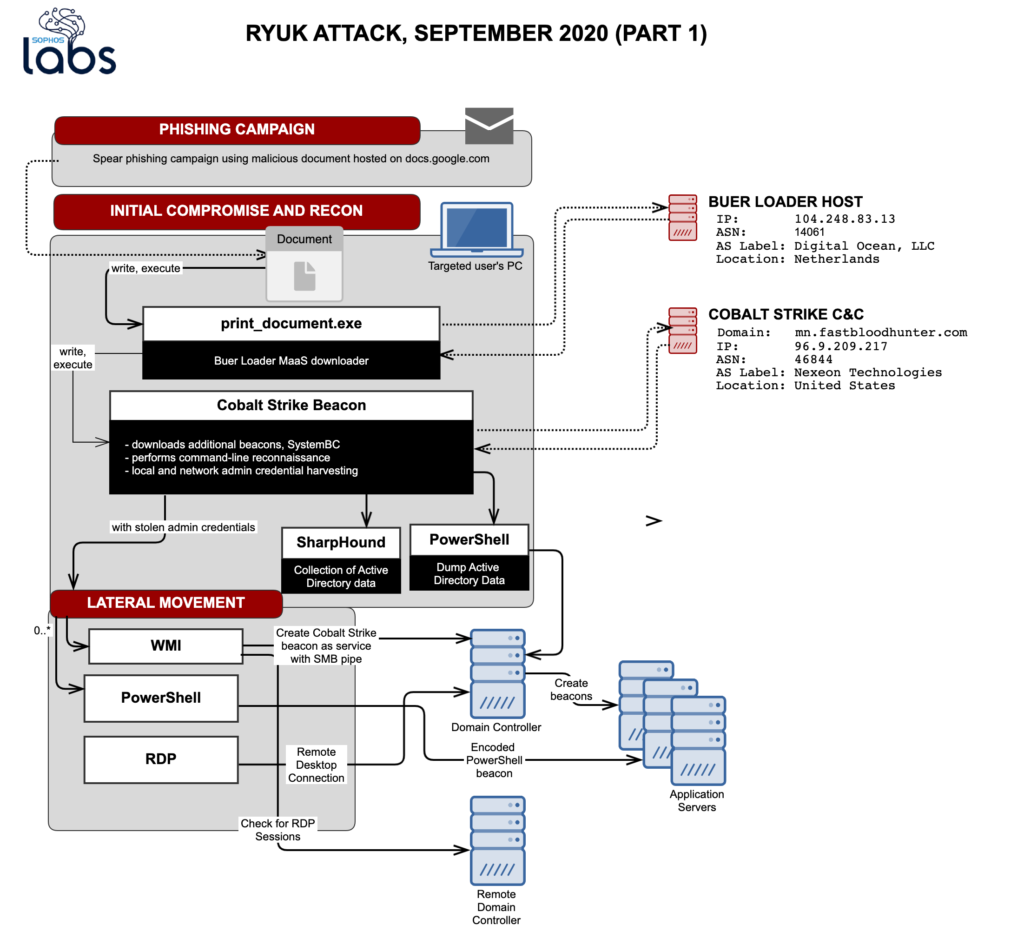
According to the Sophos report, Ryuk has launched a phishing campaign using malicious documents hosted on docs.google.com on September 22, 2020, managed to compromise a large firm’s network, deployed a Cobalt Strike beacon, stole network admin credentials, and proceeded to move laterally on the network.
The phishing messages were quite convincing and highly-targeted, so the actors knew the names of employees working there and had a rough idea of their work methods. The email address of the sender was spoofed to make it look like a legitimate external address, and the topic of the message concerned payroll transactions to create a sense of urgency in the opening of the attachment.
Sophos reports that within half an hour from the deployment of the Cobalt Strike beacon, the actors managed to plant numerous more beacons onto the compromised system, establishing a foothold that created the setting for reconnaissance. The commands that were recorded from then on concern network configuration scans, account data fetching, domain controller checks, etc.
The activation of the ransomware itself was attempted less than a day after the victim clicked on the phishing link that started it all, but only after the reconnaissance procedure had been concluded. The spread of the ransomware binaries was attempted via WMI, RDP clipboard transfers, and file shares. The binary itself was similar to earlier versions, although it featured stronger obfuscation.
Although the actors used GMER to identify and shutdown protection services, and even though they launched the attack from over 40 compromised systems, all attempts were blocked by Sophos Intercept X, and no files were encrypted. Even then, the hackers attempted to activate a SOCKS proxy on the domain controller and kept on trying to drop more Ryuk payloads, deploy Cobalt Strike, and prepare for a second wave. The attack was over only when they were finally ousted from the network.
The recent Ryuk attacks show a shift from using Emotet and Trickbot to Cobalt Strike and GMER. This indicates a more sophisticated, “manual,” and custom approach that makes Ryuk even more dangerous.