Iranian Hackers “ITG18” Exposed Themselves Through Misconfiguration
- Iranian hackers exposed themselves after they failed to secure a server holding their videos.
- The videos demonstrate how to steal email accounts and how to move laterally without raising alarms.
- The hackers even showcased access to the accounts of American and Greek Navy officers.
The Iranian group of hackers known as “ITG18” has exposed itself after misconfiguring a server holding more than 40 GB of data that can be linked to recent attacks to pharmaceutical companies.
The group has ties with the “Charming Kitten” and “Phosphorus,” so the exposure will be a treasure in the hands of white-hat hackers. The discovery of the data came from IBM X-Force IRIS, who had the change to look into very revealing cyber-crime training and hacking demonstration videos, among other stuff.
Related: Microsoft Seizes “Thallium” Domains and Sues the North Korean Hackers
Source: IBM
The ITG18 has been active since at least 2013, engaging in a wide range of cyber-crime operations like phishing campaigns, credential harvesting, email compromise, government-level espionage, and more.
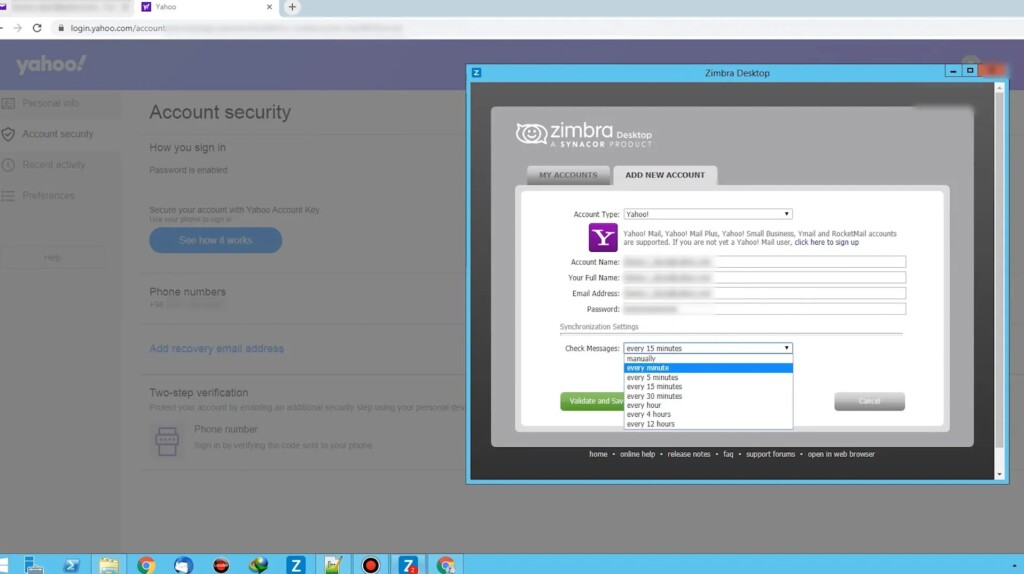
In the training videos found in the exposed server, the hackers demonstrate how to compromise email accounts depending on the target’s service, how to exfiltrate sensitive data, and how to use cloud storage solutions without raising flags or alarms. Other videos explained how to abuse “Zimbra” to send out thousands of phishing emails to targeted organizations.
Source: IBM
Apart from the training videos, there were also “hands-on” videos of successful attacks in the database. One example concerns the compromise of accounts belonging to the United States Navy.
Another one involves an officer of the Hellenic (Greek) Navy, with the actors moving to steal data associated with Greek universities and payroll sites for the Navy personnel. USA and Greece are NATO members and strategic allies, and when it comes to naval operations, the two countries co-operate the “Souda Bay” base in Crete. Iran would obviously be very interested in accessing information relating to NATO’s Eastern Mediterranean operations.
Another crucial detail in IBM’s report is that when the actors faced a multifactor authentication wall, they just skipped the target and moved to the next set of credentials they had in their hands.
Hackers generally don’t bother to spend much time trying to break through properly secured accounts unless these belong to high-profile targets. Even with valuable targets, hackers just opted to hop to less secured accounts and dig their way through there.
All that said, the way to protect yourself becomes pretty obvious, and it would surely include setting up MFA. Resetting your password periodically and using strong, unique passphrases should also be a solid method to help you fend off hackers.
Finally, limiting your email account access to all third-party apps would make it harder for the hackers to use your account as a stepping stone to compromise more accounts in the same network, so make sure to review the relevant settings.