“ReVoLTE” Is a New Remote Phone Call Spying Attack
- A new attack against VoLTE calls enables actors to spy on calls by using equipment worth a few thousand USD.
- The attack is based on finding a method to decrypt recorded calls, which is made possible by pallid telco practices.
- The attack will be hard to mitigate, mostly due to practical complexities and its extensive presence.
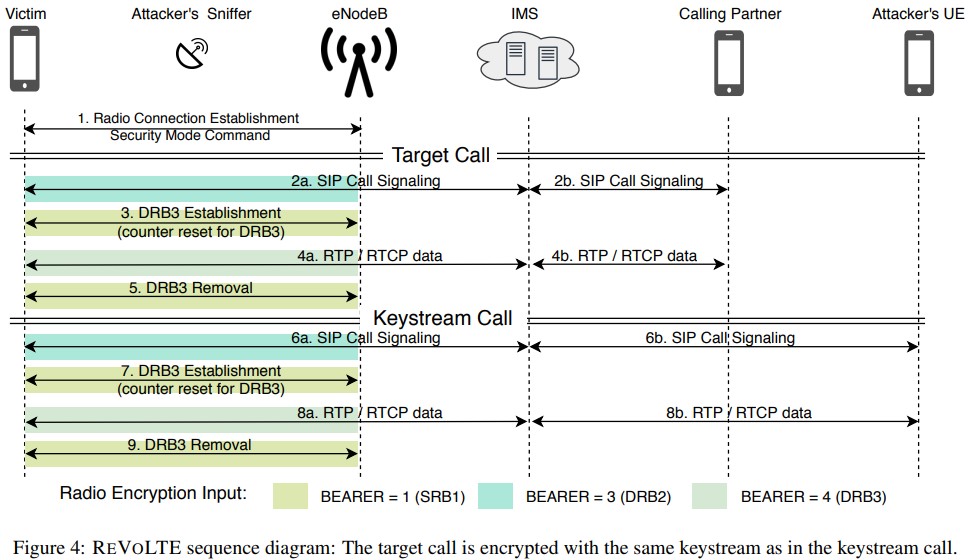
Researchers from the Ruhr Bochum and the NYU Abu Dhabi universities have released the details of a new attack they contrived and named “ReVoLTE.” The attack works remotely and can potentially allow a malicious actor to eavesdrop encrypted LTE calls. ReVoLTE abuses the keystream reuse on the radio layer, essentially making it possible for the attacker to decrypt a recorded call without having to use highly sophisticated tools or very expensive equipment.
VoLTE is supported by over 120 telecommunication providers and 1200 device types worldwide, so the gravity of this report is substantial.
For the attack to work, the actor will first need to record the target during a call, which will be encrypted. This will give the actor the chance to extract the keystream by XOR-ing the sniffed traffic - needed for the subsequent decryption.
The equipment that enables the attacker to sniff radio-layer transmissions in the downlink direction would cost about $1,400. The user-plane encryption key is not reset before 10 seconds pass (for most providers), so within this time, the actor must call the target and record the conversation data in plaintext for the derivation of the key.
There are some prerequisites for this to work, like ensuring that the second call is longer than the first one to enable the decryption of all frames (the entire conversation). Apart from that, there’s the total cost of the ReVoLTE setup, which would be about $7,000, according to the researchers.
This is not a problematic cost for serious actors, but at the same time, it filters out anyone who doesn’t have compelling motives to launch this kind of attack. Also, there’s the practical difficulty of knowing when the victim is on a call; otherwise, you wouldn’t be able to record it. Finally, the attacker needs to be connected to the same base station as the victim during the eavesdropping.
The team has shared their findings with the GSMA, and hopefully, most of the vulnerable base stations will now be secured. Of course, fixing this around the world and expecting all telcos to act quickly and responsibly will be very unrealistic.
The researchers suggest various countermeasures against ReVoLTE, like using different radio bearer identities, implementing intra-cell handover, and more. Some short-term defensive measures could cause latency and obsolete overhead for VoLTE calls, so the definitive solution would be to specify mandatory media encryption and integrity protection for this particular communication technology.